External devices such as USB and home printers are commonplace tools needed to complete daily business operations. These devices help employee productivity, but also pose a threat to enterprise data and serve as a potential entry point for malware and viruses. The move to remote work due to COVID-19 over the last year has raised the risk to another level.
End user activities represent one of the most common threat vectors and Microsoft Defender for Endpoint brings a compelling story for organizations looking to reduce their security exposure associated with removable media and printing.
We are excited to announce new device control capabilities in Microsoft Defender for Endpoint to secure removable storage scenarios on Windows and macOS platforms and offer an additional layer of protection for printing scenarios. These new device control capabilities further reduce the potential attack surface on user’s machines and safeguard organizations against malware and data loss in removable storage media scenarios.
Overview
| Feature | Availability | Documentation |
|
Removable storage access control on Windows |
General Availability (MDE version 4.18.2106 or later) |
Removable storage access control |
|
Removable storage protection on Mac |
General Availability (MDE(Mac) version 101.34.20 or later) |
Device control for macOS |
|
Printer protection |
Public Preview |
Printer protection on Windows |
What’s new
Removable storage access control on Windows
We are bringing removable storage access control capabilities on Windows to complement our existing device control protection in scenarios such as Device Installation, removable storage Endpoint DLP, and removable storage BitLocker.
The new feature allows to Audit/Allow/Prevent Read, Write, or Execute access to removable storage based on various device properties, e.g., Vendor ID, Serial Number, Friendly Name, with or without an exclusion.
Removable storage protection on Mac
We also recently introduced removable storage protection capabilities on Mac. USB storage device control for Mac is designed to regulate the level of access given to external USB storage devices (including SD cards). The access level is controlled through custom policies. You can find more details in our Mac USB storage device control blog.
- The capability supports Audit and Block enforcement levels.
- USB device access can be set to Read, Write, Execute, No access.
- To achieve a high degree of granularity, USB access level can be specified for Product ID, Vendor ID, and Serial Number.
- The custom policy allows customization of the URL where user is redirected to when interacting with an end user facing “device restricted” notification.
Printer protection on Windows
The new printer protection feature allows you to block users from printing via a non-corporate network printer or non-approved USB printer. This adds an additional layer of security and data protection for work from home and remote work scenarios.
Getting started
The next few sections will go over how to get started deploying and using the new device control capabilities.
How to deploy removable storage access control on Windows
Removable storage access control policies can be applied for a user or machine via GPO (group policy object). The feature includes group configuration policy and access control policy.
For example, here is the most common scenario: Prevent Write and Execute access to all but allow specific approved USBs.
Step 1: Create groups
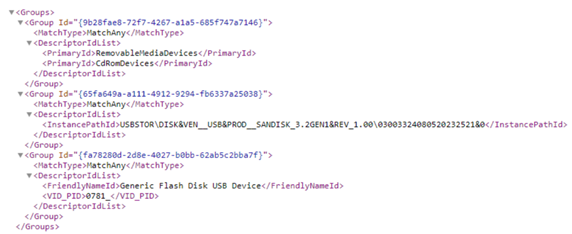
- Group 1: Any removable storage and CD/DVD. An example of a removable storage and CD/DVD is: Group 9b28fae8-72f7-4267-a1a5-685f747a7146 in the sample Any Removable Storage and CD-DVD Group.xml file.
- Group 2: Approved USBs based on device properties. An example for this use case is: Instance ID – Group 65fa649a-a111-4912-9294-fb6337a25038 in the sample Approved USBs Group.xml file.
Step 2: Create policy
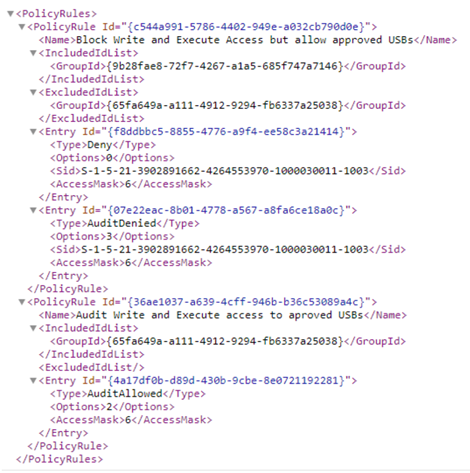
- Policy 1: Block Write and Execute Access but allow approved USBs. An example for this use case is: PolicyRule c544a991-5786-4402-949e-a032cb790d0e in the sample Scenario 1 Block Write and Execute Access but allow approved USBs .xml file.
- Policy 2: Audit Write and Execute access to allowed USBs. An example for this use case is: PolicyRule 36ae1037-a639-4cff-946b-b36c53089a4c in the sample Scenario 1 Audit Write and Execute access to approved USBs.xml file.
Deploy policy via Group Policy
- Combine all groups within <Groups> </Groups> into one xml file.
The following image illustrates the example of Scenario 1: Prevent Write and Execute access to all but allow specific approved USBs.
- Combine all rules within <PolicyRules> </PolicyRules> into one xml file.
If you want to restrict a specific user, then use SID property into the Entry. If there is no SID in the policy Entry, the Entry will be applied to everyone login instance for the machine.
The following image illustrates the usage of SID property, and an example of Scenario 1: Prevent Write and Execute access to all but allow specific approved USBs.
- Save both rule and group XML files on network share folder and put network share folder path into the Group Policy setting: Computer Configuration -> Administrative Templates -> Windows Components -> Microsoft Defender Antivirus -> Device Control: ‘Define device control policy groups’ and ‘Define device control policy rules’. If you cannot find the policy configuration UX in the Group Policy, you can download the WindowsDefender.adml and WindowsDefender.admx file by clicking 'Raw' and 'Save as'.
The target machine must be able to access the network share to have the policy. However, once the policy is read, the network share connection is no longer required, even after machine reboot.
Here is an example of configuring policy on Group Policy:
View device control data in Microsoft Defender for Endpoint
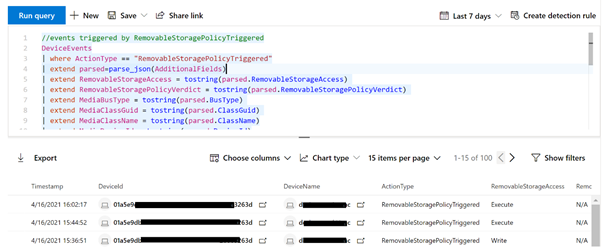
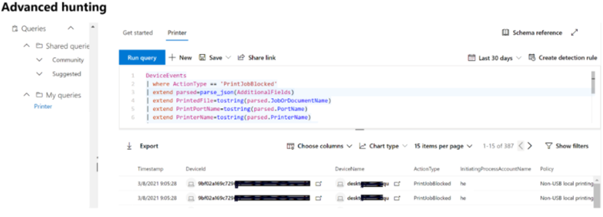
The policy events can be viewed in Microsoft 365 Defender and the Microsoft Defender Security Center via advanced hunting.
Here is an advanced hunting query example:
For more information, see Microsoft Defender for Endpoint Device Control Printer Protection | Microsoft Docs.
How to protect removable storage on Mac
To learn more about Mac USB storage device control, refer to our recent Mac USB storage device control blog. For a more in-depth overview of this capability and step by step guidance on configuring USB device control policies on macOS, refer to our Mac USB device control public documentation.
View Mac device control data in Microsoft Defender for Endpoint
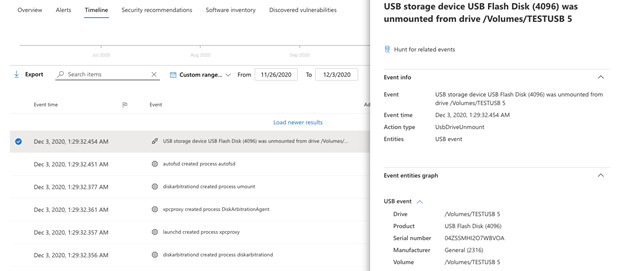
USB device mount/unmount events on Mac devices can be viewed in Microsoft 365 Defender and in the Microsoft Defender Security Center via advanced hunting and in the device timeline.
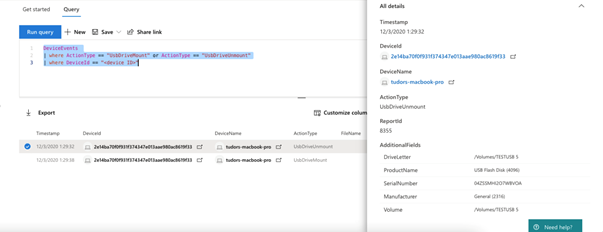
Here is an advanced hunting query example:
DeviceEvents
| where ActionType == "UsbDriveMount" or ActionType == "UsbDriveUnmount" or ActionType == "UsbDriveDriveLetterChanged"
| where DeviceId == "<device ID>"
And that is how the above advanced hunting query looks like in the security center:
Here is an example of Mac USB device control event in the device timeline page:
How to deploy printer protection on Windows
To deploy printer protection on Windows, you can apply the policy for users or machines via GPO or Intune/OMA-URI.
Deploy policy via Intune OMA-URI
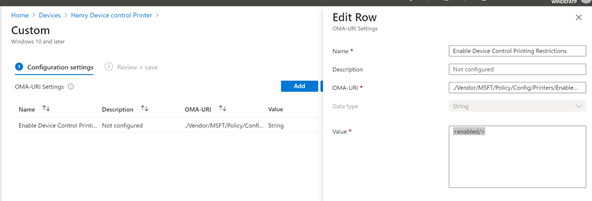
For Intune, currently printer protection supports Open Mobile Alliance Uniform Resource Identifier (OMA-URI) setting (Microsoft Endpoint Manager admin center: Devices -> Configuration profiles -> Create profile -> Platform: Windows 10 and later; Profile type: Templates -> Custom) only.
Block people from printing via any non-corporate printer
- Apply policy over machine:
- ./Vendor/MSFT/Policy/Config/Printers/EnableDeviceControl
- Apply policy over user:
- ./Vendor/MSFT/Policy/Config/Printers/EnableDeviceControlUser
The CSP support string Data type with Value:
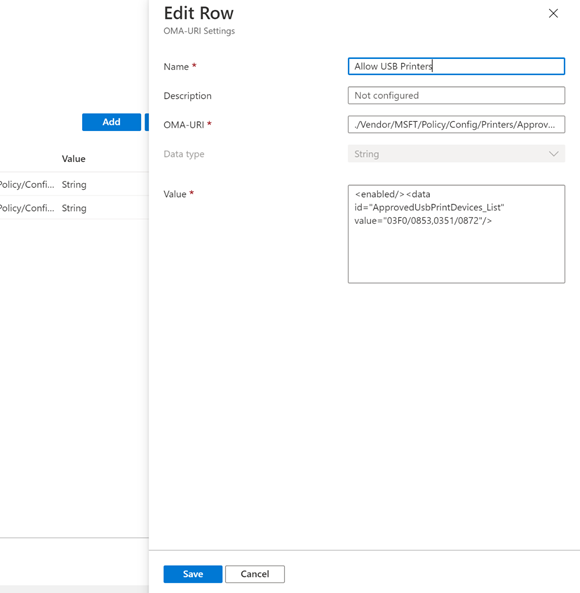
Allow specific approved USB printers
- Apply policy over machine:
- ./Vendor/MSFT/Policy/Config/Printers/ApprovedUsbPrintDevices
- Apply policy over user:
- ./Vendor/MSFT/Policy/Config/Printers/ApprovedUsbPrintDevicesUser
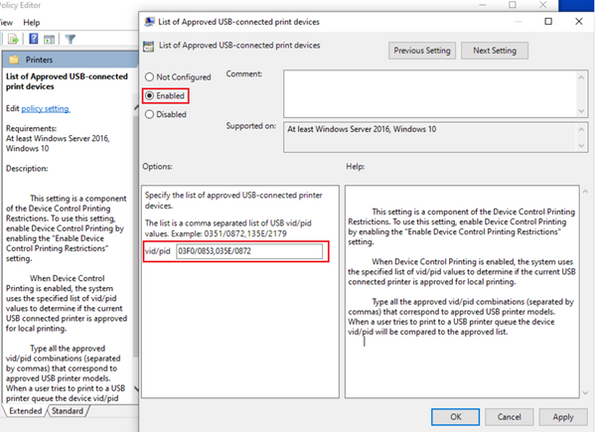
The CSP support string Data type with approved USB printer VID/PID via ‘ApprovedUsbPrintDevices’ property and the property supports multiple VID/PIDs via comma. Currently does not support wildcard.
The following is a policy allowing printing if the USB printer VID/PID is either 03F0/0853 or 0351/0872 - <enabled/><data id="ApprovedUsbPrintDevices_List" value="03F0/0853,0351/0872"/>:
Deploy policy via Group Policy
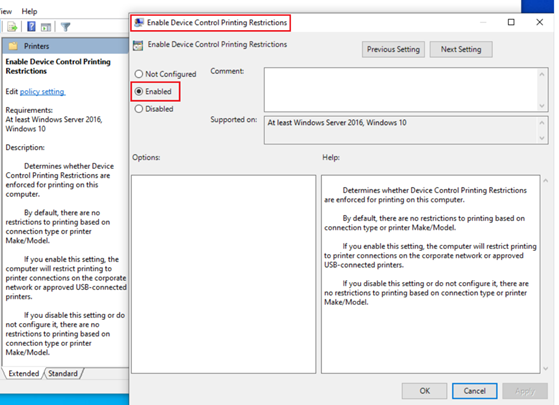
Block people from printing via any non-corporate printer
- Apply policy over machine:
- Computer Configuration > Administrative Templates > Printer: Enable Device control Printing Restrictions
- Apply policy over user:
- User Configuration > Administrative Templates > Control Panel > Printers: Enable Device control Printing Restrictions
Following is an example of configuring the policy in Group Policy:
Allow specific approved USB printers
- Apply policy over machine:
- Computer Configuration > Administrative Templates > Printer: List of Approved USB-connected print devices
- Apply policy over user:
- User Configuration > Administrative Templates > Control Panel > Printers: List of Approved USB-connected print devices
Following is an example allowing printing if the USB printer VID/PID is either 03F0/0853 or 0351/0872:
View device control data in Microsoft Defender for Endpoint
The policy events can be viewed in Microsoft 365 Defender and the Microsoft Defender Security Center via advanced hunting.
Here is an advanced hunting query example:
For more information, see our documentation: Microsoft Defender for Endpoint Device Control Printer Protection | Microsoft Docs
We’re excited to deliver these new device control functionalities to you. To experience these capabilities in public preview, we encourage you to turn on preview features for Microsoft Defender for Endpoint today. As always, we welcome your feedback and look forward to hearing from you! You can submit feedback directly to our team through the portal.
Microsoft Defender for Endpoint is an industry-leading, cloud-powered endpoint security solution offering vulnerability management, endpoint protection, endpoint detection and response, and mobile threat defense in a single unified platform. With our solution, threats are no match. If you are not yet taking advantage of Microsoft’s unrivaled threat optics and proven capabilities, sign up for a free trial of Microsoft Defender for Endpoint today.
Microsoft Defender for Endpoint team
Posted at https://sl.advdat.com/3z8TJXI