Introduction
This article is a continuation of Azure Defender PoC Series which provides you guidelines on how to perform a proof of concept for a specific Azure Defender plan. For a more holistic approach where you need to validate Azure Security Center and Azure Defender, please read How to Effectively Perform an Azure Security Center PoC article.
Azure Defender provides advanced threat detection and security alerts for all kinds of workloads, like Virtual Machines, SQL databases, Storage, Containers, Kubernetes, Key Vault, Web applications, Open-source relational databases. Recently we expanded the protection to two new plans, Azure Defender for DNS and ARM with the help of which you can enhance the resiliency against attacks.
To understand how helps your organization, make sure to read out this article. Azure Defender for DNS provides an additional layer of protection for your cloud resources by continuously monitoring all DNS queries from your Azure resources and runs advanced security analytics to alert you when suspicious activity is detected. To read more about how Azure Defender for DNS protects against issues, please read our official documentation.
Planning
With Azure Defender for DNS, we are looking at all the azure resources in an environment that’s connected to the Azure DNS, we are monitoring all the DNS queries that your resources are performing and detecting threats based on these queries so by doing so, we are actually protecting a variety of Azure resources that’s connected to this layer.
As part of your Azure Defender for DNS PoC you need to identify the use case scenarios that you want to validate. Common scenarios like, you may want to be notified when a DNS attack happens in your environment, DNS tunneling is another type of attack which is trying to exfiltrate sensitive data from your Azure resources, another type of attack is DNS cache poisoning for example, when an attacker is trying to redirect your communication to a malicious website. These attacks utilize DNS mechanism to attack the resource.
Azure Defender for DNS doesn’t use any agents. To protect your DNS layer, you need to enable Azure Defender for DNS for each of your subscriptions to protect the entire Azure subscription with Azure Defender.
Preparation
You need at least Security Admin role to enable Azure Defender for DNS. For more information about roles and privileges, visit this article. If you are conducting this PoC in partnership with the SOC Team, make sure they are familiar with the alerts that may appear once you enable this plan. Review this article that gives you guidelines on how to respond to Azure Defender for DNS alerts Alerts Reference Guide. You can view list of all Azure DNS alerts from this article.
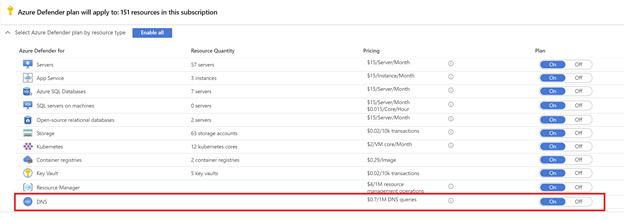
As of this blog writing, Azure Defender for DNS pricing model would be $0.70/1M Queries. Please visit our Pricing page to calculate the estimation of price in your environment.
From the readiness perspective, make sure to review the following resources to better understand Azure Defender for DNS
- Azure Defender for DNS : Azure Security Center in Field #13
- Azure Defender for DNS Documentation
- How to respond to Azure Defender for DNS alerts
Implementation and Validation
To test and validate the Security alerts for Azure Defender for DNS follow the steps from this great article to trigger a test alert. For a complete list of all analytics available for Azure Defender for DNS, read this documentation.
Whether an alert is generated by Azure Defender for DNS or received by Azure Defender from a different Microsoft security solution (MDE for example), you can also export it. To export your alerts to Azure Sentinel, any third-party SIEM, or any other external tool, follow the instructions in Exporting alerts to a SIEM. To investigate Azure Defender alerts using Azure Sentinel, make sure to check out this blog to understand how they operate in a better together scenario.
If you find an alert not relevant, you can manually dismiss it. Alternatively, you can also use suppression rules feature to automatically dismiss similar alerts in the future. Follow our documentation if you’re looking to learn more about Suppression of alerts.
Make sure to check out our Azure Security Center Github repository which gives you access to numerous sample security playbooks that will help you automate in remediating a recommendation.
Conclusion
By the end of this PoC you should be able to determine the value proposition of Azure Defender for DNS and the importance to have this level of threat detection to your workloads.
Stay tuned for more Azure Defender PoC Series!
Reviewer
Special Thanks to Yuri Diogenes & Tal Rosler for reviewing this article.
Posted at https://sl.advdat.com/3fa5bL6