Last year at Microsoft Inspire, we shared gratitude for the amazing work our partners did in helping our joint customers rapidly shift to remote work. As the world continues to evolve and the new reality takes hold, two trends are shaping our customer’s priorities this year: a shift to hybrid work and a growing sophistication of cyber threats. As our customers navigate these changes, they continue to lean on our partner ecosystem to help them adapt. One critical way our partners have helped customers adapt is by helping them adopt a Zero Trust security strategy.
While starting a Zero Trust journey can seem intimidating, inaction is no longer a choice. Together, with our partners, we have a shared accountability to guide every customer through this journey. For organizations seeking guidance on where to start, we recommend building a strong foundation by securing identities and endpoints. At Microsoft Inspire this week, we’re sharing key strategies that we recommend in building such foundation.
Modernizing identity and endpoint management
To unlock the advanced security and a comprehensive Zero Trust strategy, accelerate your journey to the cloud by modernizing identity and endpoint management solutions – a growing priority for business leaders.
Modernization may look like an overwhelming task, but the key to making it actionable is to focus on managing critical access decisions from the cloud and eliminating common attack vectors. Modernizing authentication from legacy federation allows you to choose the best access path for your business, and staged-roll out can make the migration seamless by testing deployment in a control group. Blocking legacy authentication helps ensure multifactor authentication can be enforced, and can be set as a default policy with Conditional Access. And to unify access management sync all on-premises identities to the cloud with tools like Azure AD connect cloud sync, which works even for complex identity environments with hundreds of disconnected Active Directory (AD) forests.
To modernize endpoint management, Microsoft Endpoint Manager can chart the path to the cloud at a pace that fit your needs. Microsoft Endpoint Manager brings together Configuration Manager and Intune in a single, unified endpoint management solution, to be used individually or together in co-management.
Finally, to modernize identity and endpoint management, unify app management with a single cloud identity and cloud endpoint management solution. Connecting all apps to one identity system gives better visibility and control into the apps being used and simplifies access to resources with one set of credentials, and our solutions work across cloud apps to on-premises apps as well as desktop and mobile apps.
Secure your hybrid workforce
When all employees work in an agile and hybrid environment, securing identities and endpoints becomes even more important. The first step in securing the hybrid workforce is to verify user identities with strong authentication. Passwords are the weakest link in a security chain, so that’s why we believe strongly that if you only do one thing to protect yourself, start with multi-factor authentication – which can prevent 99.9% of identity attacks. For even stronger authentication, we go passwordless - it is more secure and easier to use.
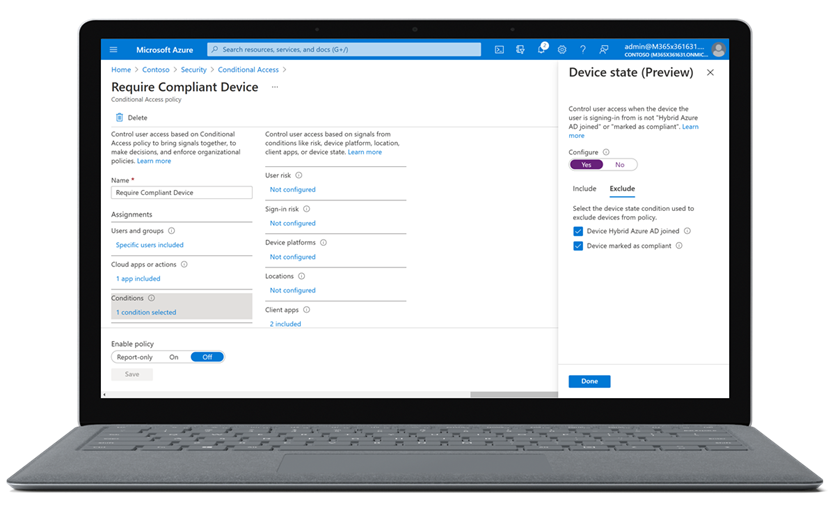
Next, limit access to only compliant and trusted devices with policies that prevent vulnerable and compromised devices access to resources. You can secure your endpoints by enrolling them in device management, applying data protection policies on your devices and using threat protection solutions like Microsoft Defender for Endpoint to detect compromised devices.
Once you established control points for identities and devices, configure adaptive access policies based on context and risk assessment. With Conditional Access, fine-tune access policies based upon user, device, location, and session risk assessment. And we continue to make Conditional Access smarter by enabling more granular controls like building policies upon the authentication context, or Continuous Access Evaluation that constantly re-assesses if access conditions are met and can interrupt a session if a change is detected.
Another critical factor in access decisions are permissions that your customers give to their employees and partners, which can be based on roles, projects, or other attributes. While those permissions are easy to grant, they are much harder to track, or revoke access when it is no longer needed. With a growth of extended workforce, having one solution to manage such permissions for everyone is increasingly important. Identity Governance built into Azure AD helps you protect, monitor, and audit access to critical resources.
Transform employee experiences
Delightful employee experiences are a growing priority for business leaders as remote work makes it even harder to rely on traditional approach to IT helpdesks. One example – in the US alone 49 million remote workers report that it takes days—and even weeks—to get IT issues fixed1.
Creating a great employee experience starts when a new employee is onboarded and hired. Using Azure AD provisioning, Microsoft Endpoint Manager and Windows Autopilot organizations can shorten this process from days to hours or even minutes and grant access to the appropriate apps and devices on day one. With Azure AD verifiable credentials, you can simplify this experience even more – for example, you can confirm information about a new hire—like their education and professional certifications in minutes, without collecting and storing their personal data.
Moving past on-boarding, a single sign-on can help streamline how employees access the apps they need. One of the easiest actions to improve employee productivity is to connect ALL applications to Azure AD from cloud apps like Workday, ServiceNow, and even AWS to on-premises apps or custom-built apps. Once apps have been connected to Azure AD, end users can easily discover and launch all their applications from our centralize app launch portal, My Apps.
Customize secure access for all users
Secure access and delightful experiences should extend to all users. Let’s take one example – frontline workers. Last year we’ve all seen the essential role they play in our society yet 75% still don’t have the right tools to do their work.2 We’re working with our partners and customers to change that by creating experiences that adapt to their work environment. The first step is to streamline the sign-in processes with one-time SMS codes and empower frontline worker credential management, like adding phone numbers and approving password resets, in the My Staff portal. With kiosks being a common tool for frontline roles, shared device mode allows workers to securely sign-in and sign-out of all their apps and browser sessions on such devices.
Another critical priority is building long lasting relationships with your customers. With Azure AD B2C, organizations and developers have the flexibility to tailor sign-in experiences of their customer-facing apps and build granular access policies. And to further protect customer accounts and revenue from abuse and fraud, Azure AD B2C integrates with Dynamics Fraud Protection. With this integration, you can defend against fake account creation, account takeovers, and fraudulent account access. You can also improve transaction acceptance rates with insights that balance revenue opportunity against fraud loss and checkout friction.
Join us virtually, live or on-demand at Microsoft Inspire
The changes in how and where we work and increased security threats require a new set of principles and a new security approach: Zero Trust with identity and endpoints as a foundation. Taken together, Azure AD and Microsoft Endpoint Manager, along with our integrated security approach, helps ensure that only the right people are getting the right level of access across your organization, elevating both security and end-user productivity.
No matter where you are in the world, I hope you will join us during at Microsoft Inspire for our sessions. Join the conversation on Twitter and LinkedIn with the hashtag #MSInspire.
- TS03: Build a foundation of trust and security
- BRK122: Identity and endpoint management – a strong foundation for Zero Trust and profitability
- OD122: Build a business around helping customers drive towards a Zero Trust framework
- ATEBRK122: Ask the Experts: Identity and endpoint management – a strong foundation for Zero Trust and profitability
Best regards,
Irina Nechaeva
Senior Director, Identity Product Marketing
Source:
- 1E American Remote Work Survey, July 20, 2020
- Equip Firstline Workers with Better Tools to Drive Engagement, Forrester Opportunity Snapshot: A Customer Study Commissioned by Microsoft, December 2018
Learn more about Microsoft identity:
- Return to the Azure Active Directory Identity blog home
- Join the conversation on Twitter and LinkedIn
- Share product suggestions on the Azure Feedback Forum