This post was authored by @johnengels, a Senior Program Manager from the Microsoft Defender for Office 365 team.
Security operations (SecOps) teams frequently need to investigate security alerts associated with emails and online interaction. Critical to this is ensuring that malicious emails associated with a likely attack are fully removed from all mailboxes – plus verifying no users or mailboxes have been compromised through interaction with any delivered emails. These days, the attack methods used by malicious actors, along with the high volume of email they send out, ensures that SecOps team are always busy with this task.
Earlier in May 2021, we announced that Microsoft is positioned as a leader in The Forrester Wave™: Email Security, Q2 2021, receiving the highest possible score in the incident response category. This represents the latest validation of our relentless effort, strategy, and focus on offering our customers industry-leading protection against threats orchestrated over email and collaboration tools – and of course industry-leading incident response capabilities.
Microsoft Defender for Office 365 is now rolling out three email investigation improvements that will drive additional SecOps efficiencies. The following changes will directly reduce the volume and prioritize the most malicious automated investigations for SecOps approval:
- Email actions are created only when malicious emails’ latest delivery location is in a cloud mailbox
- Pending email actions are updated based on the latest delivery location
- Investigations prioritize the most malicious threats for action
Email actions are created only when malicious emails’ latest delivery location is in a cloud mailbox
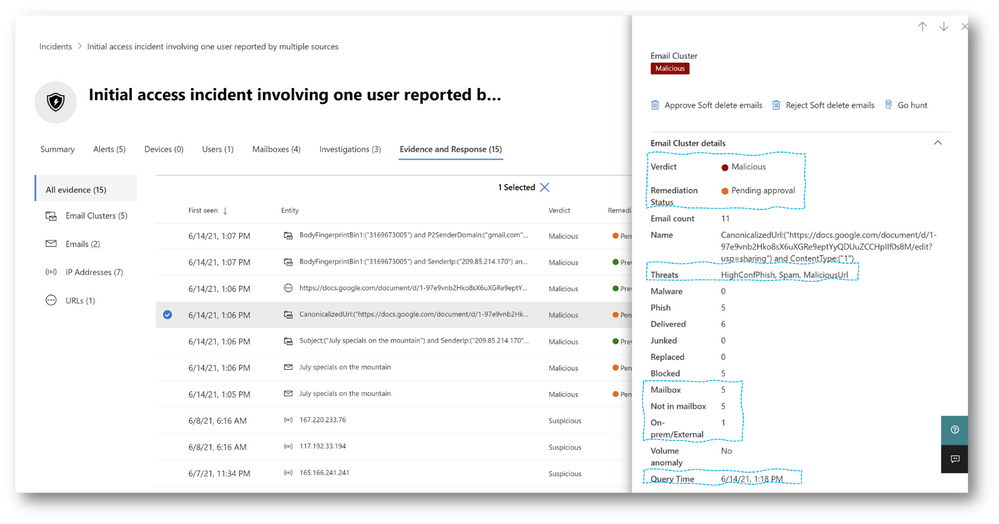
Previously automated investigations in Defender for Office 365 leveraged ‘original delivery information’ to identify emails that needed cleanup. This provided a view of emails that were initially visible to end users with recommendations on emails that should be removed. With this change, we are now pivoting the investigation email clustering analysis to the ‘latest delivery location’ information. As a result, investigations for things like Zero-hour auto purge (ZAP) or user submissions will show malicious emails that are still present in inbox or junk folders at the time of the investigation still in need of removal. The email location information for emails and email clusters will clearly show the latest delivery location and number of emails ‘in mailbox’, ‘not in mailbox’ (i.e. blocked or remediated), and ‘on-premise/external’ (inaccessible to Defender for Office 365’s remediation). Most importantly, to reduce SecOps work, the email analysis will now only trigger pending email actions when the emails are considered malicious and at least one email still in a cloud ‘mailbox’.
The latest delivery location and action changes that are currently rolling out apply to both the original emails that triggered the alerts as well as identified email clusters for similar emails and malicious URLs and files. The net effect of these changes is that you’ll see more current location information with fewer email actions required, particularly for ZAP alert investigations. After this change, if you see pending email actions for ZAP investigations, you should review and approve those actions to remove any residual email threats that remain.
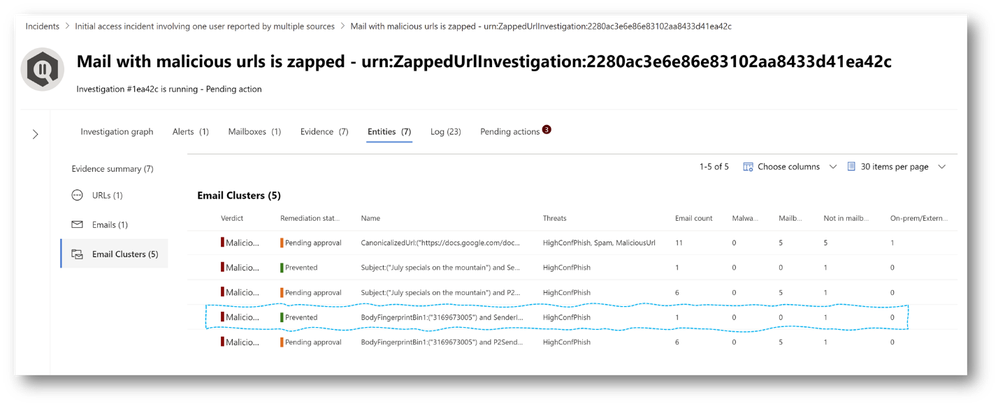
Pending actions are updated based on the latest delivery location
The Defender for Office 365 team is also improving investigations to re-analyze the email status after the investigation has completed. Until an investigation’s actions are approved or rejected, the investigation will periodically re-evaluate the investigation’s email findings and actions against the latest delivery locations then update the remediation status. This updates the investigation’s findings and the pending actions based on the latest remediations from ZAP, manual admin actions, as well as other approved automated investigations actions. If all malicious emails with pending actions have been removed from the mailboxes, the actions will cancel, with the incident and action center showing the emails as remediated (with updated location information). If all the investigation’s email actions have been completed by other remediations, then the investigation will change to ‘remediated’, and the original alerts will close.
Investigations prioritize the most malicious threats for action
Investigations are also being updated to surface to SecOps personnel the most relevant threats, helping ensure they are given sufficient attention and that actions are driving critical containment activities.
- First, the investigation’s email analysis is changing to use the latest Defender for Office 365 threat categories: malware, high-confidence phishing, normal phishing, and spam. This provides security teams with the ability to focus on the most critical malicious threats included in the investigation (high confidence, e.g. a credential theft URL) vs. items that are simply suspicious. It also ensures that comparing investigations to threat explorer or advanced hunting data provides more consistent results in terms of threat types.
- A second improvement is that investigations only create recommended actions for emails and email clusters determined to be the most critical threats: malware, high-confidence phishing, malicious URLs and malicious files. This further reduces SecOps workloads –by focusing valuable time and actions on malicious emails.

Coming up in Part 2...
In this blog, we talked about the new email analysis improvements in Defender for Office 365 investigations and how they will improve SecOps efficiencies. The new threat types, latest delivery locations, and updates after investigation completion ensure that SecOps teams get clearer threat data, more accurate and recent location information, plus fewer and more focused actions. In the next blog post, we will hear from some of our closest partners leveraging these capabilities in Microsoft Defender for Office 365 to help efficiently and effectively detect and respond to threats. Stay tuned!
Do you have questions or feedback about Microsoft Defender for Office 365? Engage with the community and Microsoft experts in the Defender for Office 365 forum.
Posted at https://sl.advdat.com/3iwmMxY