Whether you're looking at Intune as a replacement solution or as a green field deployment to manage your iOS, Android, Windows, and Mac devices, scoping and deploying a proof of concept (POC) is typically the first step. I would consider a POC to be user-driven only meaning Autopilot, DEP, etc... would be out of scope initially. Before diving into the tools, ensure that your organization or at least your POC user have the proper licensing assigned.
I recommend using security groups for your POC. This can be an Active Directory sync'd or Azure AD security group. Add your POC users to this group. Next, you'll need a global administrator in Azure to to set the MDM Authority to Intune. This can be found under Azure Active Directory --> Mobility (MDM and MAM). You can set the MDM user scope to your POC group.
If you are looking to also manage and POC Intune for Windows machines, you'll need your DNS admin to enter the proper enrollment CNAME records in your public DNS records.
For iOS and MacOS devices, this requires an Apple MDM Push Certificate. To begin, navigate to Microsoft Endpoint Manager --> Devices --> Enroll Devices -- Apple Enrollment. You'll need an Apple ID to associate with the push certificate. You can use any email address (i.e. apple@companyname.com) to create an Apple ID. The push certificate is active for two (2) years. If you enable MFA for the Apple ID (which you should), make sure the device is a shared device that all admins can get to and not associated with a phone number that is a personal number for an admin. If that admin leaves, then you will not be able to update the certificate. Walk through the steps to download the CSR, create the MDM push certificate in the Apple portal, and upload it to Intune.
For Android devices, you'll need a managed Google account. Same concept applies here. You can use any email to create a Google account (i.e. google@companyname.com) but ensure that if MFA is enabled that the token is stored on a shared device and the phone number is not associated with any admin's personal number. Once the account is created, link the managed Google Play account with Intune.
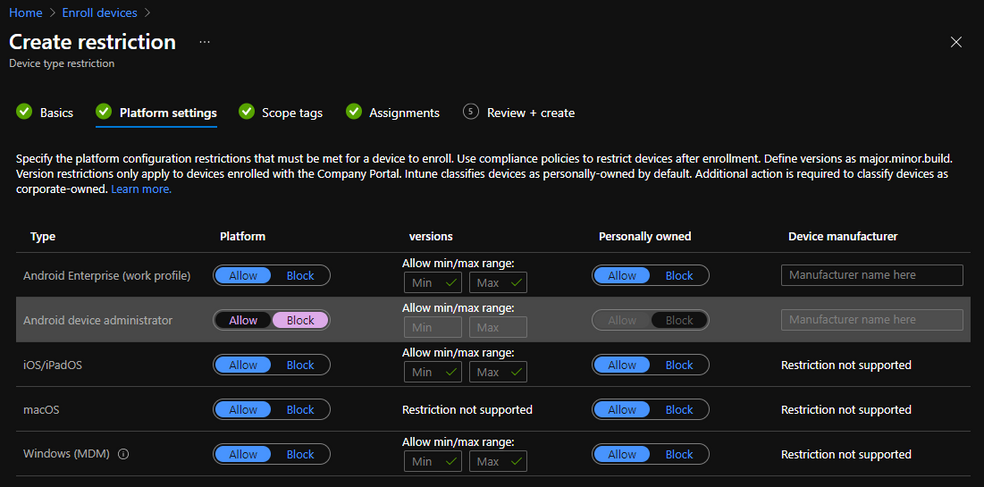
Note: I would recommend creating an Enrollment Restriction to block Android device administrator. Device admin was deprecated in Android 9.0 and has now moved to Android Enterprise (work profile) as default. This ensures only newer Android devices are allowed to enroll in your POC.
For Windows enrollment, that is automatically configured when you set the MDM authority. You can customize the enrollment status page but that is optional for the POC.
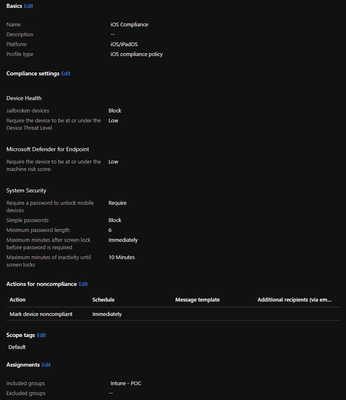
Next, I would configure a compliance policy for each OS that you plan to POC (iOS, Android, Windows, Mac). This ensure continuous device health attestation upon enrollment within Intune. What you pick for your compliance settings are dictated by your company's policies and risk analysis. Below is an example of an iOS compliance policy.
Once you have a compliance policy, I recommend configuring configuration policies. There are many ways to do this. For the mobile OS's (iOS and Android), I like to scope one configuration policy with multiple settings by default for the POC. For the desktop OS's, I like to scope one setting per policy. I have found the mobile OS's are a lot easier to configure with multiple settings while the desktop OS's tend to be a little bit more complicated so it's easier to have one policy per setting.
Again, what you pick in the policy is dictated by your own company's compliance requirements and risk analysis.
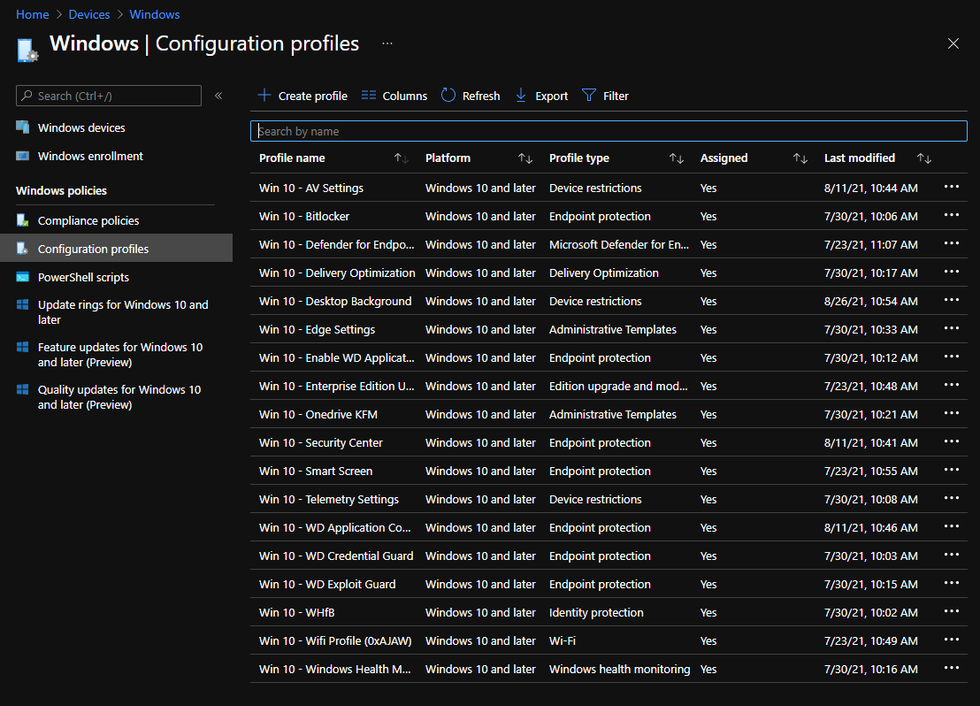
Example of Windows Configuration profiles
Once you're satisfied with the configuration policies, you can configure some apps to be available or deploy upon enrollment. Configuring iOS apps is pretty straight forward. The iOS store inventory is built into Intune and you can pull directly from that. To deploy Android apps, you "purchase" them in the managed Google Play store then sync them into Intune using the connection you created earlier. For Mac's, there are only a few apps that are built in (Office 365, Edge, Microsoft Defender for Endpoint). You can add Mac Line of Business apps but that is something I would recommend doing after the POC.
For Windows apps, it's important to make sure the Intune Company Portal is automatically installed on every Intune managed device. In order to do this, you must sync your Microsoft Store for Business with Intune. There are also some apps built into Intune (Office 365, Edge) that you can create a policy to deploy.
If you're looking to deploy Win32 or Line of Business apps, there are a number of ways to do it. Certainly you can test these in a POC but I recommend keeping it simple. Most users need just need email and Teams to get started. Don't try to boil the ocean. Take it one step at a time.
My recommendation is to walk through these steps as a POC. Get the devices enrolled first. Then look at what settings you want to manage as part of your company's compliance requirements or risk analysis. Finally, look at what you "can't" do. "I can't get on the corporate wifi." Ok, deploy a configuration profile for wifi. "I need this app on iOS." Find the app and deploy it.
Once you have that hammered out, you can move to Mobile Application Management which you can deploy on top of Intune for data loss protection and look to scope enrollment using Conditional Access.
Hopefully this helps in your Intune deployment. Email me if there are any questions or feedback at andyjaw@microsoft.com.
Posted at https://sl.advdat.com/3gQkslj