Introduction
This article is part of our Azure Defender PoC Series which provides you with guidelines on how to perform a successful proof of concept for a specific Azure Defender plan. For a more holistic approach where you need to validate Azure Security Center and Azure Defender, please read How to Effectively Perform an Azure Security Center PoC.
Azure Defender is the Cloud Workload Protection Platform (CWPP) built into Azure Security Center, which provides security alerts and advanced threat protection for virtual machines, SQL databases, containers, web applications, your network, and more.
Azure Defender for Servers adds threat detection and advanced defenses for your Windows and Linux machines.
Planning
As part of your Azure Defender for Servers PoC, you need to identify the use case scenarios you want to validate. Azure Defender for Servers includes several threat detection and protection capabilities, some of which are only available for Azure VMs, like Just-in-time VM access, and some can detect potentially malicious activity on your servers, regardless of what platform they are running on – Azure, AWS, GCP, on-premises, etc. You can find a list of all components and their description in our documentation.
Every component has different prerequisites and requires different technics and tools for validation.
While planning your PoC, you need to take into account that many of the Azure Defender for Servers capabilities rely on the Log Analytics agent that collects variety of data from your servers. You can learn more about how Azure Security Center (ASC) uses the LA agent and what deployment scenarios are available to you in this article.
If you decide to make your on-premises servers or machines hosted on other clouds, e.g. AWS or GCP, part of the PoC, you need to choose how you are going to connect them to Azure so that Azure Defender can discover them and start protecting. There are two ways of doing this: connecting the servers from the Azure portal or using Azure Arc (which is the recommended option). Please keep in mind that certain Azure Defender capabilities in this case, like vulnerability assessments powered by Qualys or the integration with Microsoft Defender for Endpoint, are only supported for the Arc-connected machines.
Once your servers are onboarded to Security Center you will be able to deploy the Qualys vulnerability assessment scanner if you decide to make vulnerability assessment scanning part of your PoC.
Remember that you have 30-day free trial to test Azure Defender for Servers. Any usage beyond 30 days will be automatically charged as per the pricing scheme here.
Preparation and Implementation
In order to enable Azure Defender for Servers, you need a user account that has at least the Security Admin role. For more information about roles and privileges, read this article.
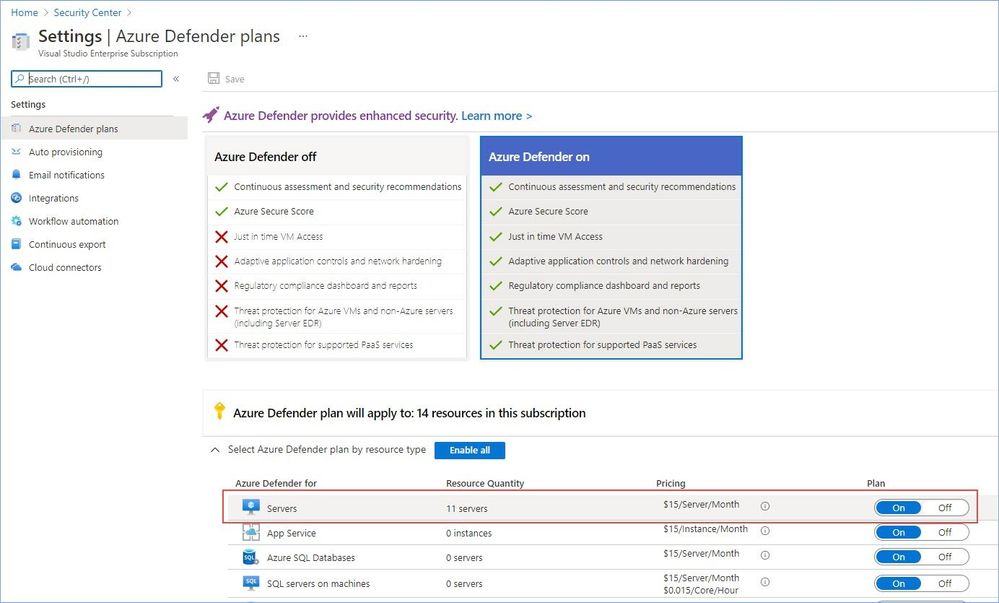
Your first step is to enable Azure Defender on the subscription(s) you are conducting the PoC in and make sure that Azure Defender for Servers plan is selected.
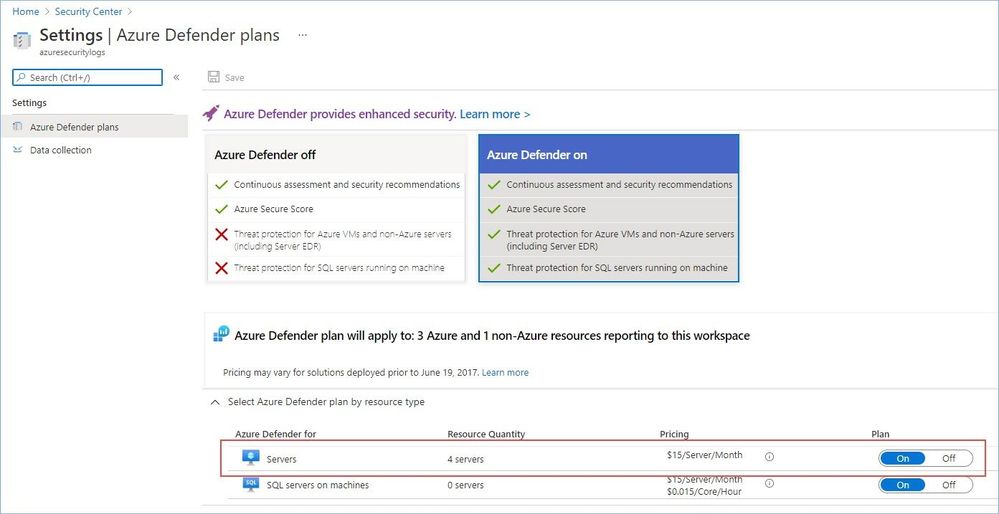
Next, you also need to enable Azure Defender on a Log Analytics workspace you are planning to use to store data collected from your servers by the Log Analytics agent.
If you are testing Azure Defender for Servers on your Azure virtual machines and you have configured auto-provisioning of the LA agent – you are all set – all existing and newly provisioned VMs will be automatically configured to collect and send data to a selected LA workspace.
If you have decided to deploy the LA agent manually, please review this article.
Validation
Since Azure Defender for Servers has many capabilities, we are going to group them based on different use case scenarios.
Scenario 1: Attack Surface Reduction
Threat actors actively look for accessible machines with open management ports, like RDP or SSH. As a matter of fact, just by leaving your VM with such ports open to the Internet for a day or two (sometimes even a couple of hours) is enough to become a victim of a brute-force attack and receive a security alert like the one below (make sure you use strong passwords):
Note: Do not forget to configure email notifications to get alerts when ASC detects new suspicious activities or attacks.
JIT VM access locks down the inbound traffic to your Azure VMs, reducing exposure to attacks while providing easy access to connect to VMs when needed. To configure and validate JIT VM access feature please follow this guidance.
You may also consider using our playbooks for Windows and Linux to simulate certain malicious activities and trigger alerts.
Adaptive Network Hardening (ANH) uses machine learning to analyze network traffic to and from your machines and provides recommendations (see the example below) to harden the Network Security Groups (NSG) rules. For that reason, it requires at least 30 days of traffic data to build and train a ML model. Please keep this fact in mind when validating this feature.
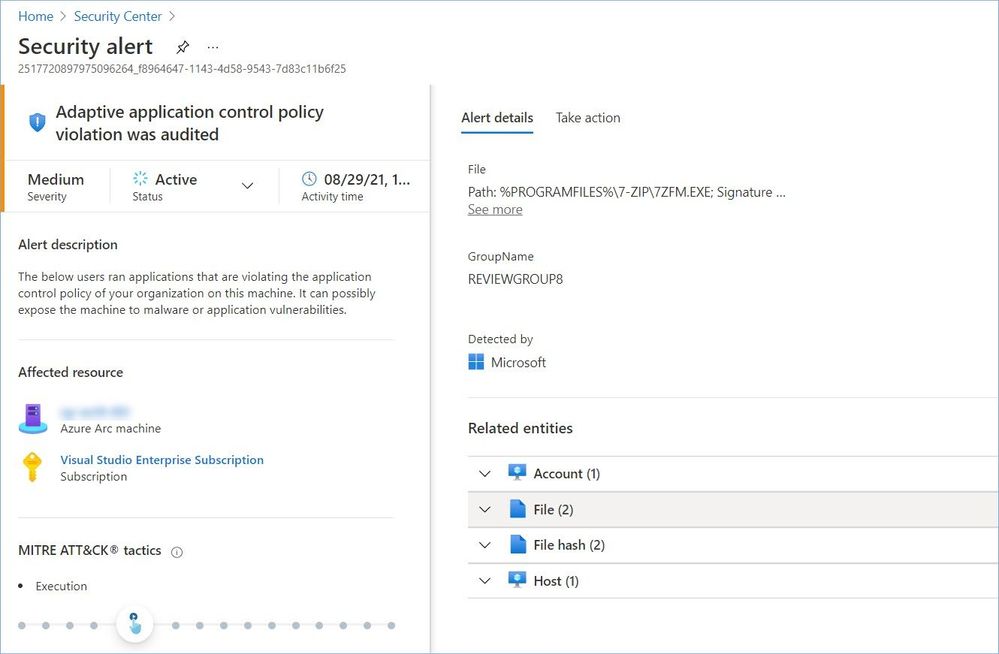
Adaptive Application Controls (AAC) also use machine learning that needs at least two weeks of data, to analyze the applications running on your servers and create a list of known-safe software. When you've enabled and configured adaptive application controls, you'll get security alerts (see the image below) if any application (other than the ones you've defined as safe) kicks in. Please use this article to configure and validate this feature.
File integrity monitoring (FIM), also known as change monitoring, examines operating system files, Windows registries, application software, Linux system files, and more, for changes that might indicate an attack. Please use this guide to help you configure and verify FIM.
Scenario 2: Integration with an EDR solution
If you have properly enabled and configured the integration with Microsoft Defender for Endpoint (MDE), all new servers connected to ASC will be automatically onboarded to MDE, and you will be able to see them on the Microsoft 365 Defender portal. To verify that MDE alerts successfully flow to ASC you can use a test alert as described here.
Note: This alert is generated as Informational, so you would need to change the default severity filter in the ASC security
alerts dashboard to see that alert.
Scenario 3: Vulnerability Assessment
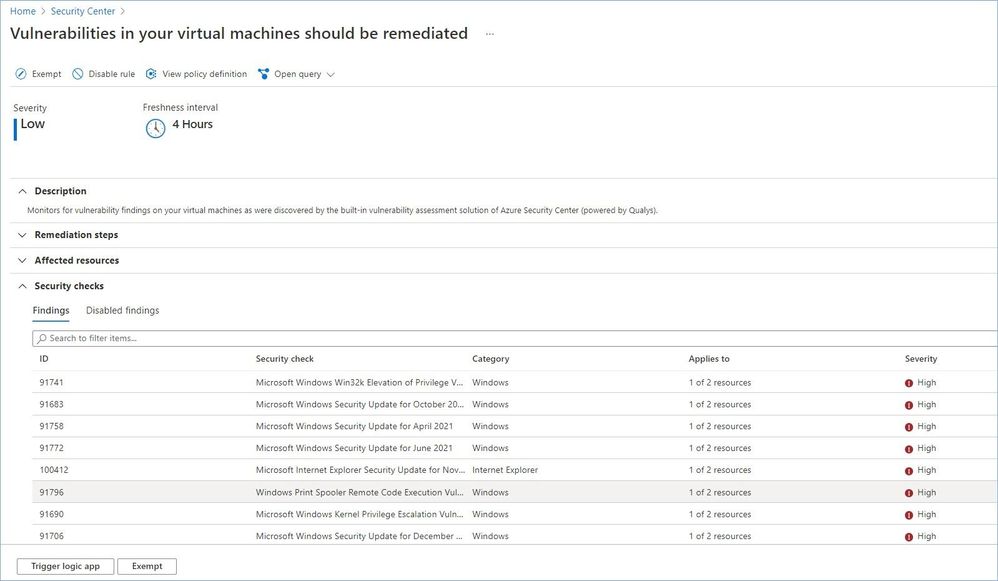
Once you have deployed the Vulnerability assessment solution (powered by Qualys) to your servers, the VA scanner will automatically start scanning your machines every 12 hours and report findings to Security Center (see the image below). Learn more about how to deploy the scanner and how to analyze and remediate vulnerabilities.
As an alternative, you can generate sample alerts to validate Azure Defender for Server alerts. Please refer to our documentation for a complete list of all analytics/alerts available for both Windows and Linux machines.
Conclusion
By the end of this PoC, you should be able to determine the value of this solution and the importance to have this level of threat detection for your servers.
P.S. Subscribe to our Azure Security Center and Azure Defender Newsletter to stay up to date on helpful tips and new releases and join our Tech Community where you can be one of the first to hear the latest Azure Security Center news, announcements and get your questions answered by Azure Security experts.
Many thanks to my friend and colleague @Yuri Diogenes for reviewing the article.
Posted at https://sl.advdat.com/3tW53oM