Alerts are now optional for the file custom IoC “block and remediate” action. Additionally, the IoC API scheme and portal description was updated to more accurately describe whether the response action taken was a block or “block and remediate”.
Up until now, every blocked and remediate file IoC event raised security alerts to the SOC (security operations center) team. However, some organizations were flooded with unwanted security alerts. Today we’re announcing a public preview that allows customers to determine if such events require security team awareness, and if they do, the ability to set specific parameters to be met in order for an alert to be raised. In addition, we are updating the IoC API schema and description shown in the portal to more accurately describe whether the response action taken was a block or “block and remediate”.
Updated list of available IoC actions
When creating a new indicator (IoC), one or more of the following actions are now available:
- Allow – the IoC will be allowed to run on your devices.
- Audit – an alert will be triggered when the IoC runs.
- Block execution - the IoC will not be allowed to run.
- Block and remediate - the IoC will not be allowed to run and a remediation action will be applied to the IoC.
More specifically, the table below shows exactly which actions are available per indicator (IoC) type:
|
IoC type |
Available actions |
|
File |
· Allow · Audit · Block and remediate |
|
IP address |
· Allow · Audit · Block execution |
|
URL\ domain |
· Allow · Audit · Block execution |
|
Certificate |
· Allow · Block and remediate |
For example, the original three IoC response actions were “allow,” “alert only,” and “alert and block.” As part of the update, the functionality of pre-existing IoCs will not change. However, the indicators were renamed to match the current supported response actions:
- The “alert only” response action was renamed to “audit” with the generate alert setting enabled.
- The “alert and block” response was renamed to “block and remediate” with the optional generate alert setting
The IoC API schema and the threat ids in advance hunting have been updated to align with the renaming of the IoC response actions. The API scheme changes apply to all IoC Types.
Indicators can be imported through Microsoft Defender for Endpoint APIs: List Indicators API | Microsoft Docs. The indicator action types supported by the API are AlertAndBlock, Allow, Audit, Alert, Warn, BlockExecution, BlockRemediation.
Note: The prior response actions (AlertAndBlock, and Alert) will be removed once the feature has reached GAed. The estimated GA date with grace period is end of October 2021. We advise updating any existing templates or scripts as soon as possible.
|
Note: The format for importing new indicators (IoCs) has changed according to the new updated actions and alerts settings. We recommend downloading the new CSV format that is found at the bottom of the import panel.
|

|
Alerting on file blocking actions
In Microsoft 365 Defender, go to Settings > Endpoints > Indicators > add new File hash
Choose to Block and remediate the file
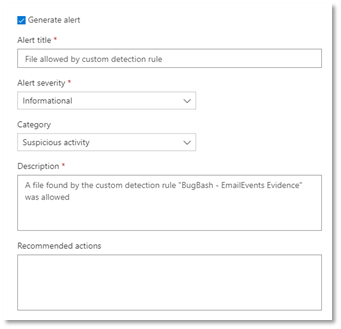
Choose if to Generate an alert on the file block event and define the alerts settings:
- The alert title
- The alert severity
- Category
- Description
- Recommended actions
Alert settings for file indicators
For more information about custom indicators handling in Microsoft Defender for Endpoint, see (Create indicators).
Summary
We’re excited to hear your feedback as you explore the new IoC capabilities, and we will continue to update the documentation throughout the preview.
If you’ve enabled public preview features, you can check out the new IoC functionality today! If not, we encourage you to turn on preview features for Microsoft Defender for Endpoint to get access to the newest capabilities. These features can be turned on in the Microsoft Defender Security Center or the Microsoft 365 security center.
Resources for using IoCs:
- IoC support documentation
- Overview of unified IoC experience in Microsoft Defender for Endpoint
- Pushing IoCs to Microsoft Defender for Endpoint
- How to integrate MISP with Microsoft Defender for Endpoint
Microsoft Defender for Endpoint is an industry leading, cloud powered endpoint security solution offering endpoint protection, endpoint detection and response, vulnerability management, and mobile threat defense. With our solution, threats are no match. If you are not yet taking advantage of Microsoft’s unrivaled threat optics and proven capabilities, sign up for a free Microsoft Defender for Endpoint trial today.
Posted at https://sl.advdat.com/3sF2qXV