This month, we’re releasing new productivity and security capabilities within Microsoft Endpoint Manager. You can view the complete list of What’s New in the 2106 (June) release for details. The three capabilities I highlight this month improve the experience for users and provide more flexibility and management options for organizations that support Android deployments. As usual, I appreciate your feedback. Comment on this post, connect with me on LinkedIn, or tag me @RamyaChitrakar on Twitter.
Improving security and productivity without compromising privacy on corporate-owned Android devices
Many IT organizations allow employees to use corporate-owned devices for some personal tasks to improve productivity so they won’t have to switch between devices. Because of this, organizations must make sure corporate devices are secure and managed while employees want to ensure their personal data and information remains private.
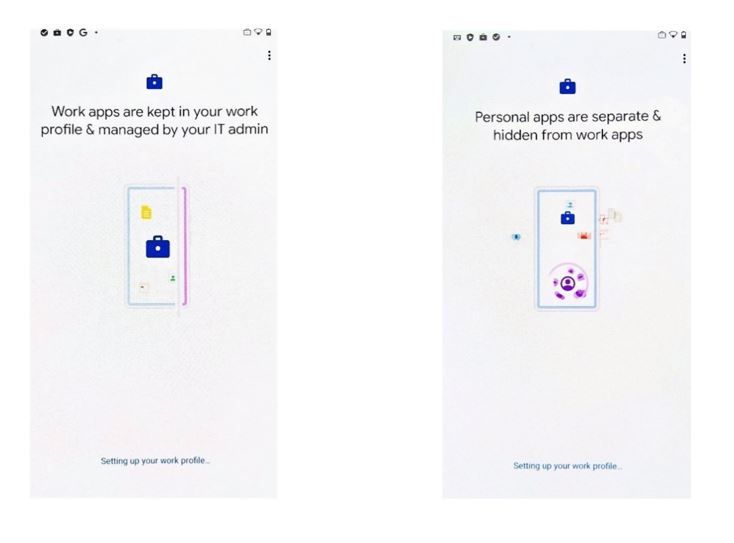
Enrollment with Android Enterprise corporate-owned devices with a work profile enables separation between corporate and personal applications, data, and settings. This month, we’re announcing general availability for management of Android Enterprise corporate-owned devices with a work profile in Endpoint Manager.
While many customers provided feedback on managing corporate-owned work profile devices during our public preview, several asked how to add this option to their portfolio in Endpoint Manager. Follow these steps to get started:
- Assess the Android devices in your environment. Are these devices mostly personally owned (BYOD) or company owned? Any task-specific devices? Review what you have today and foresee the needs of your organization.
- Review your security strategy. With Endpoint Manager, you can secure and manage all your endpoints, managed or unmanaged, corporate, or BYOD. You can protect work data with or without device enrollment. For example, your security strategy for kiosks in a public space will likely be different from that of an information worker in a corporate office.
- Evaluate the device enrollment strategy for each Android platform. There’s a great guide in docs on detailed manageability options – this just highlights the management options.
- BYOD: Personally owned devices with an Android Enterprise work profile.
- COBO: Corporate Owned, Business-use Only - Android Enterprise Fully managed device – Company owned devices fully managed and configured for business use only.
- COPE: Corp-Owned, Personally-Enabled – Enable corporate-owned devices with a work profile; this is what we’ve announced general availability for this month.
- COSU: Corp Owned, Single Use - Android Enterprise dedicated device – Corporate owned devices, managed and configured for a single, dedicated purpose such as a kiosk.
- DA: Device Administrator – Google has reduced support for the APIs on this platform; this type of management will be best suited for areas where Google services are not available or where the device type supports Device Administrator and not Android Enterprise.
- Provided you determine Android Enterprise corporate-owned work profile has a role in your environment, set policies to meet your organizational compliance requirements, such as assign certificates, or configure Wi-Fi or VPN. Keep in mind if you want to move to this device enrollment strategy, say from an Android Enterprise fully managed device, you’ll need to factory reset the devices.
- Deploy apps and utilize app configuration and app protection policies. You can configure these specifically for each platform.
The following screenshots show some of the screens in the enrollment workflow for Android Enterprise corporate-owned devices with a work profile – this is where we demonstrate the separation of work from personal apps.
Simplifying mobile security and preventing security breaches
The need to prevent security breaches within an organization is a priority for many of our customers as employees access work data from all their devices, and these days, from virtually anywhere. Organizations need to secure not only the data at rest and in transit but also the devices themselves. This month, the client app that integrates Microsoft Tunnel into Microsoft Defender for Endpoint moved from public preview to general availability on Android.
What is Microsoft Defender for Endpoint with Tunnel? It’s a secure, VPN connection for managed devices. Employees can download the Defender for Endpoint app on their Android mobile device to get a more holistic mobile threat defense solution that enables secure and productive remote work and is fully configurable from Endpoint Manager.
How do you get started? Here’s a very brief but prescriptive approach.
- Evaluate your strategy as it relates to VPN and endpoint security. Are you already using a VPN provider? If not, what are your organization's specific VPN needs? Consider your requirements and validate Defender for Endpoint meets those needs with Microsoft Tunnel. The capabilities built into the new client app were based on customer feedback so let me know if there's a capability missing.
- Assess your networking architecture and potential security weaknesses as it relates to corporate data access from Android devices. Do you want to allow data access through a more secure connection?
- Confirm if you are already using Defender for Endpoint and Endpoint Manager. Are your Android devices enrolled? If so, move forward with implementing the Microsoft Tunnel Gateway by following the documentation here.
- Once implemented, manage Microsoft Tunnel and Defender through Endpoint Manager just as you manage your other policies. Users just have one app to download from the Google Play store, which improves productivity.
Here’s a video of the user experience:
If you would like a bit more of the engineering backstory, I provided additional insight on our One Microsoft Approach Tunnel and Defender for Endpoint out on LinkedIn.
Making it easier to apply settings on different device types with filters
Filters let you maximize your current asset investments while protecting data on personal, company-owned, and shared devices. The settings catalog makes it easier to customize, set, and manage device and user policy settings. This month - we combined the two! Now, you can have a settings profile and then use filters when assigning it!
In addition, this month we have also deepened our investment in both filters and settings catalog by adding support for the Enrollment Profile Name property in filters for Android Enterprise. Use filters to target devices based on different properties, such as device name and manufacturer.
Last month, I shared what filters and settings catalog enables you to achieve. This month, I’d like to share more about our motivation to integrate these capabilities. Here’s what one of our customers specifically requested – just two examples of why we did this integration:
- Use filters in compliance policies, if for example, you have different compliance policies for Windows HoloLens devices than you do for Windows desktop endpoints.
- Use applicability rules in the settings catalog, in the event you have different configuration profiles for Windows HoloLens devices than you do for Windows desktop endpoints.
We keep our customers’ needs top of mind and invest in areas that improve the user experience and simplify IT administration. Questions? Feedback? Comment on this post, connect with me on LinkedIn, or tag me @RamyaChitrakar on Twitter.
Posted at https://sl.advdat.com/3gOGvZL