Howdy folks,
I’m excited to share the latest Active Azure Directory news, including updates and new features that will streamline administrator, developer, and user experiences. These updates show our commitment to simplifying secure identity and access management, while also enhancing the kinds of customization and controls you need.
Track risky users and risk detection using diagnostic settings
With diagnostic settings for Azure AD Identity Protection now in public preview, customers can send logs about risk detection and the behavior of risky users to storage accounts, Event Hubs, and Azure Monitor. This makes it easier to track security risks and protect the organization from identity compromise. And they can retain this data beyond the 30-day default period. Customers are able to:
- Track trends in identity compromise within their organization by building custom workbooks
- Query the risk data for specific threats and troubleshoot risk issues in their environment
- Send the risky users and risk detections data to third-party Security Information and Event Management (SIEMs), making it easier for them to plug this data into existing security operations center procedures
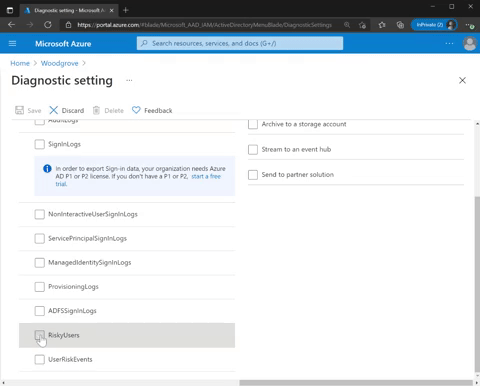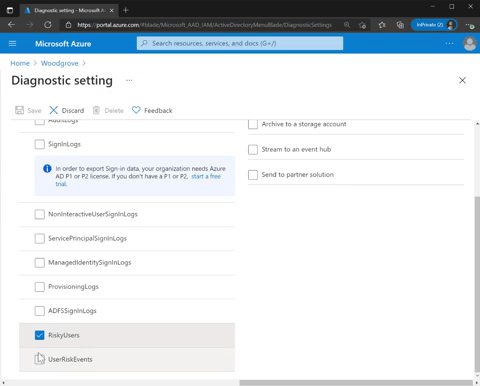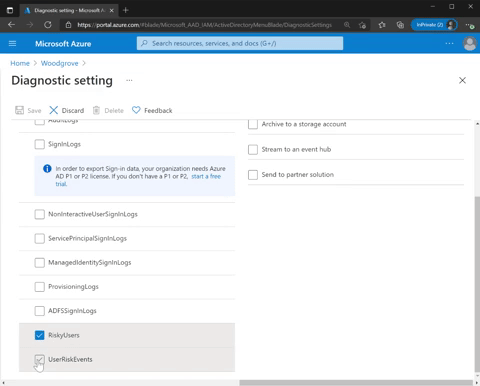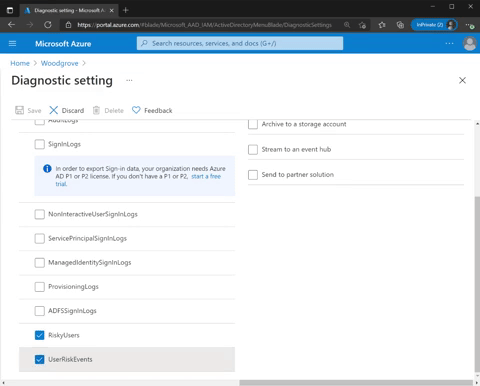
Get more details about diagnostic setting for risk protection and set it up in two easy steps:
- Go to Azure portal > Azure Active Directory, Diagnostic settings > Edit setting.
- Select RiskyUsers for the risky users’ data and UserRiskEvents for the user risk detections data.
Manage role assignments more easily with groups
Assigning roles to Azure AD groups is now easier in Azure AD. Instead of having to assign roles to individual users, a privileged role administrator or global administrator can assign a role to a group. Your existing governance workflow then approves and audits group membership to ensure that only legitimate users are members. This role assignment capability is now generally available.
This also enables the group to act without having to rely on the privileged role administrator or global administrator. Admins can assign an owner to a group for a specific role. The group owner manages group memberships and controls who is assigned the role. Available initially to Azure AD groups, this feature will be extended to on-premises groups in the future.
Store B2C user data within Australia
With Azure AD B2C in Australia now generally available, you can store B2C user data within Australia and benefit from improved latency for apps hosted in the country. Existing customers can try the new feature by searching for B2C in Australia’s Azure portal. New customers can try it by choosing Australia or New Zealand as the Country/Region when creating a new Azure AD B2C tenant.
Share your feedback
We’re always looking to improve Azure AD in ways that benefit IT and users. Often, these updates originate with the suggestions of users of the solution. We’d love to hear your feedback or suggestions for new features or feature updates in the comments or on Twitter (@AzureAD).
Best regards,
Alex Simons (@Alex_A_Simons)
Corporate VP of Program Management
Microsoft Identity Division
Learn more about Microsoft identity:
- Return to the Azure Active Directory Identity blog home
- Join the conversation on Twitter and LinkedIn
- Share product suggestions on the Azure Feedback Forum