Microsoft has released security updates for vulnerabilities found in:
- Exchange Server 2013
- Exchange Server 2016
- Exchange Server 2019
These updates are available for the following specific builds of Exchange Server:
IMPORTANT: If manually installing security updates, you must install .msp from elevated command prompt (see Known Issues in update KB article).
The July 2021 security updates for Exchange Server address vulnerabilities responsibly reported by security partners and found through Microsoft’s internal processes. Although we are not aware of any active exploits in the wild, our recommendation is to install these updates immediately to protect your environment.
These vulnerabilities affect on-premises Microsoft Exchange Server, including servers used by customers in Exchange Hybrid mode. Exchange Online customers are already protected and do not need to take any action.
More details about specific CVEs can be found in Security Update Guide (filter on Exchange Server under Product Family).
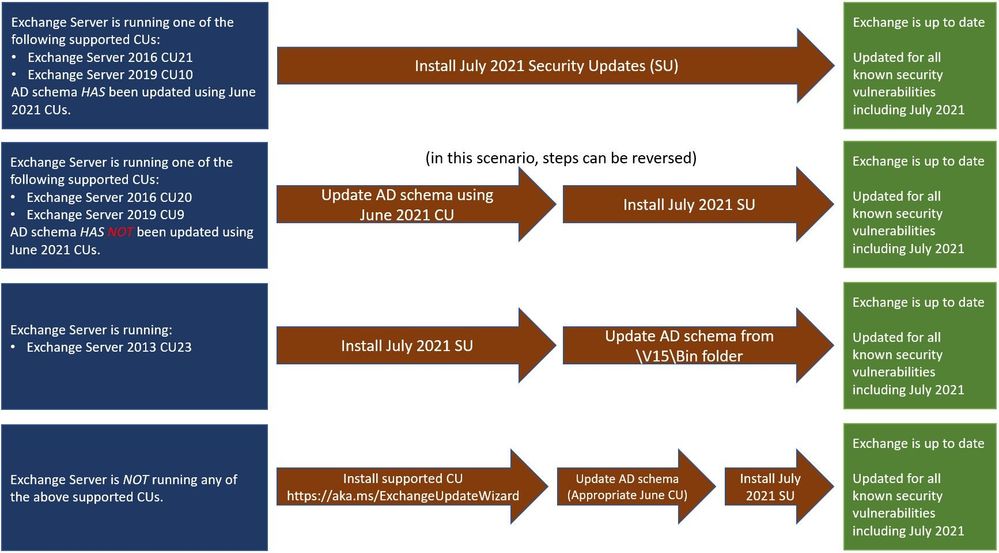
Latest /PrepareSchema needed for full effect
Because of additional security hardening work for CVE-2021-34470, the following actions should be taken in addition to application of July 2021 security updates:
|
The latest version of Exchange installed |
Additional steps needed to extend AD schema |
|
Exchange 2016 CU21 or |
Nothing; schema was extended during installation of June 2021 CUs. |
|
Exchange 2016 CU20 or |
Extend the schema using June 2021 CUs. |
|
Exchange 2013 CU23 |
- Install July 2021 Security Update for Exchange 2013 - Extend the Active Directory schema using the elevated Command prompt. Command will be similar to the following: “Setup.exe /PrepareSchema /IAcceptExchangeServerLicenseTerms” using the setup.exe from location “c:\Program Files\Microsoft\Exchange Server\V15\Bin\setup.exe” (use the folder for the installation location of your Exchange server) |
Known issues in July 2021 security updates
During the release of April 2021 SUs, we received some reports of issues after installation. The following issues reported for April 2021 SUs also apply to July SUs and have the following workarounds:
- Administrator/Service accounts ending in ‘$’ cannot use the Exchange Management Shell or access ECP. The only workaround at this time is to rename Admin accounts or use accounts with no ‘$’ at the end of the name.
- Some cross-forest Free/Busy relationships based on Availability address space can stop working (depending on how authentication was configured) with the error: “The remote server returned an error: (400) Bad Request.” Please see this KB article for how to solve this problem.
- Cmdlets executed against the Exchange Management Console using an invoked runspace might fail with the following error message: The syntax is not supported by this runspace. This can occur if the runspace is in no-language mode. Please see this KB article for more information.
Update installation
Because of the recommended schema update requiring the latest set of June 2021 CUs, there are several scenarios that you might need to follow:
Inventory your Exchange Servers / determine which updates are needed
Use the Exchange Server Health Checker script (use the latest release) to inventory your servers. Running this script will tell you if any of your Exchange Servers are behind on updates (CUs and SUs).
Update to the latest Cumulative Update
Go to https://aka.ms/ExchangeUpdateWizard and choose your currently running CU and your target CU. Then click the “Tell me the steps” button, to get directions for your environment.
If you encounter errors during or after installation of Exchange Server updates
If you encounter errors during installation, see the SetupAssist script. If something does not work properly after updates, see Repair failed installations of Exchange Cumulative and Security updates.
FAQs
My organization is in Hybrid mode with Exchange Online. Do I need to do anything?
While Exchange Online customers are already protected, the July 2021 security updates do need to be applied to your on-premises Exchange Servers, even if they are used only for management purposes. You do not need to re-run the Hybrid Configuration Wizard (HCW) after applying updates.
Do I need to install the updates on ‘Exchange Management Tools only’ workstations?
Servers or workstations running only Microsoft Exchange Management Tools (no Exchange services) do not need to apply these updates.
Instructions seem to indicate that for Exchange 2013, we should extend the schema after July 2021 SU is installed; is that correct?
Yes. Because we did not release an Exchange 2013 Cumulative Update (CU) that contains the new schema updates, the July 2021 SU package updates the schema files in Exchange server folders when July 2021 SU is installed. That is why once those files are updated (SU is installed) – we ask you to go and explicitly update the schema using setup from \v15\Bin folder.
We have Exchange 2016 CU20 and 2019 CU9 servers and have installed July 2021 security updates but did not run /PrepareSchema using June 2021 CUs first. Is this a problem?
No. Extension of AD schema using June 2021 CU is really a separate step that should be taken to address a specific CVE. There is no dependency in July 2021 SUs on this schema change, or vice versa. Just make sure that both of those actions are taken; order is not important.
NOTE: This post might receive future updates; they will be listed here (if available).
Posted at https://sl.advdat.com/3kkyv5f