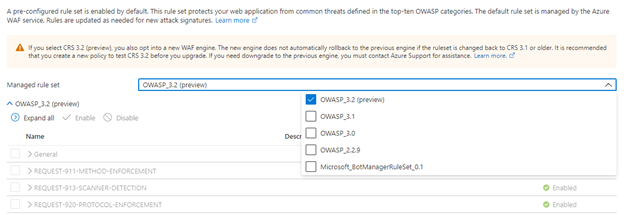
A new managed rule set called OWASP_3.2 has been launched in public preview on Azure WAF for Application Gateway. This rule set is based on OWASP ModSecurity Core Rule Set (CRS), which intends to protect web applications from the most common attacks, such as the OWASP Top 10. We often refer to the OWASP_3.2 rule set interchangeably with CRS 3.2.
What are the requirements to use CRS 3.2?
You must be using Azure Application Gateway WAF_v2 SKU, and you must be using WAF Policy to manage your Azure WAF settings.
What changes when enabling CRS 3.2?
With the new WAF engine, you will receive the following benefits:
Reduced false positives and added security rules
CRS 3.2 has several improvements in comparison to the previous CRS versions. Multiple security rules have received fixes that help lower the occurrence of false positives, and new security rules have been added to detect and protect against more threats, such as attacks against JAVA applications. For more detailed information on what changed from CRS 3.1 to CRS 3.2, you can refer to the OWASP ModSecurity Core Rule Set Version 3.2.0 change log.
Better performance
The new WAF engine has been designed to allow for more flexibility, reliability, and efficiency. This engine offers improved memory utilization, latency, and throughput – which contributes to overall better performance when using Azure WAF for Application Gateway v2.
As an example, we compared the latency rates between the new WAF engine, old WAF engine, and Application Gateway v2 with no WAF enabled. Keep in mind that the examples below are findings from internal test samples, and actual performance improvement rates for customers’ resources may vary.
In the sample test below, we verified the amount of latency based on a GET request with different cookie sizes. We can see in the chart below how a request with a cookie size of 4kb with the old WAF engine resulted in a latency of above 100 milliseconds, while the latency for the same cookie size with the new WAF engine is below 50 milliseconds. The performance improvement gets even more significant when comparing to a larger cookie size, as seen with the 16kb cookie.
In another sample test, we measured the amount of latency based on a POST request with different payload sizes. We can see in the chart below that a payload of 128kb in size has an expected latency of just above 500 milliseconds with the new WAF engine, while the same payload size reaches almost 2500 milliseconds of latency with the previous WAF engine.
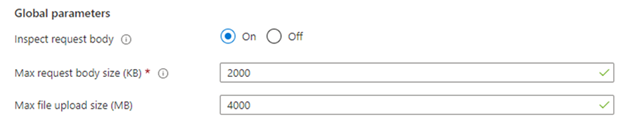
Increased limits
Due to improvements in our new WAF engine in the backend, we now allow customers to increase the limits for Max Request Body Size and Max File Upload Size. The Max Request Body Size limit was increased from 128KB to 2MB, and the Max File Upload Size limit was increased from 750MB to 4GB.
Posted at https://sl.advdat.com/3kF3uc7