Device Control Device Installation update
We are excited to announce the general availability of a new device installation policy which will dramatically simplify the management of the device installation feature.
This policy setting will change the evaluation order in which Allow and Prevent policy settings are applied when more than one install policy setting is applicable for a given device. The policy setting is called “Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria.”
Enable this policy setting to ensure that overlapping device match criteria are applied based on an established hierarchy, such that more specific match criteria supersede less specific match criteria. The hierarchical order of evaluation for policy settings that specify device match criteria is as follows:
- Device instance IDs > Device IDs > Device setup class > Removable devices
Note: The "Prevent installation of devices not described by other policy settings" policy setting has been replaced by the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting for supported Windows 10 versions. We recommend using the "Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria" policy setting when possible.
This policy supports Group Policy and Intune.
How to deploy the policy via Intune
In Microsoft Endpoint Manager (https://endpoint.microsoft.com/)
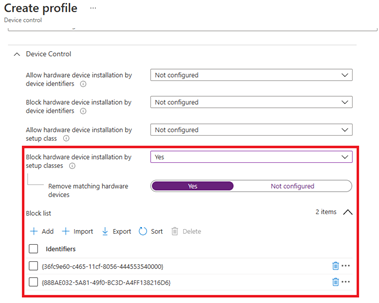
- Configure Prevent installation of devices using drivers that match these device setup classes. Go to Endpoint security > Attack surface reduction > Create Policy > Platform: Windows 10 and later, and Profile: Device control.
- {36fc9e60-c465-11cf-8056-444553540000}: USB Bus Devices (hubs and host controllers. This class includes USB host controllers and USB hubs, but not USB peripherals. Drivers for this class are system-supplied.
- {88BAE032-5A81-49f0-BC3D-A4FF138216D6}: USB Device. This class includes all USB devices that do not belong to another class. It is not used for USB host controllers and hubs.
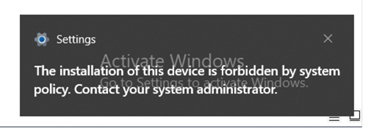
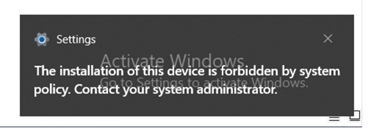
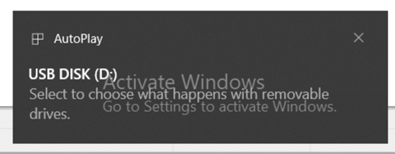
Before you finish the configuration, if you plug in a USB device, you will see following error:
Proceed through the next few steps to finish the configuration.
- Enable Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria
- Configure Support for OMA-URI only for now.
Go to Devices > Configuration profiles > Create profile > Platform: Windows 10 and later, and Profile: Custom
- Configure Support for OMA-URI only for now.
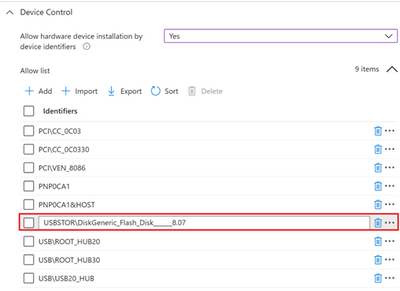
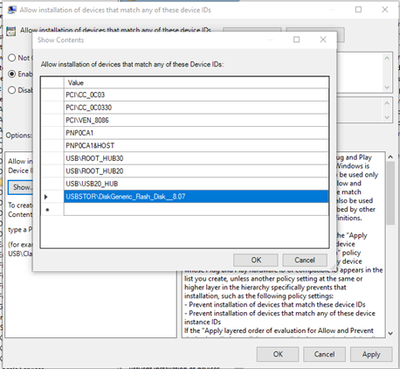
- Enable and add allowed USB Instance ID – Allow installation of devices that match any of these device IDs
- Update the Device control profile from step 1.
Adding PCI\CC_0C03; PCI\CC_0C0330; PCI\VEN_8086; PNP0CA1; PNP0CA1&HOST; USB\ROOT_HUB30; USB\ROOT_HUB20; USB\USB20_HUB in the above screen capture is required because it is not enough to enable only a single hardware ID in order to enable a single USB thumb-drive. You have to ensure all the USB devices that precede the target one are not blocked (and instead allowed) as well. You can open Device Manager and change view to Devices by connections to see the way devices are installed in the PnP tree. In our case, the following devices must be allowed so the target USB thumb-drive could be allowed as well:
- “Intel(R) USB 3.0 eXtensible Host Controller – 1.0 (Microsoft)” > PCI\CC_0C03
- “USB Root Hub (USB 3.0)” > USB\ROOT_HUB30
- “Generic USB Hub” > USB\USB20_HUB
Note: Some devices in the system have several layers of connectivity to define their installation on the system. USB thumb-drives are such devices. Thus, when looking to either block or allow them on a system, it is important to understand the path of connectivity for each device. There are several generic Device IDs that are commonly used in systems and could provide a good start to build an ‘Allow list’ in such cases. See below for the list:
- PCI\CC_0C03; PCI\CC_0C0330; PCI\VEN_8086; PNP0CA1; PNP0CA1&HOST (for Host Controllers)/ USB\ROOT_HUB30; USB\ROOT_HUB20 (for USB Root Hubs)/ USB\USB20_HUB (for Generic USB Hubs)/
Specifically for desktop machines, it is very important to list all the USB devices that your keyboards and mice are connected through in the above list. Failing to do so could block a user from accessing their machine through HID devices.
Different PC manufacturers sometimes have different ways to nest USB devices in the PnP tree, but in general this is how it is done.
When you plug in the USB drive now, you can see that it is allowed and available.
How to deploy the policy via Group Policy
Under Administrative Templates > System > Device Installation > Device Installation Restrictions:
- Configure Prevent installation of devices using drivers that match these device setup classes:
- {36fc9e60-c465-11cf-8056-444553540000}: USB Bus Devices (hubs and host controllers), this class includes USB host controllers and USB hubs, but not USB peripherals. Drivers for this class are system-supplied.
- {88BAE032-5A81-49f0-BC3D-A4FF138216D6}: USB Device, this includes all USB devices that do not belong to another class. This class is not used for USB host controllers and hubs.
Before you have finished the configuration, when you plug in a USB, device, you will see following error:
- Enable Apply layered order of evaluation for Allow and Prevent device installation policies across all device match criteria
- Enable and add allowed USB Instance ID – Allow installation of devices that match any of these device IDs
Adding PCI\CC_0C03; PCI\CC_0C0330; PCI\VEN_8086; PNP0CA1; PNP0CA1&HOST; USB\ROOT_HUB30; USB\ROOT_HUB20; USB\USB20_HUB on above screen capture is required because it is not enough to enable only a single hardware ID in order to enable a single USB thumb-drive. You have to ensure all the USB devices that precede the target one are not blocked (allowed) as well. You can open Device Manager and change view to ‘Devices by connections’ to see the way devices are installed in the PnP tree. In our case, the following devices have to be allowed so the target USB thumb-drive could be allowed as well:
- “Intel(R) USB 3.0 eXtensible Host Controller – 1.0 (Microsoft)” -> PCI\CC_0C03
- “USB Root Hub (USB 3.0)” -> USB\ROOT_HUB30
- “Generic USB Hub” -> USB\USB20_HUB
Note: Some devices in the system have several layers of connectivity to define their installation on the system. USB thumb-drives are such devices. Thus, when looking to either block or allow them on a system, it is important to understand the path of connectivity for each device. There are several generic Device IDs that are commonly used in systems and could provide a good start to build an ‘Allow list’ in such cases. See below for the list:
PCI\CC_0C03; PCI\CC_0C0330; PCI\VEN_8086; PNP0CA1; PNP0CA1&HOST (for Host Controllers)/ USB\ROOT_HUB30; USB\ROOT_HUB20 (for USB Root Hubs)/ USB\USB20_HUB (for Generic USB Hubs)/
Specifically for desktop machines, it is very important to list all the USB devices that your keyboards and mice are connected through in the above list. Failing to do so could block a user from accessing its machine through HID devices.
Different PC manufacturers sometimes have different ways to nest USB devices in the PnP tree, but in general this is how it is done.
When you plug in the USB device now, you’ll see that it is allowed and available.
View Device Control Removable Storage Access Control data in Microsoft Defender for Endpoint
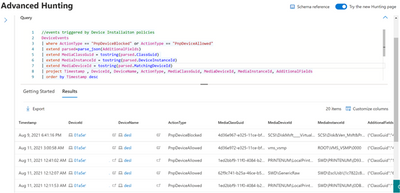
The Microsoft 365 Defender portal shows removable storage blocked by the Device Control Device Installation. To access advanced hunting in the Microsoft 365 Defender portal, you must have a license that includes Microsoft Defender for Endpoint for reporting to be enabled. Go to Advanced hunting, and then use the following example query:
For more information, see our documentation: Microsoft Defender for Endpoint Device Control Device Installation | Microsoft Docs.
We’re excited to deliver these new device control functionalities to you. To experience these capabilities in public preview, we encourage you to turn on preview features for Microsoft Defender for Endpoint today. As always, we welcome your feedback and look forward to hearing from you! You can submit feedback directly to our team through the portal.
Microsoft Defender for Endpoint is an industry-leading, cloud-powered endpoint security solution offering vulnerability management, endpoint protection, endpoint detection and response, and mobile threat defense in a single unified platform. With our solution, threats are no match. If you are not yet taking advantage of Microsoft’s unrivaled threat optics and proven capabilities, sign up for a free trial of Microsoft Defender for Endpoint today.
Microsoft Defender for Endpoint team
Posted at https://sl.advdat.com/2Vs8SFl