Though Microsoft’s Azure Active Directory is the underlying identity platform for Azure resources and Microsoft 365 applications, there are two other identity capabilities with specific functions – Azure AD B2B and Azure AD B2C.
Azure AD B2B lets you allow external users access to your Azure resources and applications by trusting their credentials that have been verified by their own identity provider (including other Azure AD tenants).
Azure AD B2C provides developers with an identity platform separate to your Azure Active Directory tenant, which they can customise to suit the sign-up process and user profile requirements of their application. If your developers are building applications or websites which require consumers or customers to sign in, Azure AD B2C gives them a full-featured Customer Identity and Access Management system, including the ability to custom brand the user experience. So, what do IT Pros need to know about the impact of Azure AD B2C on user identity management and security?
1. Azure AD B2C is a separate tenant
You’ll need to log into Azure with an account that has Contributor access to an existing Subscription, but then the process of provisioning Azure AD B2C creates a new tenant and associated directory. You’ll be able to switch to this using the Directories + Subscriptions filter in the Azure portal, but this keeps all of the B2C Users isolated from any user accounts you’re already managing for your organization in Azure Active Directory. You will then register you applications to be able to use this directory.

For more information, see Technical and feature overview – Azure AD B2C tenant
2. Azure AD B2C supports social identities and other Identity providers
If you have ever signed up to use a website, you might have entered and verified your email address to create an account, or you may have be asked if you’d like to use an existing social identity account to log in with, like Facebook, Google, or a consumer Microsoft Account.

Azure AD B2C supports both of these scenarios, with detailed documentation on connecting a range of popular social platforms but also allows for any identity provider that supports OAuth 1.0, OAuth 2.0, OpenID Connect or SAML. An advantage of OAuth 2.0 identity providers (including Facebook and Google) is the ability for those identity platforms to authenticate the user credentials and pass them through to your application, as well as supporting single sign on.
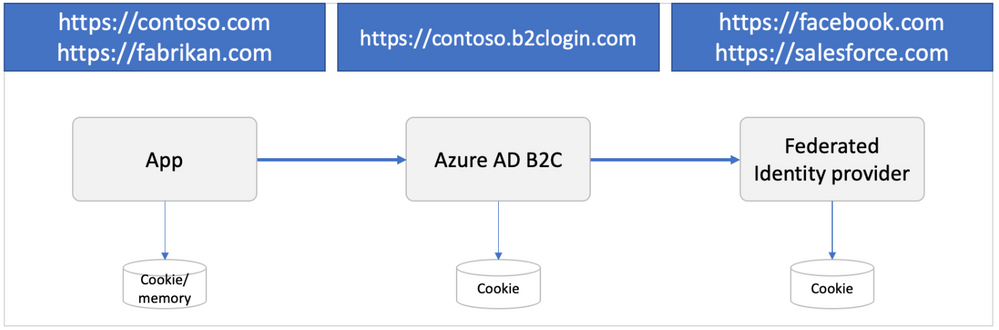
This also means those platforms retain the password management functionality. For more information visit Add an identity provider to your Azure Active Directory B2C tenant and Configure session behaviour in Azure Active Directory B2C
The sign up process also allows developers to ask for additional information to be stored in the user’s profile such as city, country, date of birth or other custom attributes like Loyalty Program Number. For more information on user attributes, visit User profile attributes.
Developers can also define the user experience for different identity-related tasks, such as editing their profile or challenging for MFA. Details can be found at User flows and custom policies.
3. Management has some differences compared to Azure Active Directory
An Azure AD B2C tenant cannot have other Azure resources provisioned in it, like virtual machines or Azure functions. Azure AD features like groups and roles only apply to administrative accounts in the tenant, not to the consumer accounts that are create by the application users. You can use Azure AD security defaults to force all administrative accounts to use Multi Factor Authentication (MFA). For detailed information on supported Azure AD features and more, visit Manage your Azure Active Directory B2C tenant.
You can create or delete consumer accounts via the Azure Portal and reset a user’s password (if they’re not using a social identity sign on). Find the steps at Use the Azure portal to create and delete consumer users in Azure AD B2C.
4. Azure AD B2C allows for some advanced identity features
Beyond the basics of Azure Active Directory, you may have explored advanced identity features like Identity Protection and Conditional Access. Some of these features are available to protect Azure AD B2C accounts, with Azure AD B2C P1 and P2 licensing.
Identity Protection lets you view risky users and risk detections, and can be accessed via the Microsoft Graph API. You can then investigate these detections and decide on any appropriate action, such as blocking users. Note that detections are limited to a small set of risks when a social identity is being used, as it is managed by the external identity provider. For an overview of Azure AD B2C Identity Protection including service limitations, licensing and report details, visit Investigate risk with Identity Protection.
Conditional Access can be used to activate steps (like prompting for an MFA challenge or blocking a sign in), based on the conditions that are evaluated during the sign-in attempt taking place. This can be based on things like user or sign-in risk, or specific locations. Only a subset of Azure AD Conditional Access policies are available. Find all the details at Add Conditional Access to user flows in Azure Active Directory B2C.

Azure AD B2C uses a sophisticated strategy to lock accounts, to help mitigate credential attacks. You can customize the lockout threshold and lockout duration. Learn more at Mitigate credential attacks in Azure AD B2C.
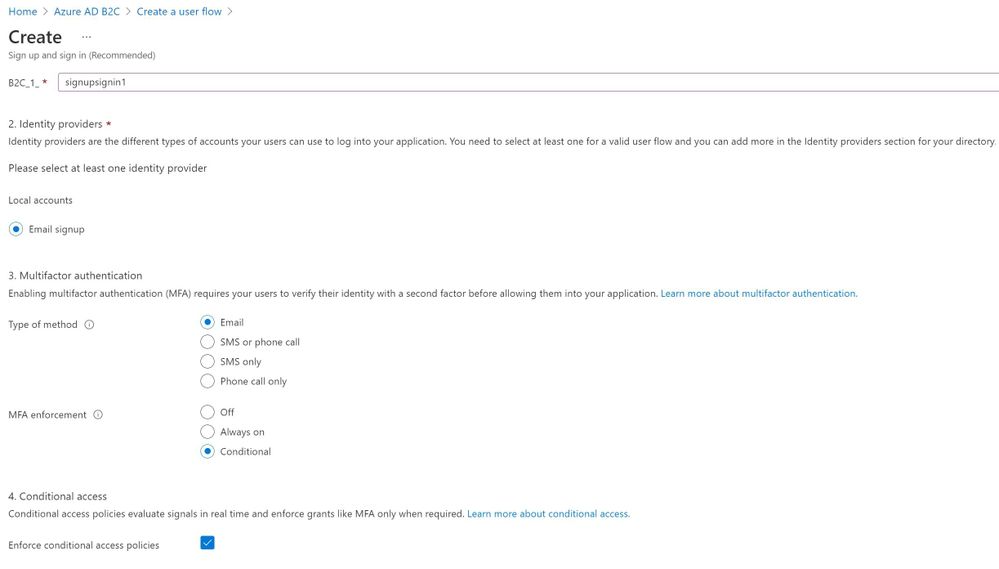
When they register their web application, developers can also set multi factor authentication options, including MFA methods and whether it's enforced on every logon or only challenged for when conditions are met:
5. Azure AD B2C integrates with Azure Monitor and Azure Sentinel
It’s important to note that Azure AD B2C audit log events are only retained for 7 days. If you require a longer retention period, you’ll need to configure a solution to send the audit log events to another retention source, for example downloading it using the Azure Active Directory reporting API or sending the data to an Azure storage account or to Log Analytics.
One benefit of using Log Analytics is that you can then query the data with Azure Monitor. But remember how I said you can’t create an Azure resource, including a Log Analytics Workspace, in an Azure AD B2C tenant? Instead, architect a solution where the Log Analytics Workspace resides in a different tenant, and Azure Lighthouse allows delegated access from the B2C tenant to the LAW resource:

Then you can query the logs with Kusto Query Language, create workbooks, alerts and action groups, and change the data retention period. Visit Monitor Azure AD B2C for detailed steps.
You can also configure Azure Sentinel to use the log data! Take advantage of Microsoft’s analytics and threat intelligence, investigate threats and hunt for suspicious activities and quickly response to incidents, adding Azure AD B2C activities to your bigger security picture. Check out the steps at Tutorial: How to perform security analytics for Azure AD B2C data with Azure Sentinel.
NOTE: Registering web applications for use with Azure AD B2C also involves creating an application secret. If performing secret rollovers is part of your IT Pro role, these application secrets should also be included. Learn more at Create a client secret.
Learn more:
I hope this article has provided you with a good overview of the benefits and capabilities of Azure AD B2C, so you can support a request from your developers to provide websites and applications with log-in capabilities for your own external customers!
About Azure AD B2C
Recommendations and best practices for Azure Active Directory B2C
MS Learn - Enable secure access to apps for external users with Azure AD B2C
Posted at https://sl.advdat.com/3iy9bah