We have added support for GitHub in Azure for U.S. Government and Azure China.
Due to compliance reasons, we suggest customers get their OAuth application to authenticate against their own GitHub accounts. To use GitHub in Azure Gov and Azure China, you can bring your own (BYO) GitHub OAuth application.
Note: BYO GitHub OAuth application capability is not available in Azure public. In Azure public, we use Microsoft managed GitHub OAuth app which simplifies the setup by not requiring customers to bring and manage their own OAuth applications.
Getting started steps:
- Create a GitHub OAuth application [Prerequisite]
Detailed steps -> https://docs.github.com/en/developers/apps/building-oauth-apps/creating-an-oauth-app
Make sure you enter the below properties accurately while creating the OAuth application.
- Application Name: <Your desired application name>
- Homepage URL: <Your Data Factory's web URL (domain), ex. "https://adf.azure.us">
Note: if you use ADF in multiple environments, you will need an app per environment (Azure China, Azure Gov, etc.). - Application Description: Optional description
- Authorization callback URL: Same as Homepage URL.
Copy the client id and client secret for use in the next step.
- Create or use existing Azure Key Vault in the same Azure environment (Azure Gov or Azure China) as your Azure Data Factory.
- Use an existing Azure Key Vault or create a new one in the Azure Portal.
- Create a new secret name and set the value equal to the GitHub client secret you generated earlier.
- Copy the full secret URL, ex. https://<account name>.vault.azure.net/secrets/github-client-secret-local2/37f145c97a134698ad74f105388ec282.
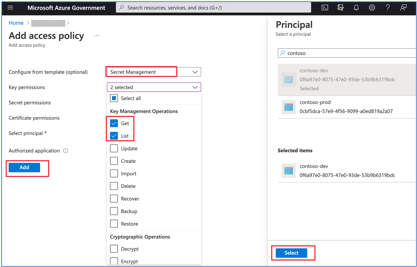
- Update the Access Policies on the left sidebar and click "+ Add Access Policy".
- Under secret permissions, grant "List, Get" permissions and select the principal as your Azure Data Factory. It will allow the data factory to access your GitHub client secret during GitHub authentication. Click add and return to the data factory.
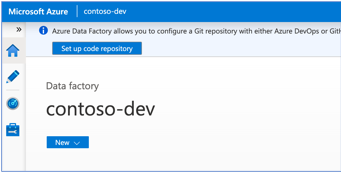
- Configure the GitHub repository in Azure Data Factory
- In the ADF management tab, select "Git configuration" and click "Configure."
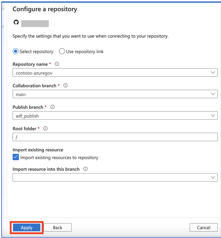
- Select repository type as GitHub and enter the GitHub account associated with your repository, then click continue.
- In the "Azure Government Cloud BYOA" popup, enter your GitHub client id and the secret URL, ex. https://<account name>.vault.azure.net/secrets/github-client-secret-local2/37f145c97a134698ad74f105388ec282.
- Click verify and log into GitHub in the popup window.
- If your OAuth app and key vault are correctly configured, you will then be able to complete your repository setup on the next screen.
Common issue:
Ensure your call back URL is correct and does not include a "/" at the end, ex. https://adf.azure.com is a valid URL, and https://adf.azure.com/ is not
Posted at https://sl.advdat.com/3sN31GZ