Overview & Use Case
Thanks to @WarrenZA , @Jason_Baxter & @paulrob for the brainstorming, technical contributing, and proof reading!
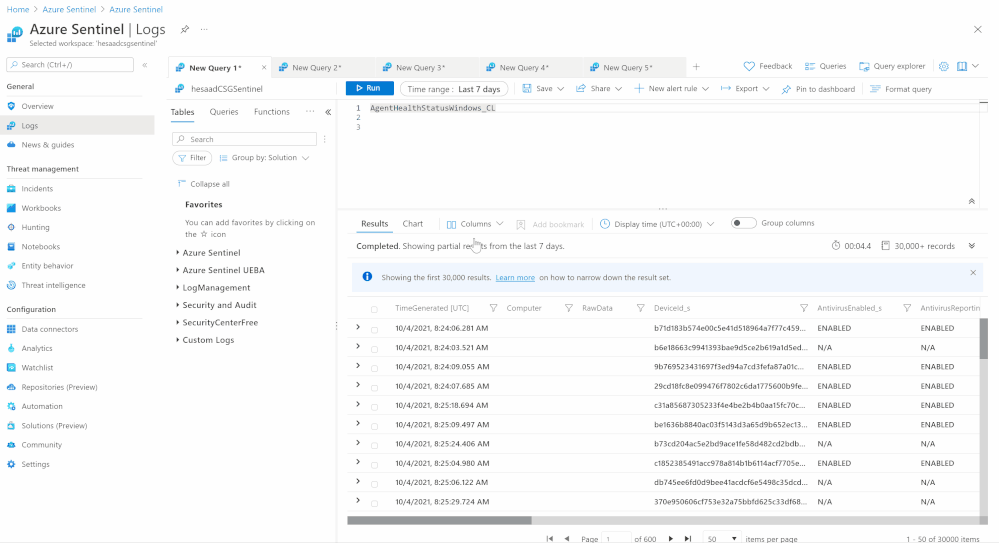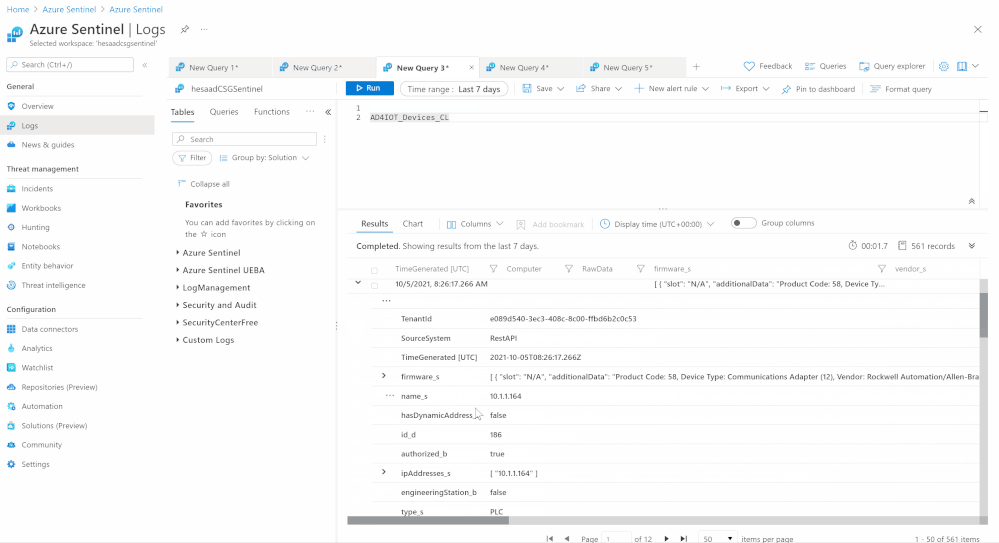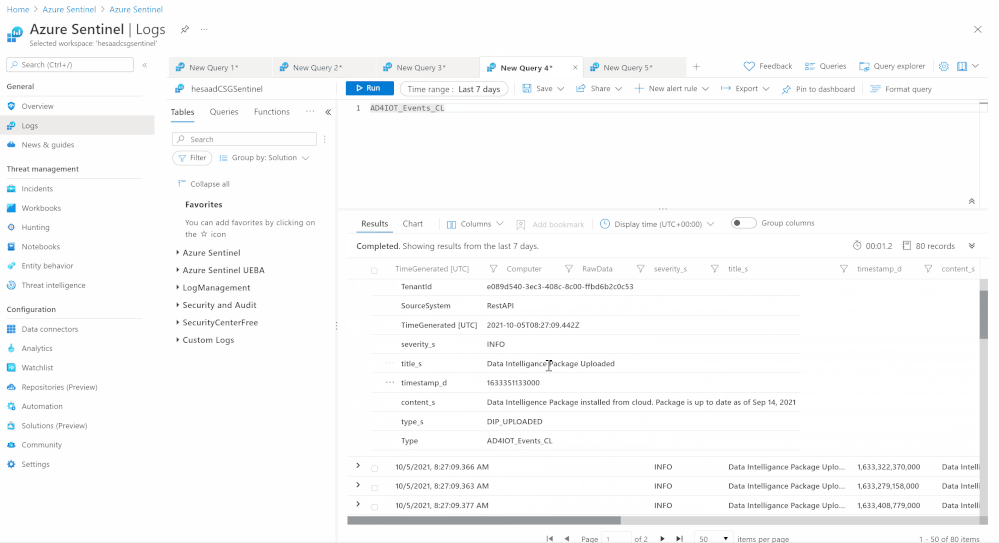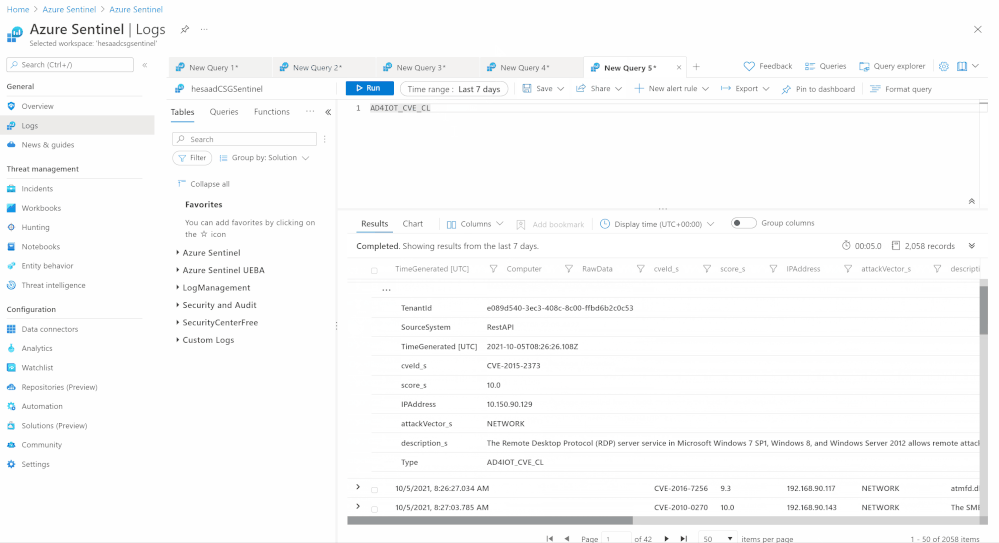
The field of Endpoint forensics seeks to help investigators reconstruct what happened during an endpoint intrusion. Did an attacker break in because of a missing definition / signature / policy / setting or a configuration, and if so, how? What havoc did the attacker wreak after breaking in? Tools that help investigators answer these types of questions are still quite primitive and are often hindered by incomplete or incorrect information. Analyzing Endpoints Forensics - Azure Sentinel Connector can enable more-powerful forensic analysis through techniques such as streaming a computer’s EPP (Endpoint Protection) health status, policies, settings, and configuration in addition to IoT vulnerable assets, data events & vulnerabilities.
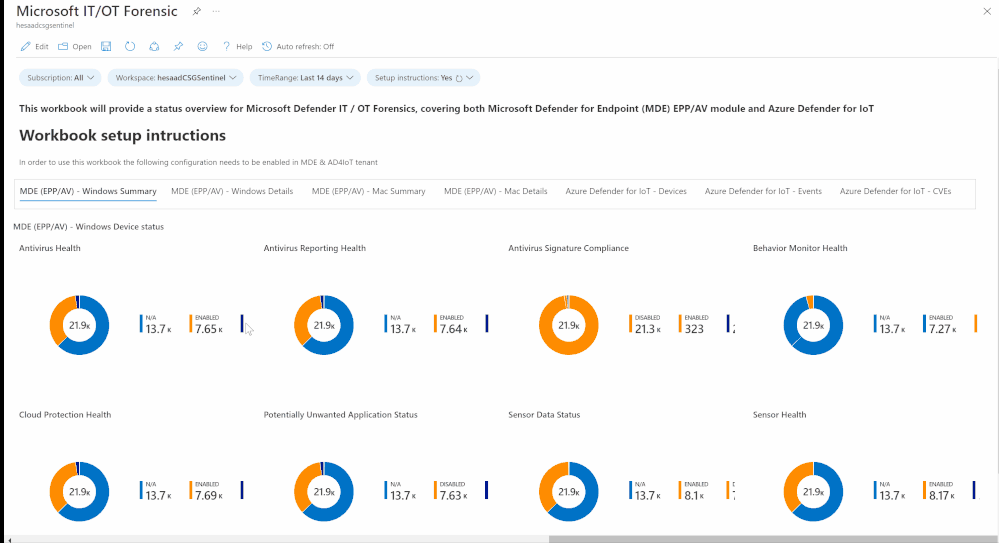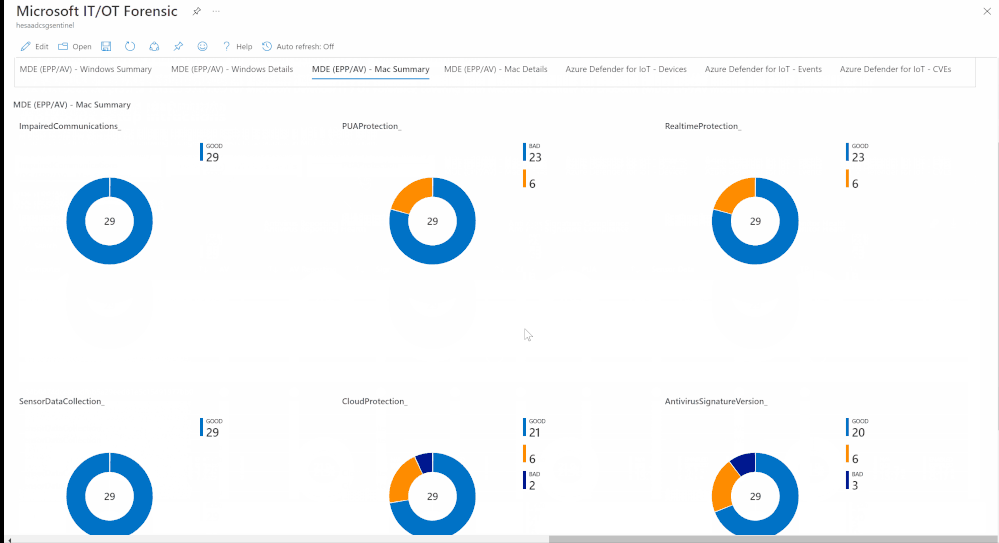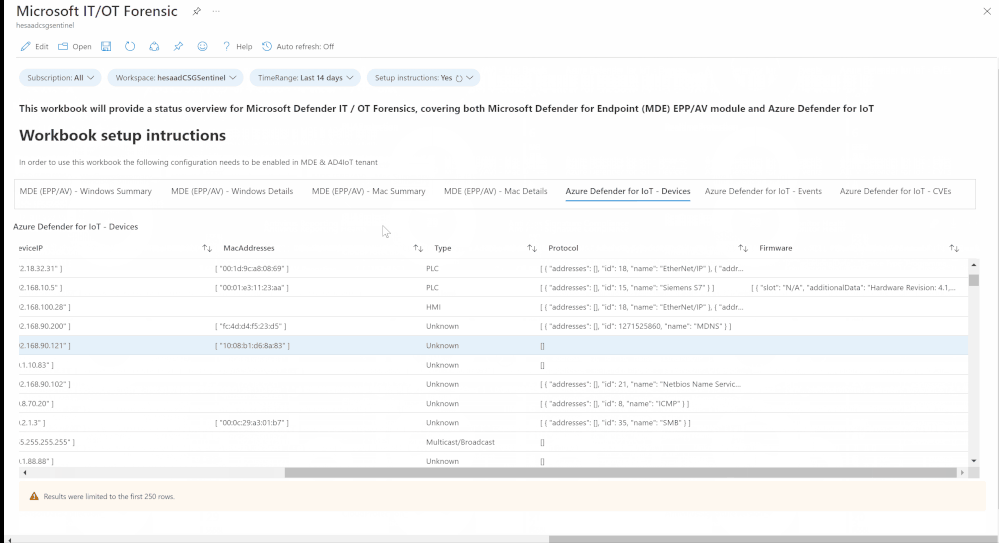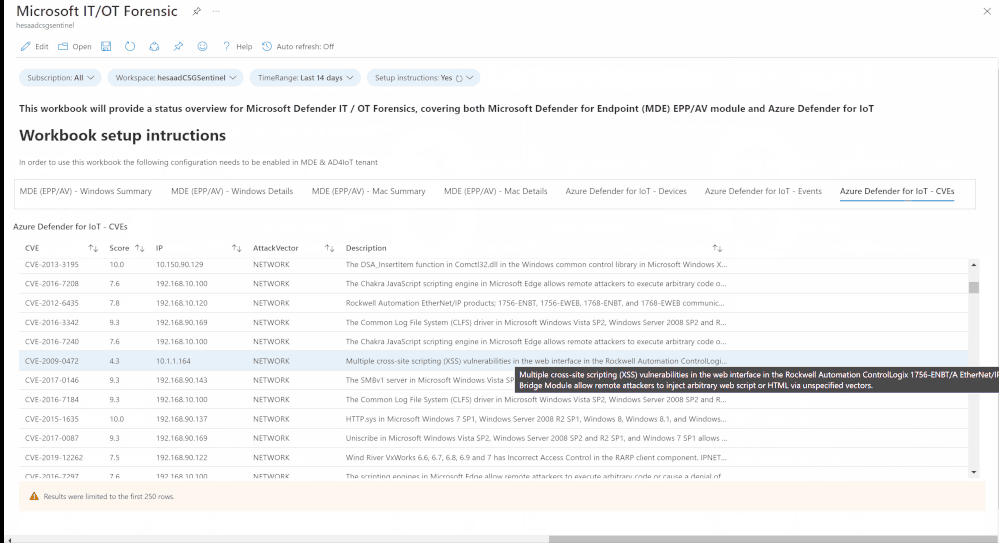
Devices (IT/OT) health state and security configurations policies and settings (Microsoft Defender for Endpoint & Azure Defender for IoT) are critical to SOC team helping them to address the following use cases:
- Identifying onboarded devices and their health status
- Activity and a security posture for IT/OT assets
- Viewing the compliance status of the devices based on the security recommendations
- Identifying devices vulnerabilities and hence provide a triage – matrix remediation framework
Implementation
Step(1): Prep, App Registration & Azure Defender for IoT Key
- Log in to Azure tenant, http://portal.azure.com
- Search for App Registration > New Registration
- Type Name, ensure of selecting the right "supported account type” then click Register button
- Define and consent the below API permissions as shown below:
- Get the following values:
- Application / Client ID
- Tenant ID
- Secret
- Azure Active Directory Domain
- Log in to the Azure Defender for IoT central manager console, System Settings > Access Tokens
- Select Generate new token, describe the purpose of the new token, and select
- Copy the token, save it, and select finish
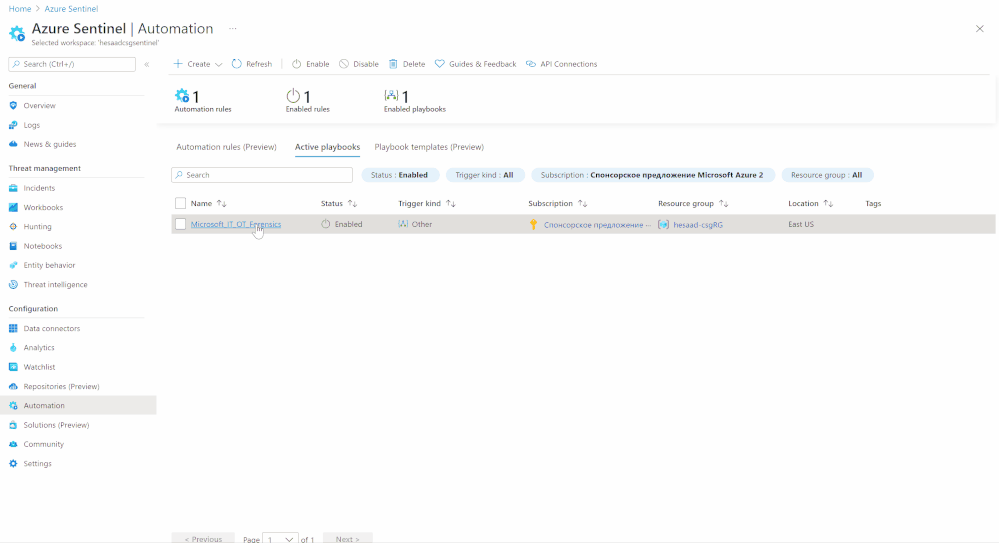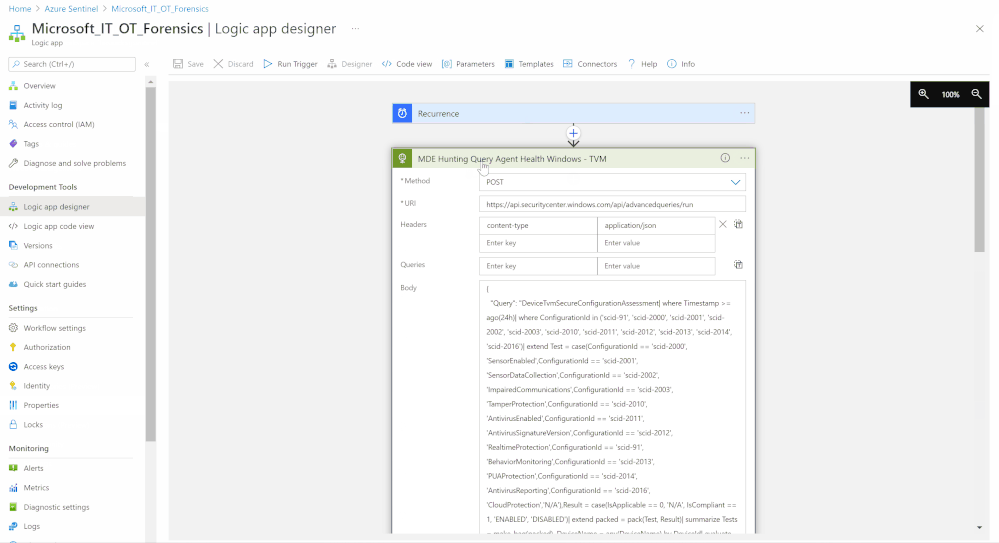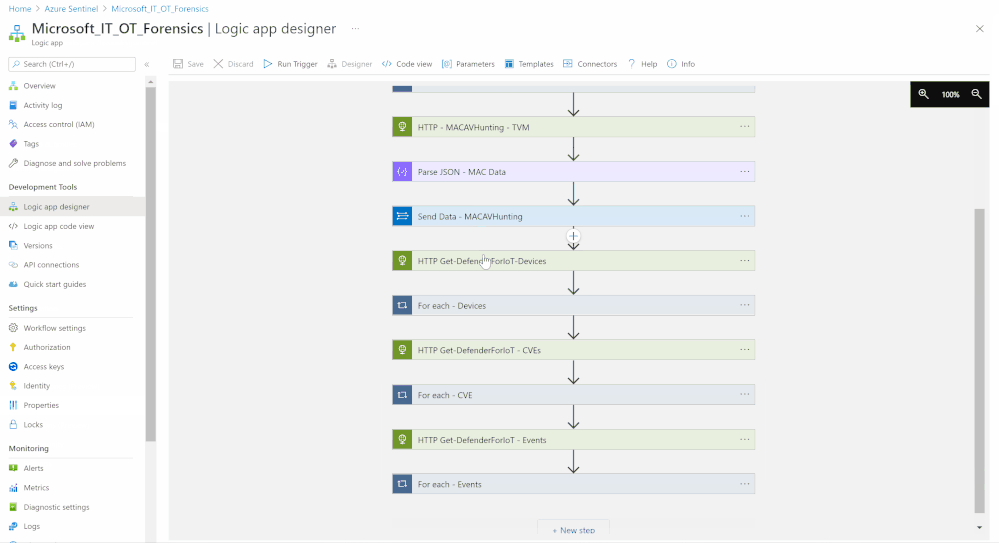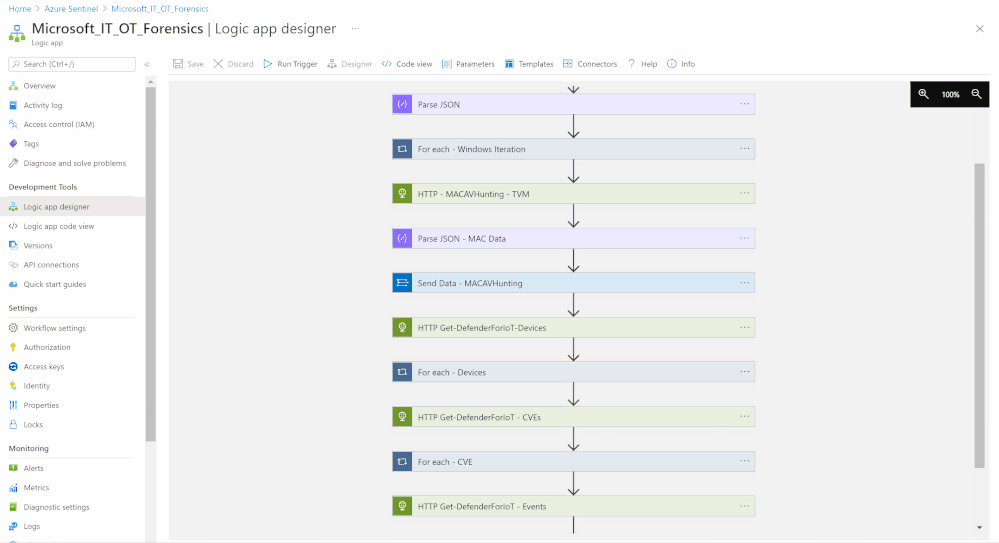
Step(2): Microsoft Devices Forensics Custom Connector
- Log in to Azure tenant, http://portal.azure.com
- Go to Azure Sentinel > Automation
- Create a new blank Playbook and follow the below Gif, the code being uploaded to github repo as well:
- Initialize set of parameters:
- Name: AD4IoTKey
- Type: String
- Default Value: <Azure Defender for IoT Key value been generated at the prep step>
- Name: Application ID
- Type: String
- Default Value: <App registration ID value been generated at the prep step>
- Name: Secret
- Type: String
- Default Value: <App registration Secret value been generated at the prep step>, it’s recommended to use Key vault
- Name: Tenant ID
- Type: String
- Default Value: <App registration Tenant ID value>
- Set a recurrence step to trigger and execute the playbook
- Set an HTTP endpoints to query and fetch Microsoft Defender for Endpoint Windows required logs “MDE Hunting Query Agent Health Windows - TVM”, ensure the authorization type is Active Directory OAuth
- Parse content-types data via Json
- Iterate (For-each) on all returned values (Body) as Microsoft Defender for Endpoint Windows iterations data then send the data to Azure Sentinel Log analytics workspace via a custom log table (AgentHealthStatusWindows)
- Repeat the above steps to cover MacOS and store the data at (MDE_MAC_devicehealth) custom log tables, you can easily do the same and cover Linux and other supported OSs platforms.
- Also repeat the above steps to cover Azure Defender for IoT:
- Devices
- Events
- CVEs
Step(3): Microsoft Devices Forensics Workbook & Hunting
- Log in to Azure tenant, http://portal.azure.com
- Go to Azure Sentinel > Automation
- Create new workbook (Add workbook)
- Click on Edit > Advanced Editor (icon)
- Copy and paste the workbook json code uploaded to github repo, click done editing and save
Notes & Consideration
- You can customize the parsers at the connector's flow with the required and needed attributed / fields based on your schema / payload before the ingestion process, also you can create custom Azure Functions once the data being ingested to Azure Sentinel
- Azure Function can be used to create the custom connector as well
- Couple of points to be considered while using Logic Apps:
- Cost (standard / enterprise connectors)
- Considerations & Configurations
- Nonstandard schema
- Rewriting rules
Get started today!
We encourage you to try it now!
You can also contribute new connectors, workbooks, analytics and more in Azure Sentinel. Get started now by joining the Azure Sentinel Threat Hunters GitHub community.
Posted at https://sl.advdat.com/3aqLX0Z