Most enterprises rely on a multitude of vendors, security solutions, and IT tools to combat advanced cyber-attacks. At Microsoft, we believe that when these solutions work well together, customers benefit and can build stronger defenses.
That’s why we are excited to announce the general availability of a new integration between Microsoft threat and vulnerability management and ServiceNow Vulnerability Response (VR). The integration between these two products gives customers more flexibility in managing the end- to-end workflow of their vulnerability management program and aims to:
- Optimize vulnerability prioritization
- Automate response workflows
- Speed up overall time to remediation
ServiceNow’s VR module ingests asset information, data of open and fixed vulnerabilities, as well as recommendations from Microsoft threat and vulnerability management. It syncs these findings into VR tables and data structures, where vulnerabilities are matched against existing assets in your CMDB or creates a new Configuration Item (CI) if no match is found. The integration leverages standard Vulnerability Response data import and CI reconciliation methods.

The diagram above shows the import of vulnerability assessment content from Microsoft threat and vulnerability management into ServiceNow VR to orchestrate the remediation workflow of vulnerabilities.
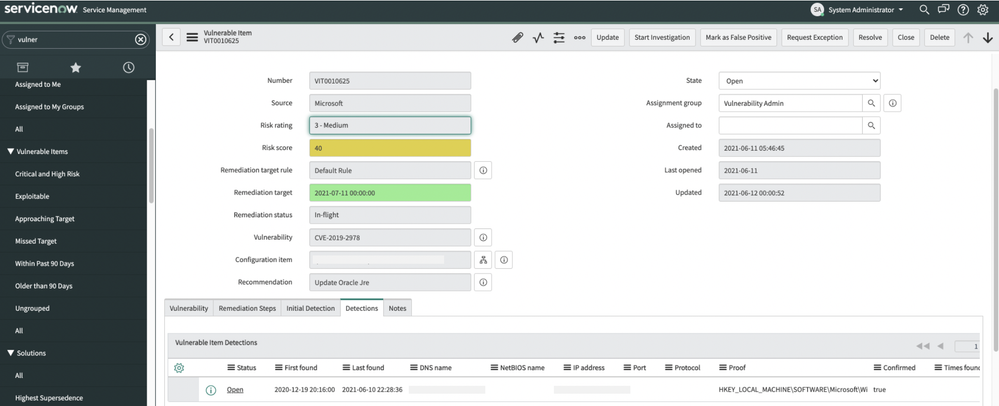
Once ServiceNow VR has ingested information from Microsoft threat and vulnerability management, security teams can start with a top-level view of the ingested data or dive deep using various views. Some of the available views include vulnerability groups, vulnerable items, and security recommendations taken directly from Microsoft threat and vulnerability management.

Image 2 shows an all-up integration run status and details of how much data has been ingested over the last 30 days. The included timeline shows performance metrics over the same period.


As part of the remediation workflow, ServiceNow VR prioritizes vulnerabilities using asset and business context, along with vulnerability risk scores. The risk score and rating take the vulnerability information and configuration item into account. Security teams can customize the risk calculator based on their organization’s preferences and requirements, optimizing the prioritization of vulnerabilities.
Users can then investigate each vulnerability and associated details within the ServiceNow console.
Lastly, ServiceNow VR provides a grouping of vulnerabilities based on the Microsoft recommendations and automatically assigns tickets to the relevant IT owners and sets the SLAs using predefined rules. This enables customers to use existing workflows and established processes in their organization and create an end-to-end process across the vulnerability management program.
The integration between Microsoft threat and vulnerability management and ServiceNow VR can help security teams create more automated remediation workflows and drive efficiencies with their IT counterparts.
An added focus on interoperability
Microsoft threat and vulnerability management APIs empower security teams to deliver greater value to their vulnerability management program. The set of APIs that was used to build the ServiceNow integration gives customers and partners full access to the threat and vulnerability management dataset, including:
- Vulnerability assessment
- Security configuration assessment
- Software inventory for all devices
If you want to know how to use these APIs to create custom reports, build automations, and more, check out this blog post.
As we continue to expand the depth and breadth of Microsoft’s vulnerability management capabilities, our team is focused on building a broad ecosystem of integration partners. We understand that our customers have existing investments and established processes to run their security and IT operations and we want to ensure our products support these requirements. If you would like to see additional integrations within Microsoft Defender for Endpoint, go to the Partner Application page in the Microsoft Defender Security Center, and click Recommend other partners.
More information and feedback
- The threat and vulnerability management capabilities are part of Microsoft Defender for Endpoint and enable organizations to effectively identify, assess, and remediate endpoint weaknesses to reduce organizational risk.
- Check out the step-by-step guide on how to setup and use the integration.
- Get the integration in the ServiceNow store.
- We want to hear from you! If you have any suggestions, questions, or comments, please visit us on our Tech Community page.