With recent attacks moving beyond simple data theft to target core business operations, security teams are adopting new continuous detection strategies for their industrial control system (ICS) and Operational Technology (OT) networks.
So we’re proud to report that MITRE Engenuity’s inaugural ATT&CK® Evaluations for ICS showed that Microsoft successfully detected malicious activity for 100% of major attack steps — plus industry-leading visibility for 96% of all sub-steps (i.e., fewest missed detections of any other vendor).
TRITON and MITRE ATT&CK for ICS
Most network defenders are already familiar with MITRE ATT&CK for Enterprise, and Microsoft has previously participated in three years of MITRE ATT&CK Evaluations.
ATT&CK for ICS builds upon ATT&CK for Enterprise. By enumerating specific adversary behaviors and TTPs for ICS/OT applications and devices, it provides a common language to describe attacks on our most critical infrastructures, including energy utilities, manufacturing, pharmaceuticals, chemicals, food, oil refineries, wastewater treatment facilities, and more.
In this initial round of evaluations, MITRE emulated the TTPs associated with the TRITON malware. This malware has previously been used to compromise safety controllers and industrial systems around the world, including oil and gas and electrical plants in the Middle East, Europe, and North America. (For more details about the TRITON kill chain, see the “Deep dive” section below.)
How Defender for IoT delivered industry-leading visibility for the TRITON kill chain
Azure Defender for IoT is an agentless, network-layer monitoring solution with the industry’s only patented, ICS/OT-aware behavioral analytics and a deep understanding of legacy and proprietary industrial protocols, applications, and ICS/OT devices.
Clients include 3 of the top 10 US electric utilities and one of the largest US water providers, plus deployments in some of the world’s most demanding industrial and critical infrastructure environments across the Americas, EMEA, and Asia-Pacific region.
Clients can deploy the solution fully on-premises or in cloud-connected environments. Tightly-integrated with our Azure Sentinel SIEM/SOAR solution[1], it also provides built-in support for third-party SOC tools including Splunk, IBM QRadar, and ServiceNow.
In MITRE’s rigorous testing, the Microsoft ICS security solution provided visibility for 100% of major steps and 96% of all sub-steps in the emulated TRITON attack chain (with the fewest detections marked as “None” of any other vendor).
Additionally, Defender for IoT provided visibility for nearly 100% of all network-based behaviors (in contrast to sub-steps that rely on Windows host-based logs for detection[2]).
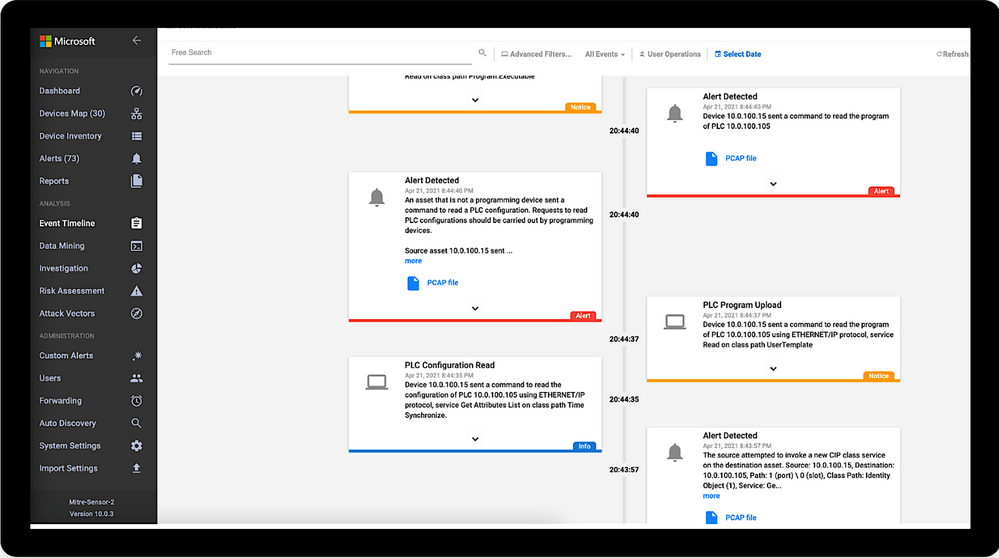
See example below showing how Defender for IoT displays a complete timeline of suspicious events including reading and writing to the safety PLC.
Event timeline generated by Defender for IoT’s ICS-aware behavioral analytics, showing sequence of events leading to adversary inserting custom backdoor into safety PLC, with PCAPs immediately available for deeper investigation.
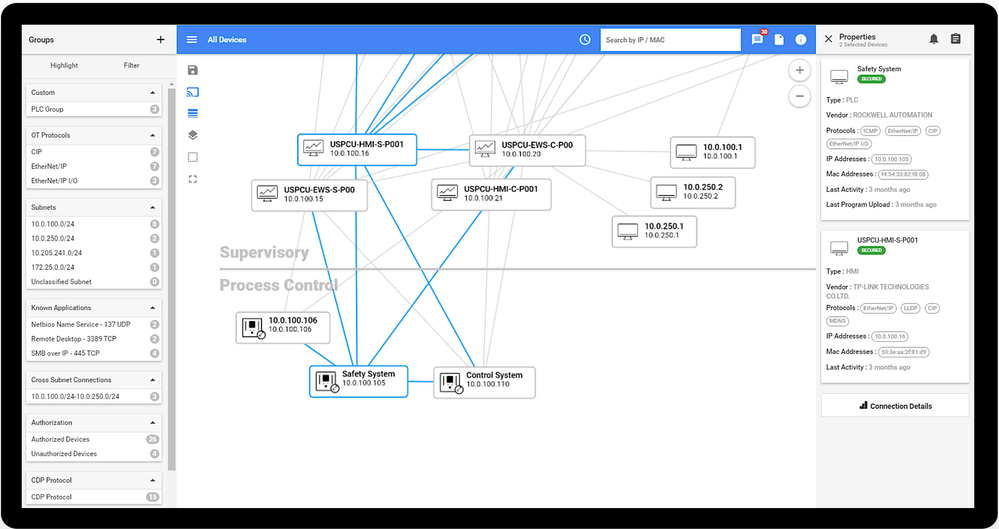
Defender for IoT showing ICS assets discovered via passive monitoring in TRITON emulation. Arranged via the standard Purdue Model, the topology map indicates active communication paths with blue lines and device properties (device type, OT vendor, protocols, etc.) at top right. To aid in threat hunting and investigations, the diagram can be filtered by protocol, subnet, applications, cross-subnet connections, and custom groupings.
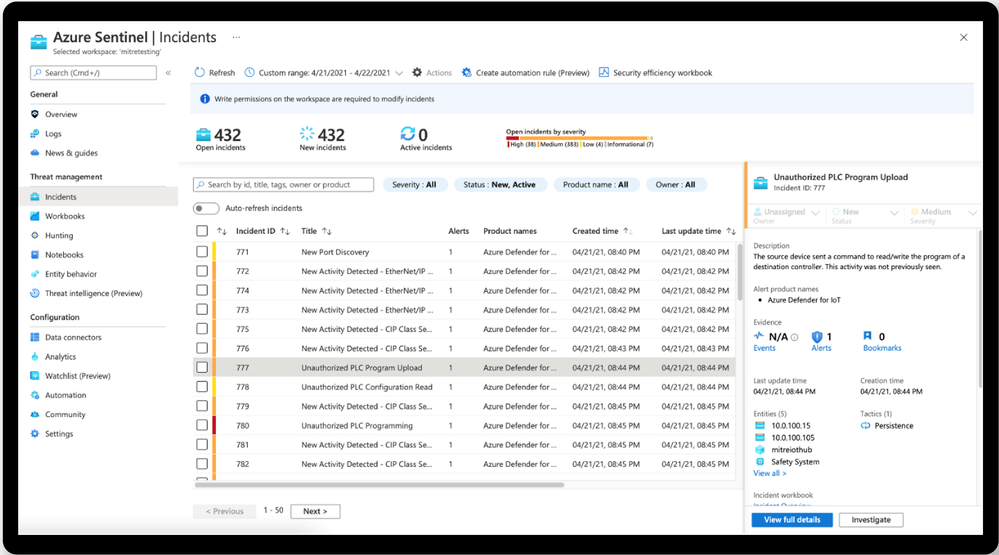
Alerts generated by Defender for IoT, as viewed in Azure Sentinel | Incidents.
Simulated investigation graph in Sentinel showing IT and OT assets related to TRITON incident, including contextual details obtained from Defender for IoT about related ICS devices to aid in investigation and response.
Looking to the future
Our mission is to empower world-class IT/OT defenders by continuing to drive product innovation and excellence, listening to customers, and investing in research to deliver increasingly intelligent solutions. We attribute the success in this evaluation to these investments and our customer-first approach.
To gain more holistic protection for these types of sophisticated multi-stage attacks crossing IT/OT boundaries, Microsoft clients can also incorporate our unified Microsoft 365 Defender stack — with its market-leading capabilities in Microsoft Defender for Endpoint and Microsoft Defender for Identity — which demonstrated 100 percent coverage of attack chain steps in the most recent MITRE ATT&CK Evaluation for Enterprise.
We look forward to continuing to collaborate with the MITRE team as the evaluation process evolves. For example, Microsoft Defender for Endpoint could be used in the future to block and more fully detect host-level events from the TRITON attack such as process and file creation, in addition to the network-layer events detected by Defender for IoT’s passive network monitoring technology.
Learn more
Microsoft Security is a Leader in five Gartner Magic Quadrants and seven Forrester Waves. Check out the Defender for IoT training site and Go inside the new Azure Defender for IoT blog post. To learn more about Microsoft Security solutions visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity.
Appendix: TRITON Deep Dive
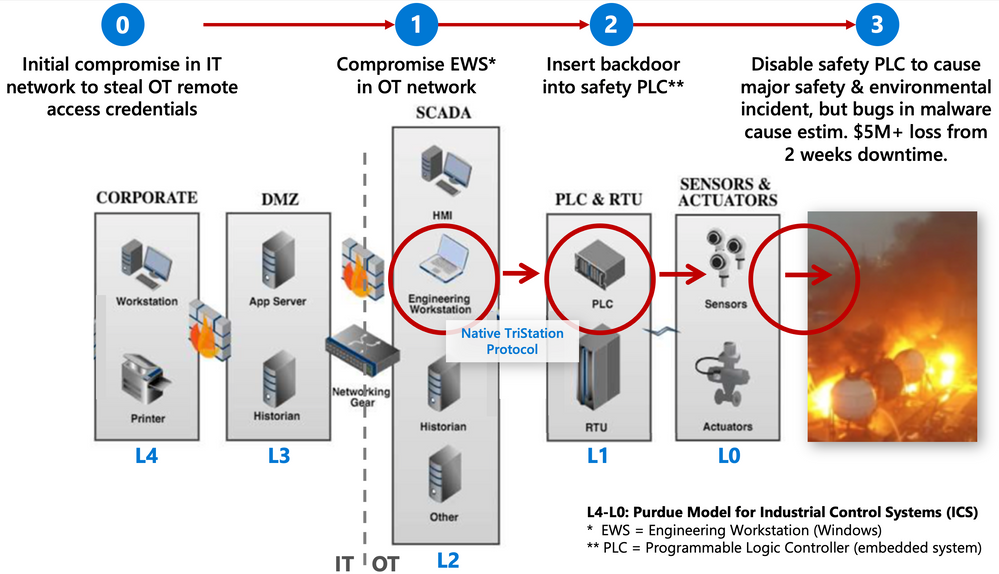
The TRITON attack on a petrochemical facility is illustrative of how adversaries leverage living-off-the-land tactics and vulnerabilities to move laterally from IT to OT networks and compromise industrial control systems. The kill chain diagram below is a simplified version of the full attack path.
Multi-stage TRITON kill chain showing initial compromise of IT network (step 0) and subsequent compromise of OT network and safety controllers (steps 1-3).
- The adversary initially compromised the corporate IT network. This could have occurred via a phishing attack, supply chain attack, infected USB drive, malicious insider, or other mechanisms.
- From there, they used the Mimikatz credential stealing tool to obtain OT remote access credentials in order to establish their initial foothold in the OT network.
- The adversary’s ultimate goal was to disable safety controllers designed to shut down the plant when unsafe conditions are reached, such as the temperature or pressure in a tank going above a safety threshold.
- After pivoting to OT, the adversary uploaded a purpose-built ICS RAT into the safety controllers using its native TriStation protocol. They used a standard PLC logic update function that OT engineers themselves use from time to time — which is a great example of attackers employing Living-off-the-Land (LOTL) tactics in an ICS context.
- Based on malware reverse engineering by Microsoft’s Section 52 security research team, we also know they designed a custom mechanism to communicate with the RAT and control the PLC using unused fields in the TriStation protocol (so the PLC could continue operating normally without the campaign being detected),
- With the safety system out of the way, we believe the adversary intended to manipulate control systems to cause a major safety and environmental incident, including physical damage to the facility and potentially loss of human life.
- Due to bugs in the adversary’s malware, the plant was accidentally shut down on 2 separate occasions — leading to millions in losses due to downtime and clean-up costs — but it could have been a lot worse.
- In addition to weaknesses in the plant’s IT/OT security controls, another key factor was the organizational breakdown that also seems to have existed. There were no clear definitions of which team was responsible for ensuring that security controls had been properly implemented and were actually effective, and who was responsible for the security of the OT environment — IT security, OT personnel, the system integrator, the OT automation vendor, etc.
Overview of the TRITON test scenario
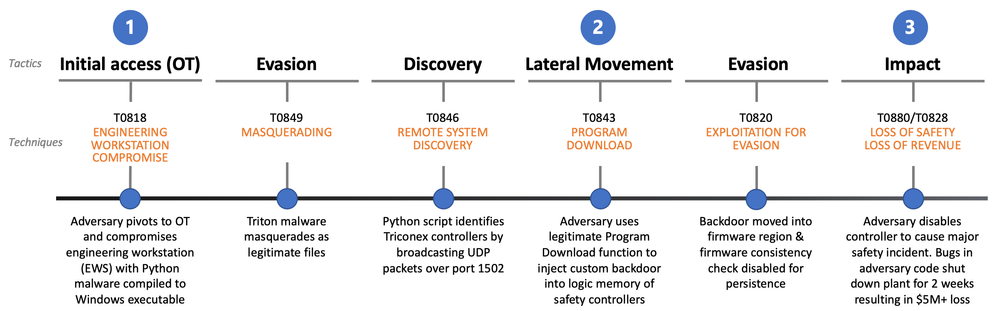
In this MITRE evaluation, the emulation begins with the OT network compromise. The diagram below highlights key steps in the MITRE emulation, along with Tactics and Technique examples from the ATT&CK for ICS framework. Not all steps are shown, as the scored emulation consists of 100 sub-steps.
Simplified TRITON kill chain showing Tactics and Techniques from MITRE ATT&CK for ICS emulation.
[1] There is no cost for ingesting Defender for IoT alerts and incidents into Azure Sentinel.
[2] In the inaugural evaluation, the test environment was not configured to use Microsoft Defender for Endpoint to detect host-based events such as file and process creation.
Posted at https://sl.advdat.com/2Wcp8dK