Recent reports show the high extent to which information workers are utilizing cloud apps while doing their everyday tasks. In an average enterprise, there are more than 1500 different cloud services used, where less than 12% of them are sanctioned or managed by the IT teams. Considering that more than 78GB of data is being uploaded monthly to risky apps we conclude that most organizations are exposed to potential data loss or risks coming out of these cloud applications.
Shadow IT usage of risky apps is usually mitigated by a strict approach of blocking any usage of these cloud apps that do not meet certain risk criteria, this approach is already enabled today by using Microsoft’s Cloud App Security Shadow IT Discovery capabilities with its native integration with Microsoft Defender for Endpoints and it’s native integration with other 3rd party network appliances.
But what about apps that are widely used by employees and enable their productivity (especially in the Work from home/Covid-19 era) and their risk is not conclusive enough for a strict block. To enable the delicate balance between employee’s productivity, and the need for risk and compliance awareness, organizations need to take a gradual approach:
- Warn users that this app is not recommended/allowed but allows users to bypass to enable productivity.
- IT can monitor access and bypasses such apps and learn usage trends and importance.
- IT can offer sanctioned and managed alternatives for the users by creating a contextual company web page that provides sanctioned alternatives in the organization.
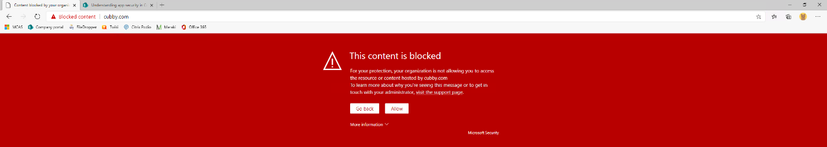
We are pleased to announce the public preview for a new endpoint-based capability to allow management and control of Monitored cloud applications, manage these Monitored applications applying soft block experience for end-users when accessing these apps. Users will have an option to bypass the block.
IT admins will be able to add a dedicated custom redirect link so users can get more context on why they were blocked in the first place and what valid alternatives do they have for such apps in the organization.
Besides enabling the soft block experience, admins will be able to continuously monitor these apps and understand how many of the users adhered to the block and chose other alternatives, or, decided to bypass the block and continue using the app – this will serve as a strong indication, org-wide, whether this app is necessary and should be considered for deeper management by IT.
By adopting a more gradual and less strict approach for blocking cloud applications, IT organizations can reduce their overhead of handling exception requests, but in parallel drive employee awareness.
How does it work?
In Cloud App security, tag the targeted app as Monitored.
The corresponding URL/Domains indicators will appear in the Microsoft Defender for Endpoints security portal as a new URL/Domain indicator with action type Warn.
When a user attempts to access the Monitored app, they will be blocked by Windows defender network protection but will allow the user to bypass the block or get more details on why he was blocked by redirecting him to a dedicated custom web page managed by the organization.
Over time, an IT admin can monitor the usage pattern of the app in Cloud App Security's discovered app page and monitor how many users have bypassed the warning message.
Get started
After you have verified that you have all the integration prerequisites listed in this article, follow the steps below to start warning on access to Monitored apps with Cloud App Security and Microsoft Defender for Endpoint.
Step 1
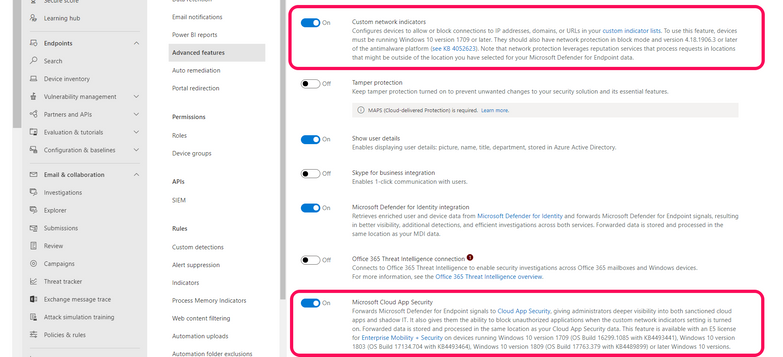
In Microsoft 365 Defender, go to settings > Endpoints > Advanced features and enable Microsoft Cloud App Security integration and Custom network indicators.
Step 2
In the Microsoft Cloud App Security portal, go to Settings > Microsoft Defender for Endpoint:
- Mark the checkbox to enable blocking of endpoint access to cloud apps marked as unsanctioned in Cloud App Security
- [Optional] Set a custom redirect URL for a company coaching page.
- [Optional] Set the Bypass duration time after which the user will get warned once again on access to the app.
More info and feedback
- Get started with our technical documentation:
- Cloud App Security documentation
- Microsoft Defender for Endpoint documentation
- Cloud App Security and Defender for Endpoint integration docs
- As always, we want to hear from you! If you have any suggestions, questions, or comments, please visit us on our Cloud App Security and Microsoft Defender for Endpoint Tech Community pages.
- Uncover your blind spots: seamlessly control cloud usage risks to your organization
-
Microsoft Cloud App Security - Manage and control your Shadow IT - YouTube
-
Microsoft Cloud App Security - Shadow IT Discovery (Solution Sheet)
Posted at https://sl.advdat.com/3CPhWFg