We place a high priority on our customers trust in Microsoft Defender for Office 365 and we know that to earn that trust, we need to take measures to make it seamless for SecOps professionals to assess the security of their Office 365 with a reporting tool that supports a data rich environment. Customizable filters and consistent reporting of email security details are essential in the cyber security space where malicious and credential phishing emails are the #1 attack vector used by bad actors.
That’s why we’re bringing you an improved reporting experience in Microsoft Defender for Office 365. These new reporting features and improvements will help refine SecOps professional’s workflows when assessing Office 365 security effectiveness. Some of those features and improvements include:
- Retirement of outdated reports
- Revamp of legacy data computation logic
- Addition of new filtering attribute
- Data oriented email detail panel
New evolved reporting
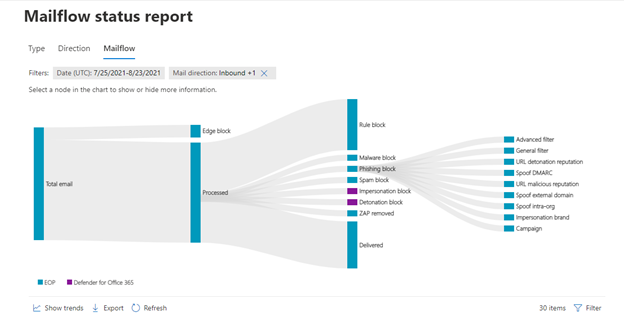
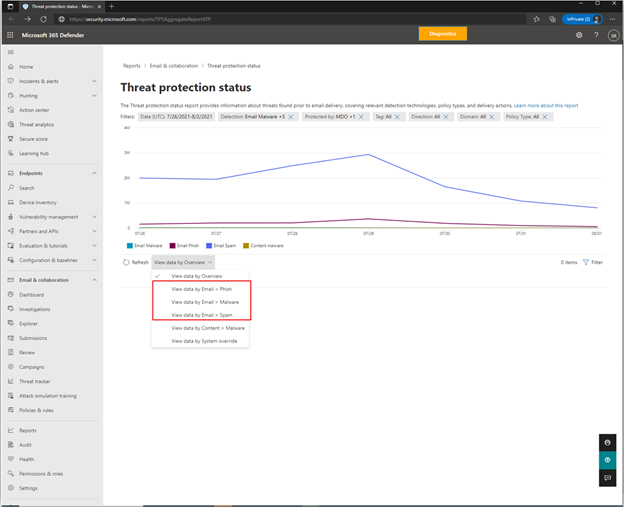
After receiving feedback from our customers, we’ve decided to make the reporting experience easier by consolidating a few existing reports and adding new views to the threat protection status report and the Mail flow status report. As a result, we’re launching a new spam view in the threat protection status report. We've also updated the mail flow status report, which will make the report easier to visualize, and will be available later this month. Deprecated reports include the malware email detection report, the spam report, the safe attachment file types, and deposition report, the sent and received email report, and the URL trace report that previously lived in the exchange admin center. Below you’ll find screenshots of what some of the new views will look like.
Figure 1: Previous Funnel view
Figure 2: New "Sankey” view in Mailflow status report (coming soon)
Figure 3: New spam view in the threat protection status report
Addition of new filtering attributes
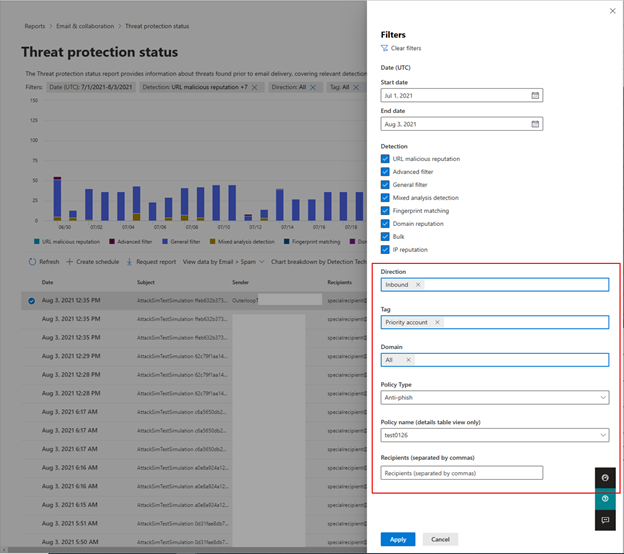
In order for SecOps to focus the scope of their assessment with a lot more granularity, we are providing security professionals the ability to filter data by organization domain, policy type and name, priority account user tag, recipient address and email directionality (inbound and outbound). Check out the screenshot highlighting the addition of this new filtering attribute below.
Figure 4: New filtering attributes in the Threat protection status report
Data oriented email detail panel
Earlier this year we launched the email entity page, which gives SecOps a 360-degree view of an email, putting all the relevant details in the hands of the analyst. We are now replacing the email details panel in the threat protection status report with a panel that provides the same in-depth view of each email, which will bolster SecOps confidence in their day-to-day assessment. You can view how much simpler the new details flyout is in the screenshot below.
Figure 5: Email summary in the threat protection status report
Stay tuned!
We’re continuing to improve the reporting experience and workflow for security teams. A few improvements you can expect to see in the coming months include a greater than 90-day data retention period, and PowerBI and reporting API integration. We’re excited to offer this enhanced reporting experience for customers to better assess email security trends within their business over time.
Do you have questions or feedback about Microsoft Defender for Office 365? Engage with the community and Microsoft experts in the Defender for Office 365 forum.
Posted at https://sl.advdat.com/3hS3qDU