The security posture of an enterprise relies on the three pillars PROTECTION, DETECTION & RESPONSE. Azure is designed to strengthen all three pillars by providing a Cloud Security Posture Management Tool, Azure Security Center & a Cloud Workload Protection tool, Azure Defender.
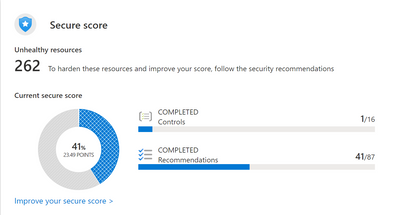
The security posture is assessed by a defined set of security controls with underlying recommendations on security configurations which make up the secure score of an organization for all subscriptions where Security Center is enabled. Microsoft recommends to keep the secure score to 100% so you can be sure your cloud environment is secure and your resources are protected proactively.
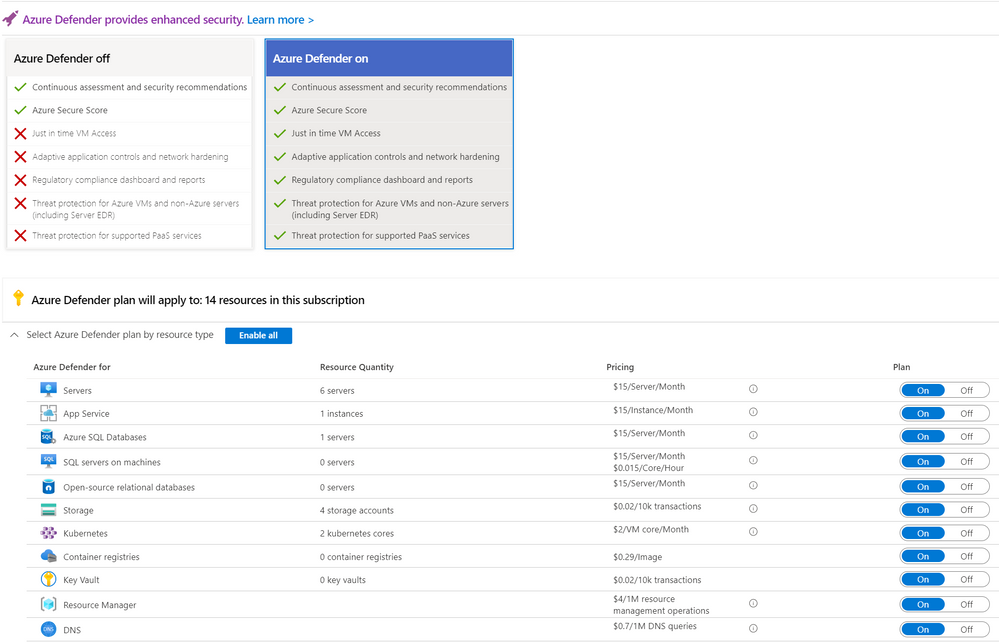
“Enable Azure Defender” is one of the security controls that make up the overall Secure Score. That means that all Azure Defender Plans need to be enabled for the selected scope to fulfill this security control1. This recommendation can be enforced by the newly released built-in policies “Configure Azure Defender for…” and you can find the “Enforce” button on top of the recommendation page.
Prior the newly released built-in policies to enable Azure Defender, it was necessary to enable Azure Defender for the selected subscriptions and resource plans manually via portal or use the custom policies within Github:
Now the built-in option to enforce the enablement of the Azure Defender plans for all needed resources that can be secured with Azure Defender is done via built-in Azure policies. The policies “Configure Azure Defender for ...” use the DeployIfNotExist effect, which means that as soon as the policy is assigned to a subscription or a Management Group above all new resources that get deployed and are type of the specified Azure Defender plan will have Azure Defender enabled2. All new subscriptions under the specified scope will get the settings automatically, existing ones need to be remediated.
But why does it make sense to enable Azure Defender plans on subscriptions automatically? To answer that questions we need to look at the three pillars of cloud security - Protect, Detect and Response.
Protection of the cloud environment means hardening the security posture by implementing all proactive security configuration to decrease the likelihood of compromising the cloud environment. These proactive actions are described and assessed in Azure Security Center for the Azure environment and make up the overall secure score. As soon as all recommendations are remediated and the Secure Score is at 100%, the Azure environment is hardened and vulnerabilities are remediated to the extent that it is assessable by Azure Security Center and the data it can gather. It is therefore proactively protected but needs to be checked iteratively to secure new resources or implement new recommended security configurations.
When we consider that customers are using a multi-cloud or hybrid cloud strategy, Security Center can only protect Azure as it can only assess Azures security hygiene and configuration. But the goal should be to have a centralized view on the security estate within all cloud platforms & on-premises systems. Luckily, Azure Defender can assess the security configuration in AWS & GCP as well by using the native Azure Defender connectors.
Additionally, when a customer wants to assess the security estate of their on-premises environment to get a unified view on their hybrid cloud, Azure Defender needs to be enabled. Therefore, it is recommended/necessary for customers with a multi-cloud as well as a hybrid cloud environment to enable Azure Defender to be able to PROTECT their holistic cloud environment.
Azure Security Center covers only the first pillar “protect” on securing the overall cloud security posture by being a proactive Cloud Security Posture Management System. Therefore, it makes sense to extend the feature set with solutions to DETECT vulnerabilities and RESPOND to attacks in a timely manner. But these features are limited within Security Center and can easily be extended by enabling the advanced capabilities of Azure Defender.
As a Cloud Workload protection tool, Azure Defender delivers not only protection but also strong detection mechanisms across cloud workloads that are based on advanced security analytics and machine-learning technologies to evaluate events across the entire cloud fabric and is enhanced by data from multiple sources like Microsoft product signals. To be able to secure the specific resource types best, Azure Defender features and detection mechanisms are aligned to them by defined Azure Defender plans per resource-type.
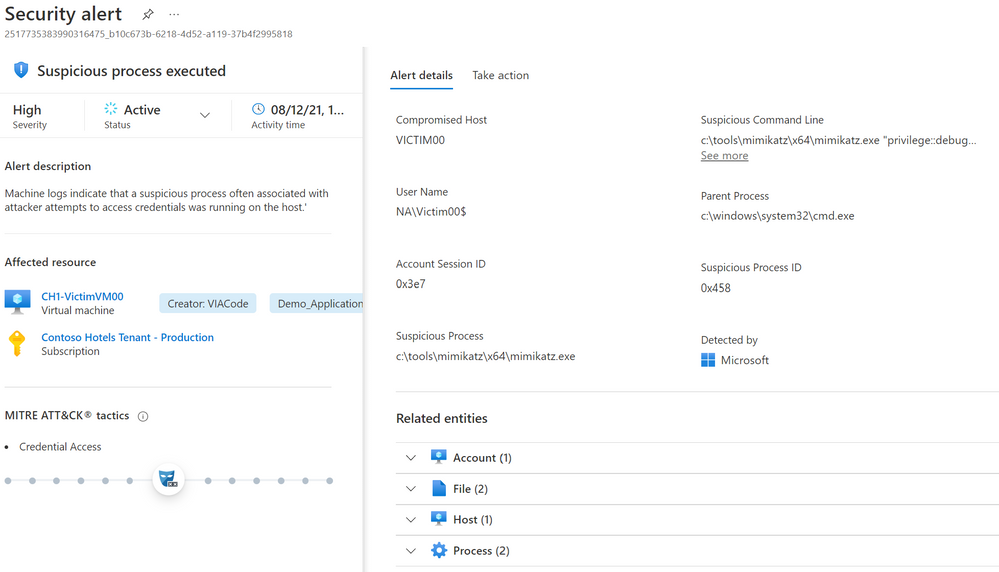
When we take a look into the advanced detection methods of Azure Defender for server, the goal is to identify compromised virtual machines by using behavioral analysis of the event logs of a virtual machine. This means that known patterns of malicious behavior are applied and as soon as there are deviations detected within the logs, it triggers an alert. A good example would be “Suspicious process was executed”. A specific process was flagged as malicious by other data sources as it was used to access credentials by attackers, therefore Azure Defender fires an alert as soon as machine logs indicate that the flagged suspicious process was running on the machine.
As soon as Azure Defender detects an attack or threat it fires security alerts to be able to respond to them. All alerts that are triggered through the advanced detection mechanisms by Azure Defender are listed here and structured by resource-type plan. These alerts describe details of the affected resources, suggested remediation steps, and in some cases an option to trigger a logic app in response.
This leads us to the final pillar, response, as there are various ways to respond to these alerts by using automatic or manual response within Azure Defender.
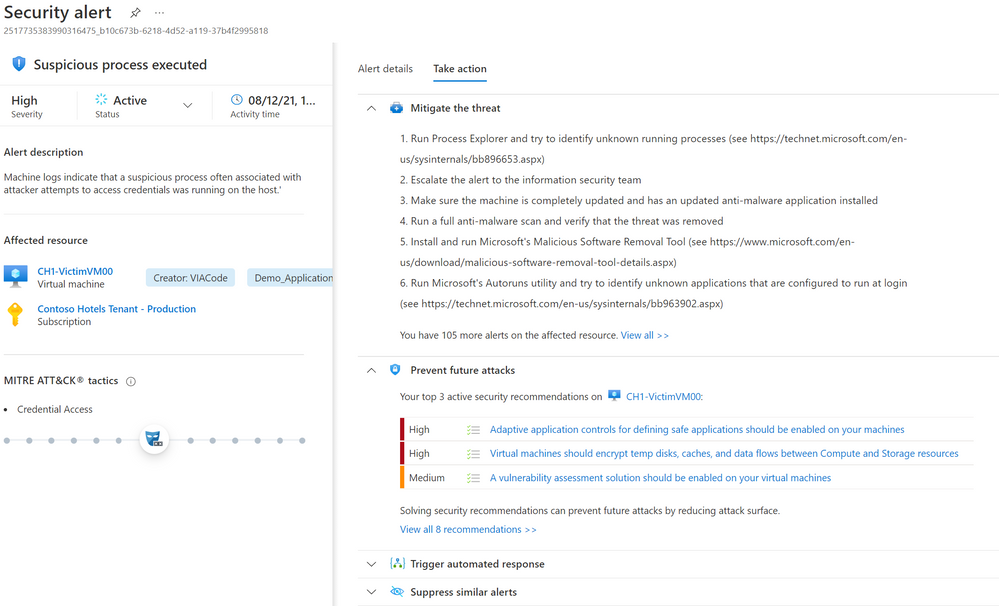
Every security alert within Azure Defender indicates different approaches to responding to the alert within the “Take action” tab. It states a manual response by describing the steps to mitigate the threat as well as pointing out the security recommendation that would have protected the resource and prevented the threat execution. In addition to that for a lot of security alerts there are recommended Logic Apps pre-built as an automated response to mitigate the threat. All Logic Apps that are created to mitigate threats within ASC can be found here. As soon as there have been a RESPONSE action taken within the security alert, it should be marked Dismissed. It is only possible to respond to alerts as soon as they have been triggered through Azure Defender.
This closes the loop on protecting through security configurations, detecting via advanced detection mechanisms and generating an alert to be able to respond manually or through automatic remediation. This makes it inevitable to enable Azure Defender to be able to ensure a complete Security Management system throughout Azure, on-premises and other clouds. With these reasons stated above Microsoft recommends to enforce the enablement of Azure Defender via the newly released Azure policies: “Configure Azure Defender for...”.
This article does not outline the full comparison of Azure Security Center & Azure Defender enabled, which can be found here.
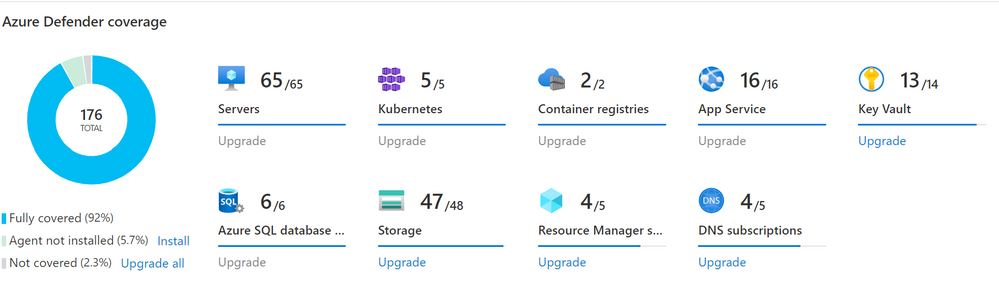
1 Please make sure that you install all needed agents on the machines you want to secure with Azure Security Center & Azure Defender, to not only pay for Azure Defender but also make use of these features. You can find the instructions on how to do this at scale here either through the auto-provisioning feature within ASC or via policy.
2 As the enablement of Azure Defender is done on a subscription scope, it does make sense to only apply it on Management Group or subscription level.
Posted at https://sl.advdat.com/3m4k321