As part of our ongoing effort to deliver industry leading EDR capabilities across platforms, we are pleased to announce that new live response capabilities for macOS and Linux are now available now for public preview customers.
With live response, you have the power to do in-depth investigative work and take immediate response actions to promptly contain identified threats -- in real-time.
Live response is designed to enhance investigations by enabling your security operations team to collect forensic data, run scripts, send suspicious entities for analysis, remediate threats, and proactively hunt for emerging threats.
With live response for macOS and Linux, analysts can do the following tasks:
- Run basic and advanced commands to investigate suspicious entities.
- Collect files (such as malware samples, scripts output) for offline analysis.
- New: Trigger response actions on the device.
- Upload any Bash script to their live response library, and then run it on the device to collect forensics evidence and remediate malicious entities.
Trigger response actions on a device
Along with the new capabilities for macOS and Linux we are pleased to introduce new commands that are unique for these platforms which allow you to trigger response actions from the live response interface while investigating a device.
Enforce network isolation – Depending on the severity of the attack and the sensitivity of the device, you might want to isolate the device from the network. This action can help prevent the attacker from controlling the compromised device and performing further activities such as data exfiltration and lateral movement. This feature disconnects the compromised device from the network while retaining connectivity to the Defender for Endpoint service, which continues to monitor the device.
Collect an investigation package – As part of the investigation or response process, you can collect an investigation package from a device. By collecting the investigation package, you can identify the current state of the device and further understand the tools and techniques used by the attacker.
Run an antivirus scan - As part of the investigation or response process, you can remotely initiate an antivirus scan to help identify and remediate malware that might be present on a compromised device. The Action center will show the scan information and the device timeline will include a new event, reflecting that a scan action was submitted on the device. Microsoft Defender Antivirus alerts will reflect any detections that surfaced during the scan.
Check out the following guide to get started with live response on macOS and Linux:
- Initiate a session and perform basic remediation actions
- Use Bash scripts to collect and analyze forensics data
- Trigger response actions through the live response interface
Before you begin
Before you can initiate a session on a machine, make sure you fulfil the following requirements:
- You’ll need to have preview features turned on in the Microsoft Defender Security Center or in the Microsoft 365 security center.
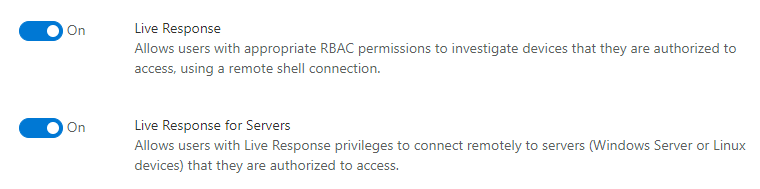
- Enable live response from the settings page - You'll need to enable the live response capability in the Advanced features settings page.
Note: Only users with manage security or global admin roles can edit these settings.
- Ensure that you have the appropriate permissions
Only users who have been provisioned with the appropriate permissions can initiate a session. For more information on role assignments see Create roles. - Verify that you're running a supported OS - devices must be running one of the following versions:
- macOS - minimum required version: 101.43.84
- macOS 10.14 (Mojave)
- macOS 10.15 (Catalina)
- macOS 11 (Big Sur)
- Linux - minimum required version: 101.45.13
- Red Hat Enterprise Linux 7.2 or higher
- CentOS 7.2 or higher
- Ubuntu 16.04 LTS or higher LTS
- Debian 9 or higher
- SUSE Linux Enterprise Server 12 or higher
- Oracle Linux 7.2 or higher
- macOS - minimum required version: 101.43.84
Depending on the role that's been granted to you, you can run basic or advanced live response commands. Users permission are controlled by RBAC custom role.
Initiate a live response session and perform basic remediation
- Log in to the Microsoft Defender Security Center and navigate to Device inventory page
- Select a compromised device to open the device page and launch the live response session by clicking Initiate Live response session.
- Wait while the session connects to the device.
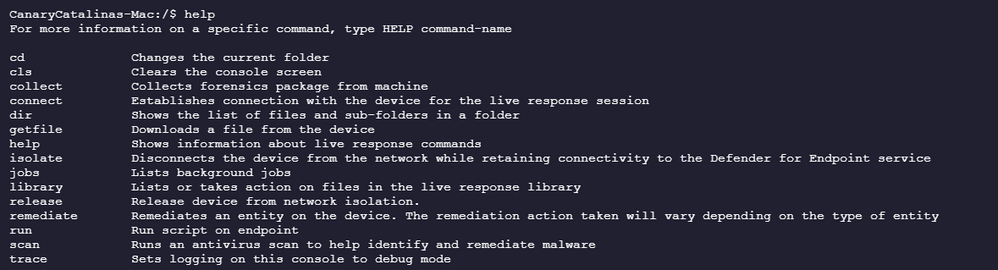
- When the device is connected, type help in the command console. It will show you all the available commands.
- Create/download a script that collects any artifact that may interest you. For basic usage, you can use the sample scripts below.
#!/bin/bash
function test_connection()
{
ping bing.com -c5
}
test_connection
exit 0
#!/bin/bash
function connections()
{
case $(uname | tr '[:upper:]' '[:lower:]') in
linux*)
ss -a
;;
darwin*)
netstat -an
;;
*)
echo "unsupported"
;;
esac
}
connections
exit 0
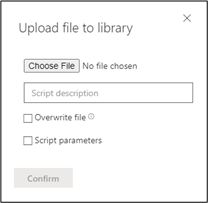
- Before you can run a script, you must first upload it to the library. From the Live Response dashboard, upload scripts to the library by clicking Upload file to library
- Type library in the command console to see the list of available scripts.
- Run the “processes” command to see all running processes in the device.
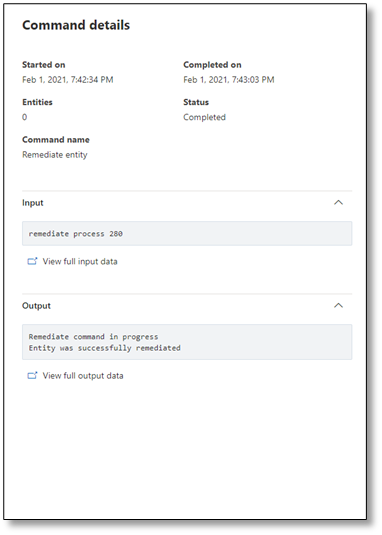
- Run the remediate command on a process in order to end it.
- Run the “connections.sh” script to see all active internet connections.
Note – Currently, the following steps are only applicable to macOS devices.
Important – When isolating a device, only certain processes and destinations are allowed. Therefore, devices that are behind a full
VPN tunnel won't be able to reach the Microsoft Defender for Endpoint cloud service after the device is isolated.
We recommend using a split-tunneling VPN for Microsoft Defender for Endpoint and Microsoft Defender Antivirus cloud-based
protection-related traffic.
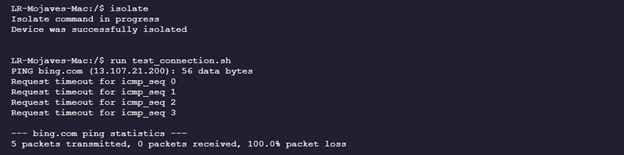
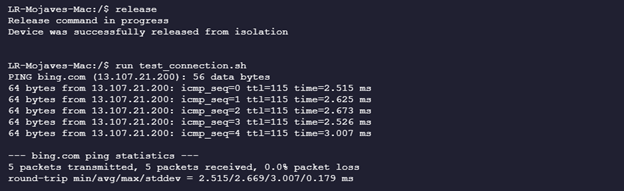
- Run the “test_connection” script to make sure the device can access the internet by typing run test_connection.sh.
- Now run the isolate command to disconnect the device from the network by typing the following command: isolate. You can verify that the device has been successfully isolated by running the “test_connection” script.
- Run the “release from isolation” command by typing: release. You can verify that the device has been successfully released from isolation by running the “test_connection” script for the last time.
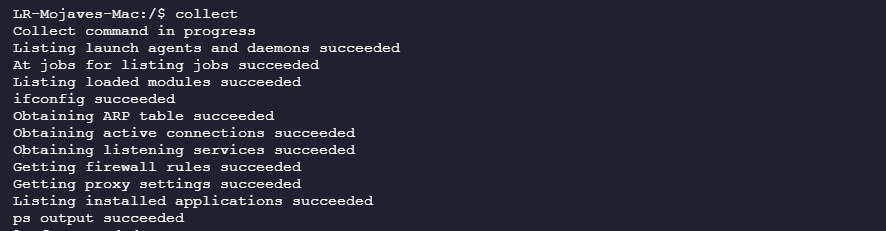
- Run the “collect investigation package” command by typing collect.
- Use the “getfile” command to fetch the investigation package from the location it was saved by typing getfile ‘[\folder\file_name]’.
- Confirm that all actions are logged in the Command log.
Congrats – you’ve initiated a live response session and performed basic remediation!
Conclusion
We’ve demonstrated how you can initiate a live response session and perform basic remediation, query device assets using a Bash script, and take response actions to contain identified threats.
This tutorial emphasizes the typical scenarios and commands that would be useful when an in-depth investigation and remediation is needed on a compromised device.
We hope you enjoyed this tutorial and are now encouraged to explore live response as well as other features and capabilities. For more information, read the product guide at docs.microsoft.com.
We welcome your feedback and look forward to hearing from you! You can submit feedback through the Microsoft Defender Security Center or through the Microsoft 365 security center. Let us know how you feel about this tutorial or any other aspects of the product. We would love to hear your ideas about additional simulations and tutorials. Thank you!
Keep an eye on our blog and Twitter channel to stay up to date on additional Microsoft Defender for Endpoint advancements.
Microsoft Defender for Endpoint is an industry leading, cloud ML powered endpoint security solution offering endpoint protection, endpoint detection and response, vulnerability management, and mobile threat defense. With our solution, threats are no match. If you are not yet taking advantage of Microsoft’s unrivaled threat optics and proven capabilities, sign up for a free Microsoft Defender for Endpoint trial today.
Posted at https://sl.advdat.com/3vH9NQ0