The tool:
SmartDump - an exception and memory dump capture utility (github.com) - https://github.com/microsoft/SmartDump
Current Release v1.02 beta · microsoft/SmartDump
How to use:
1. First of all, we need to open Kudu console and drag/upload the tool into the site folder.
2. Next, we need to find the PID of our LogicApp site’s w3wp.exe from Process Explorer.
NOTE: the one with (scm) is for Kudu console. Hence we always have to focus on w3wp.exe without (scm).
3. Then we can run SmartDump.exe and use -p option to specify the PID found in step #2.
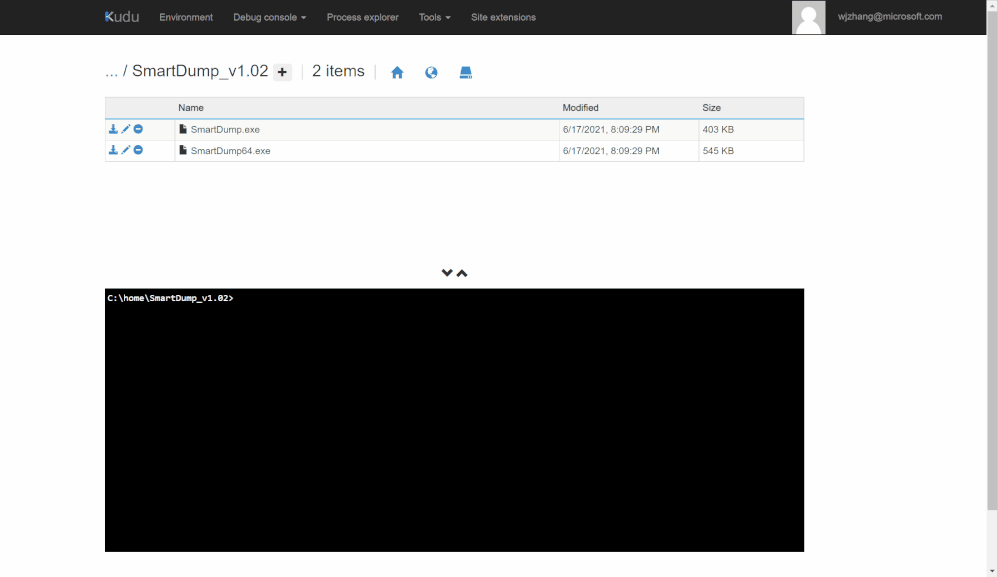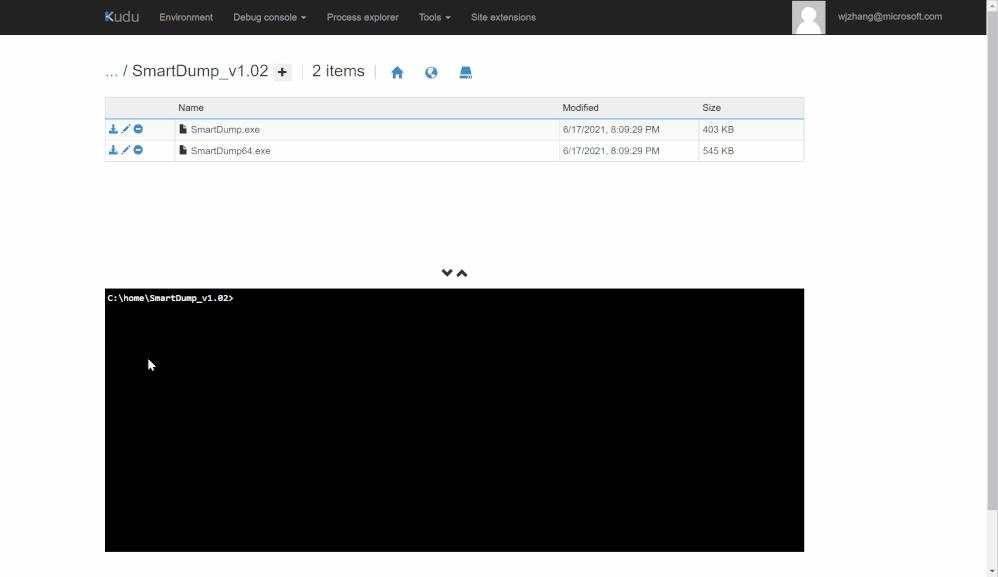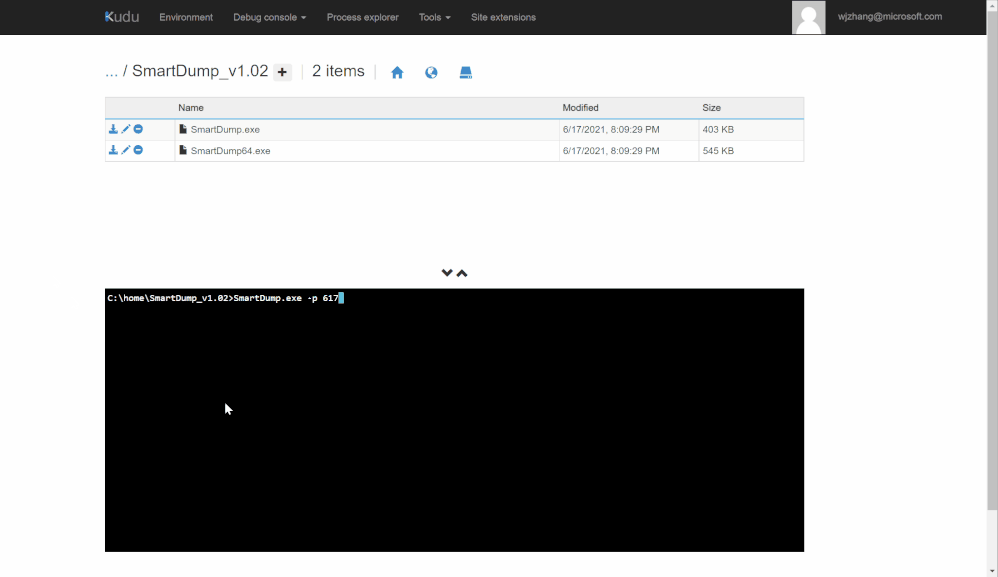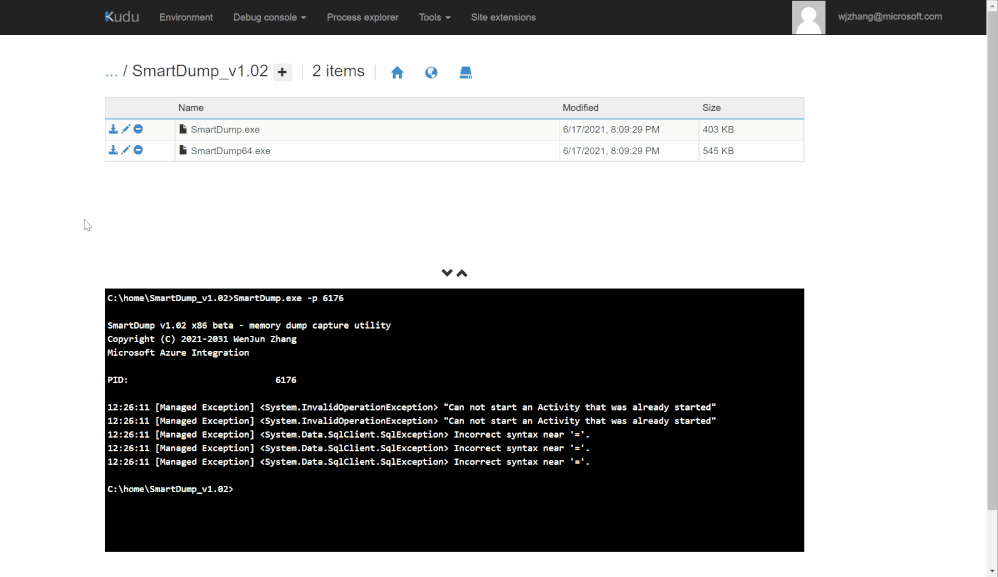
This makes SmartDump attach to the target process and start to monitor any exception thrown in it. By default, the tool captures 5 exceptions.
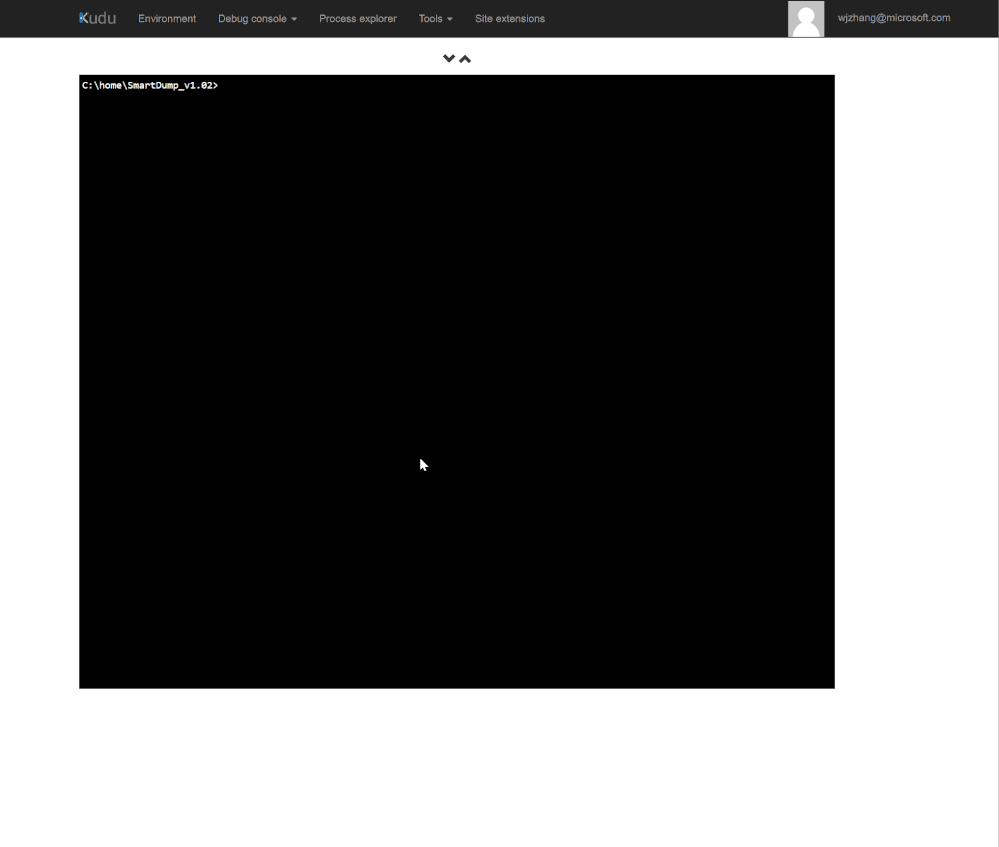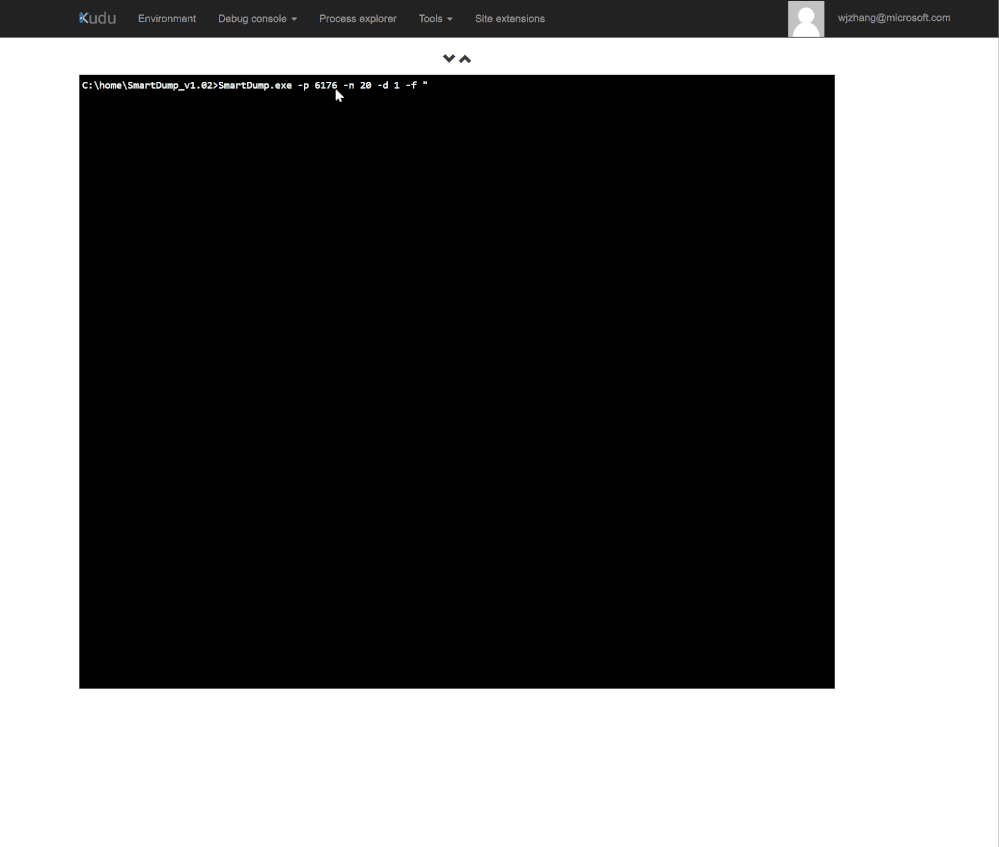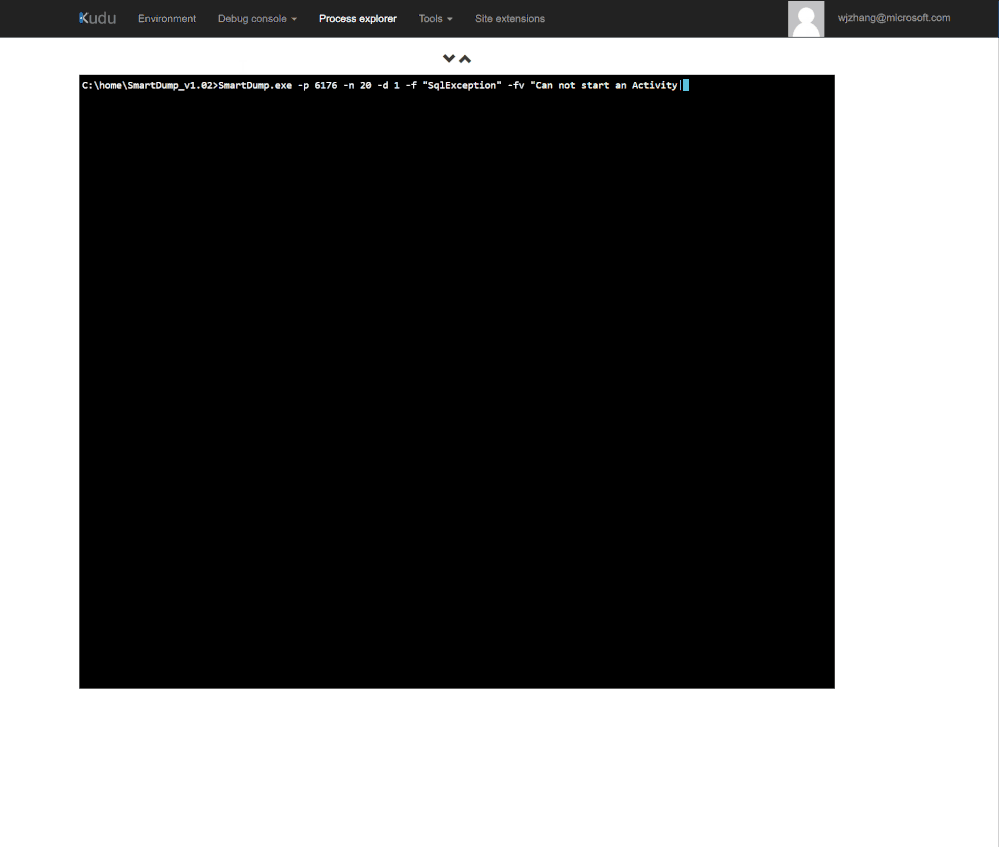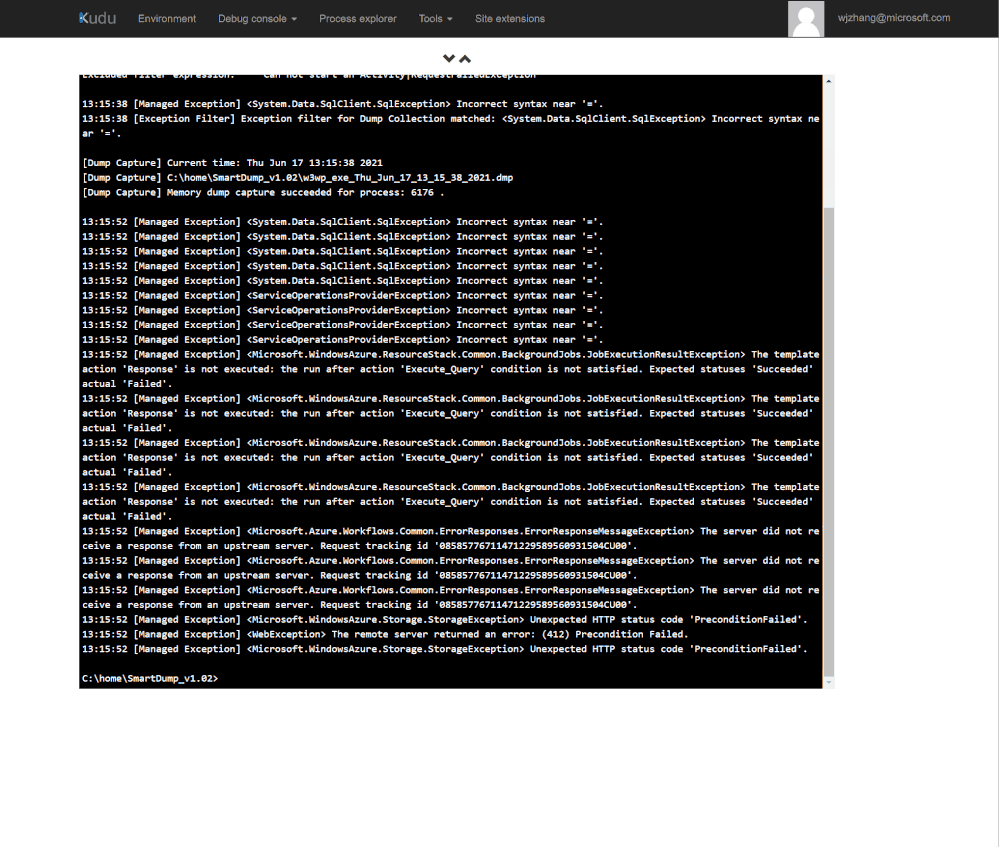
After invoke LogicApp and generate some exceptions, SmartDump will be able to capture them within the console.
4. If you want to see more exceptions, just use -n option to specify number of exceptions to be captured.
NOTE: using -n 0 to start an unlimited/endless capture. However please be careful to use this in Kudu because it doesn’t support Ctrl+C to exit a process. Run inside a common cmd.exe without such issue.
Tips: you can also add: > filename.log at the end of a command to make Kudu write output into a log file for you.
5. To generate dump, use -d option to set number of dumps to be captured. Associating it with -f(filter include) and -fv (filter exclude) options allow you to capture dumps against specific exceptions.
-f Filter exception based on specified string(s). Use '|' as delimiter for multiple strings.
-fv Exclude exceptions contain specified filter. Use '|' as delimiter for multiple strings.
6. The tool also supports to set memory address of breakpoint to generate dump files.
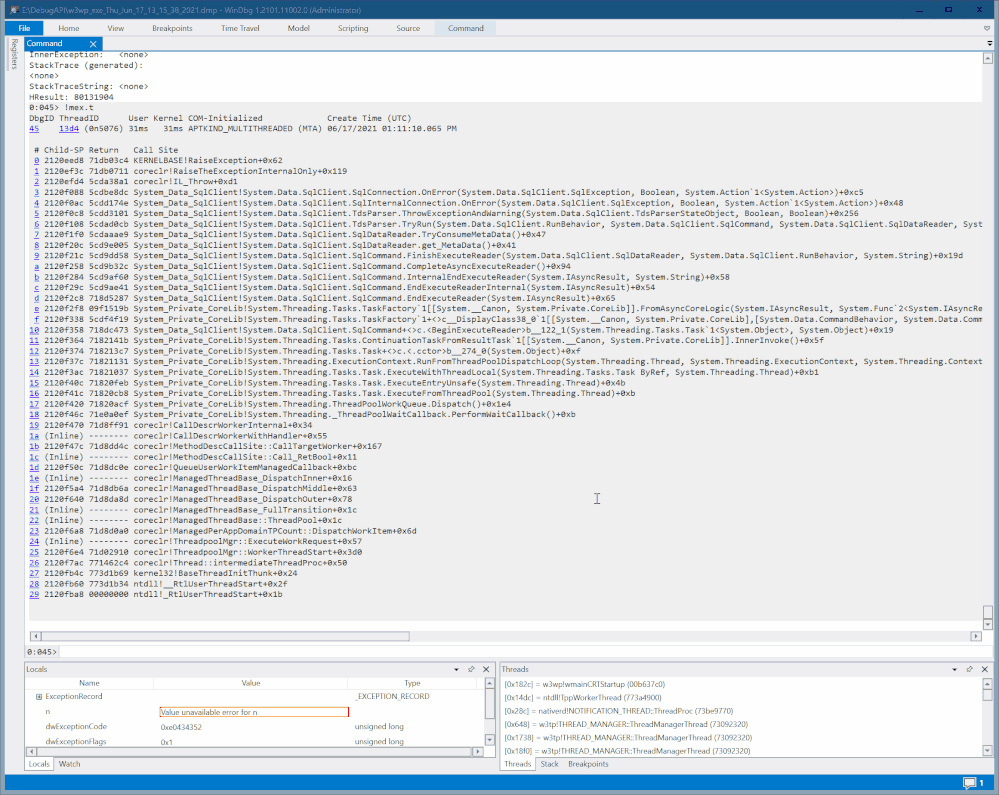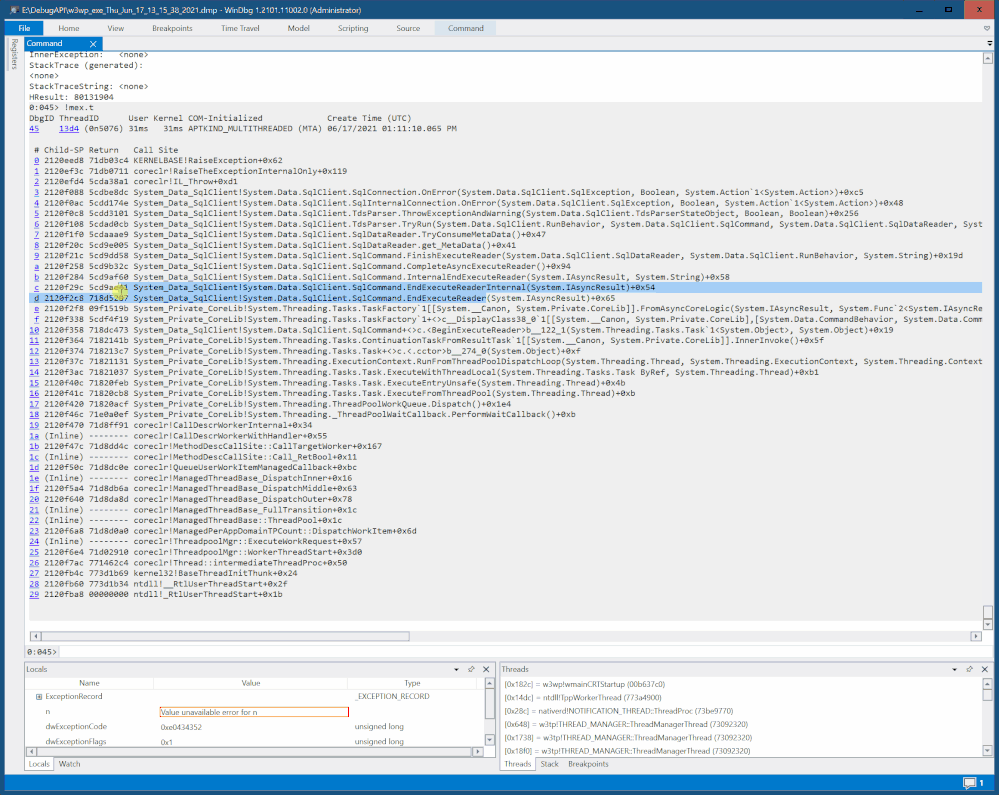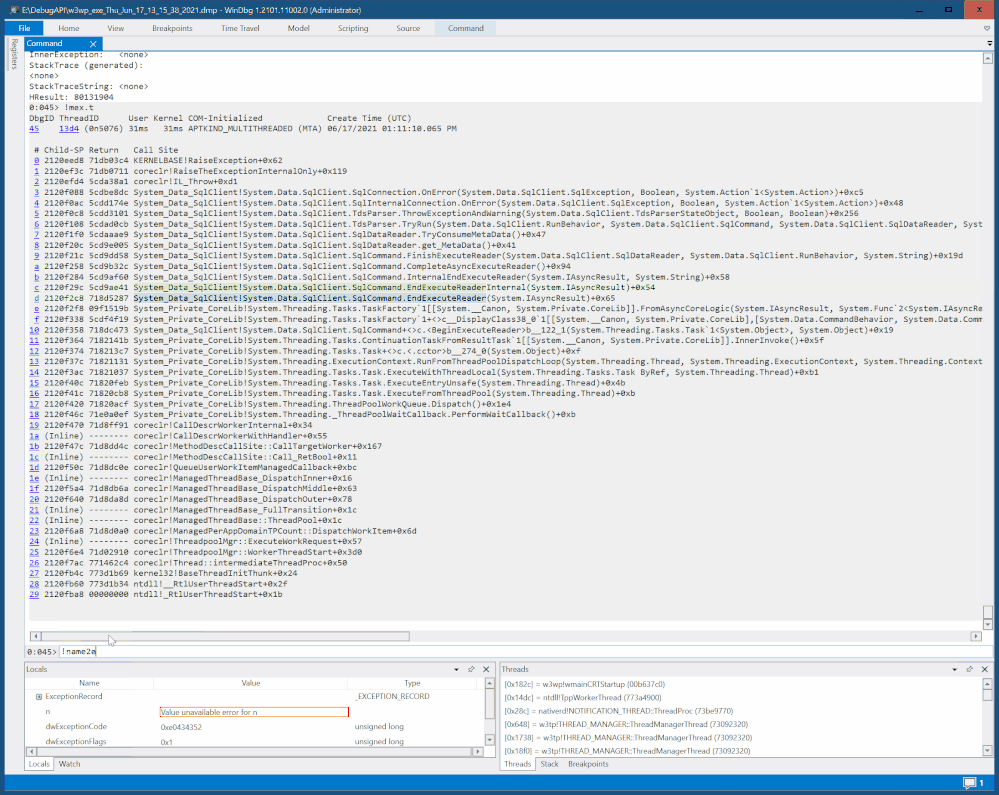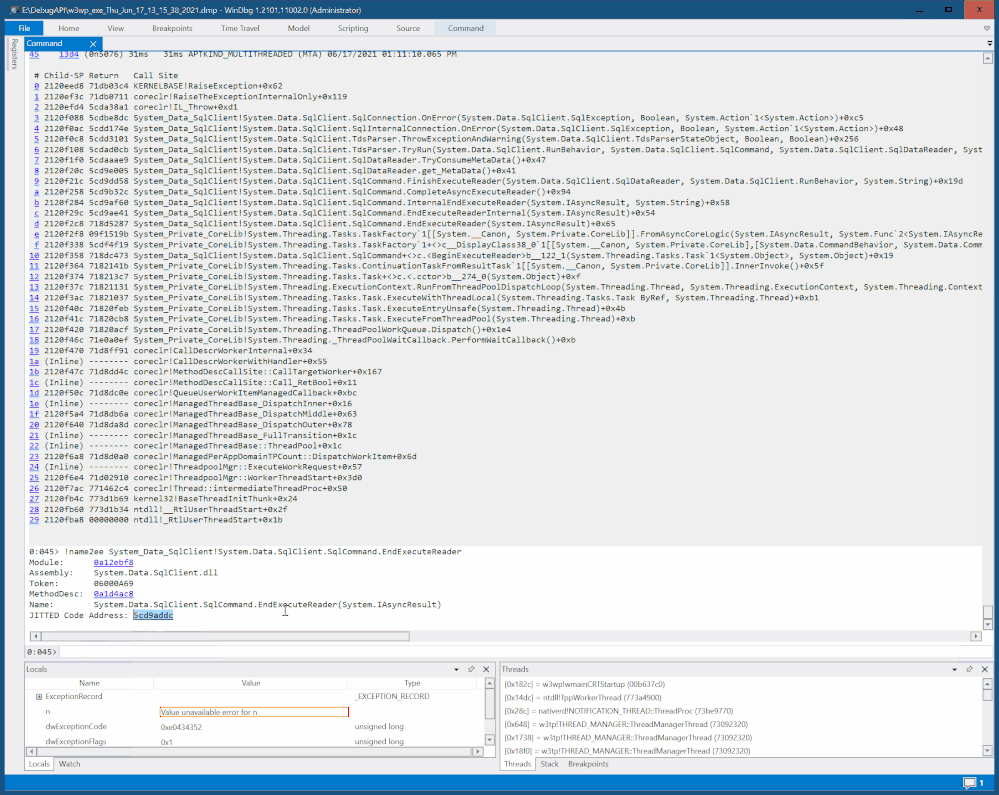
You can capture a dump first and then open it in debugger to find the code entry address of a function you interest in(or code address of any line).
Then use -a option of SmartDump to set the address as breakpoint for capture:
There are also some other useful options and sample commands can be found in the readme of GitHub page: SmartDump
Posted at https://sl.advdat.com/3iPYnVM