A great way to learn PowerShell is to set up a scenario in the Azure portal, then try different PowerShell commands to see if you can get the same results. In this article, we'll use Azure Role Based Access control, as it's both visible in the Azure Portal and we have some PowerShell commands for it.
The scenario: What Role Based Access Control does somebody have?
If you’re taking over an existing Azure environment, or if you organization has been running Azure for a while without enforced consistency of your Role Based Access Control, you might want to explore your existing RBAC assignments at scale or query the permissions for a specific user. RBAC assignments display in the Access control (IAM) blade of Azure resources, resource groups, subscriptions. Because you can assign a role to a user (or group) on an individual resource, their roles and permissions across your Azure environment may vary, and it’s time consuming to check the IAM blade of everything.
Fortunately, we can use PowerShell commands and different display formats, to get the data we want. For the purposes of learning PowerShell, you can use the Azure portal to set up RBAC for different test users (and as part of group memberships) on your resources, resource groups and subscription, so you know what results the PowerShell commands should return.
To keep things simple, I’m running these commands in Cloud Shell inside the Azure Portal.
PowerShell: Get-AzRoleAssignment
Azure RBAC is supported by a number of PowerShell commands, but for this scenario our friend is "Get-AzRoleAssignment".
Looking at the structure of PowerShell, because this is a "Get" command, it's going to query Azure for some information and return the results to us. "AzRoleAssignment" is the base for this command. The command also has a "New-" variation, for adding a new assignment, and a "Remove-" variation for removing a role assignment.
Note: If you see older blogs or scripts using "Get-AzureRmRoleAssignment", that was an earlier name for this command before the Az updates. You can often replace the AzureRm bit with just Az, but not in every case as some commands have been deprecated.
If you have multiple subscriptions, Cloud Shell will default to one of them, and your commands will query that subscription and it's associated resources. You can run "Get-AzContext" to see which subscription is selected, and run "Set-AzContext -SubscriptionName "My other subscription"" to change to a different one. (Note I've placed the actual name of my other subscription in it's own set of brackets because it has spaces in it).
Let's start by just running this command and getting a list of all of the RBAC assignments:
Get-AzRoleAssignment
Next, let's narrow that down so we are only looking for role assignments for one particular user. The Get-AzRoleAssignment command has a range of different parameters we can add which will act as a filter. We'll use SignInName, which you can find in the user's details in Azure Active Directory, if you don't know the exact format (and replace my steve.l example name):
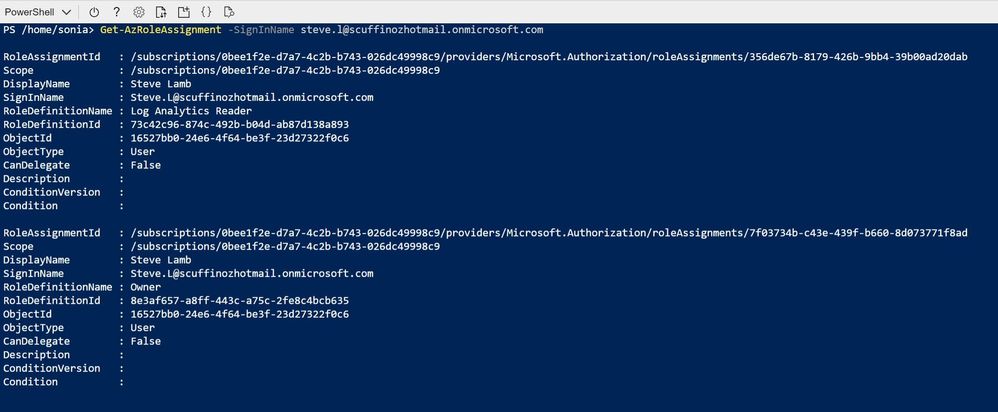
Get-AzRoleAssignment -SignInName steve.l@scuffinozhotmail.onmicrosoft.com
This gives us a long list of Steve's role assignments:
Now I want to play with the formatting to make it a little more readable onscreen.
I can format the output of this PowerShell command a few different ways, including as a list or as a table. The output above show sme all of the information that is returned by the query though, so I can use that to further refine the display:
Get-AzRoleAssignment -SignInName steve.l@scuffinozhotmail.onmicrosoft.com | FL DisplayName, RoleDefinitionName, Scope
I'm using the 'pipe' character of | (which is Shift + \ on my keyboard), then the short version of the "format-list" command, then I'm listing just the properties I want to be displayed (DisplayName, RoleDefinitionName and Scope). The pipe tells the first command to send it's output to the second command.

For more formatting command examples, visit Using Format Commands to Change Output View.
Hmm, that could still be a pretty long list if Steve had more role assignments. Let's try a table view instead with "format-table" or FT for short:
Get-AzRoleAssignment -SignInName steve.l@scuffinozhotmail.onmicrosoft.com | FT DisplayName, RoleDefinitionName, Scope
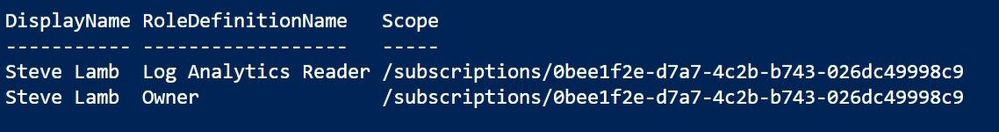
That's better! So, Steve has a pretty high level of access at the top level of my subscription (Owner) plus a Log Analytics Reader role assignment which isn't needed - I can go and tidy that up. But if I run that same command for a different user, I'm seeing a different scope:

Sonia's account is showing the scope as the SCuffSubsMG, not the subscription ID. That's because her Owner access to the current subscription is determined by a role assignment that has been added at the management group level, and as this subscription belongs to that management group, the role assignment is inherited too.
There's one more important thing we need to include - what if our user is a member of a group that has been assigned a role? Our commands so far won't include that. We need to add "-ExpandPrincipalGroups".
Get-AzRoleAssignment -SignInName sarah.g@scuffinozhotmail.onmicrosoft.com -ExpandPrincipalGroups | FL DisplayName, RoleDefinitionName, Scope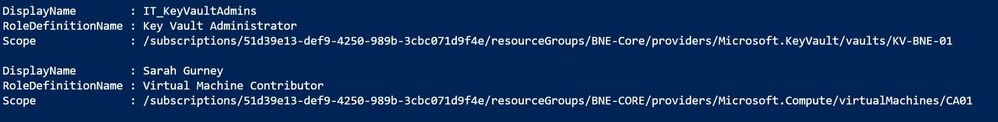
Now I can see that as well as being listed as an individual with the Virtual Machine Contributor role to VM CA01, Sarah is also a member of the IT_KeyVaultAdmins group, who have Key Vault Administrator access to the KV-BNE-01 key vault.
Azure deny assignments
There's one type of Azure role assignment that won't display with Get-AzRoleAssignment, and that's an Azure deny assignment. You can't manually assign someone a deny assignment - they are created and used by Azure to protect system-managed resources. Azure Blueprints and Azure managed apps are the only way that they can be created.
You can query where they are being used in your subscription, by using the Get-AzDenyAssignment command.
Learn more
Now you've learnt about the capabilities and structure of this command, go and explore with different command parameters. If you get stuck, visit List Azure role assignments using PowerShell or Remove Azure role assignments for more inspiration.
Get-AzRoleAssignment has the full command syntax, parameters, inputs and outputs.
And many of the basic PowerShell concepts we've explored here, like Get/Set/Remove and output formatting, are applicable to a ton of other PowerShell commands too. You're now on your way to understanding and exploring more of PowerShell, especially for scenarios where you can't easily retrieve the same information in the Azure portal.
Posted at https://sl.advdat.com/3zZphA3
