Discovering Microsoft 365 Logs within your Organization
Part 1 Unified Access Log (UAL)
I was recently asked to deliver a session around hunting Microsoft 365 logs to help an organization determine the various methods and limits to each. This seemed like an easy ask and I was sure someone already put together content. To my surprise, I couldn’t find a colleague that had a consolidated set of information.
Microsoft is good at updating doc pages and providing information, unfortunately, the answers can be spread across several different sites in various locations. Which bring me to this multi part series on how to hunt Microsoft 365 data. My goal is to help security teams better understand each method and the limits.
Microsoft 365 is a highly targeted resource that is rich with organizational data stored in Office 365, SharePoint, Teams, and other Microsoft 365 components. Over the years, security teams have gained a deeper understanding of Microsoft 365 and Microsoft has continued to add additional auditing to the platform.
For this blog series we will focus on 6 key areas:
- Unified Audit Logs (UAL)
- Mailbox Audit Logs
- Message Trace
- Azure Active Directory
- M365 Defender Streaming API
- Defender 365 Advanced Hunting
Auditing is now enabled by default in Microsoft 365,365; however, each organization should verify their auditing is enabled by running the following command:
Get-AdminAuditLogConfig | FL UnifiedAuditLogIngestionEnabled.
While Azure Active Directory data is represented in the Unified Audit Log data, additional details can be found the Azure Active Directory Sign-in and Audit Logs. Details on collecting data from Azure Active Directory will be provided in a follow-on blog.
Microsoft 365 provides two levels of auditing everyone should be familiar with and the licensing requirements for each.
- Logs stored for 90 days
- Auditing for thousands of events
- Enabled by default
- Requires one of the following licenses below:
|
License |
|
|
Office 365 |
E3/A3/G3 |
|
Microsoft 365 |
E3/A3/G3 |
- Additional log types:
- Mailitems Access
- Send
- SearchQueryIntiatedExchange
- SearchQueryInitiatedSharepoint
- Logs stored for 1 year
- Creation of log polices up to 10 years (additional cost)
- Requires any of the additional licenses outlined below:
|
License |
|
|
Office 365 |
E5/A5/G5 |
|
Microsoft 365 |
E5/A5/G5 |
|
Office 365 |
Advanced Compliance (add on) |
|
Office 365 |
Advanced Aduit/Ediscovery (add on) |
See official list here: Advanced Audit Licensing
Who can access the logs?
Microsoft 365 provides several built-in roles and allows for the creation of custom role types. As a best practice, organizations should always follow the principle of least privilege when assigning permissions.
To access the UAL, team members will need to be delegated one of the following roles; View-Only Audit Logs or Audit Logs role in Exchange online. By default, members of the Compliance Management and Organizational Management roles will have access to the logs. If you assign a user the View-Only Audit Logs or Audit Logs role on the Permissions page in the Microsoft 365 compliance center, they won't be able to search the audit log. You have to assign the permissions in Exchange Online. This is because the underlying cmdlet used to search the audit log is an Exchange Online cmdlet.
At this point, there should be a basic understanding of the two levels (basic and Advanced) of logging and the roles that are required to access the logs.
Security teams should know the time lag that can occur with the UAL and take this into consideration when working through an incident or daily troubleshooting. It can take up to 30 minutes or up to 24 hours after and event occurs for the information to be returned in a search of the UAL.
The following table provides guidelines for various events and the potential lag time for the event to show up in the UAL. Some logs can be consumed from other locations like the Azure Active Directory sign on logs at earlier intervals:
|
Microsoft 365 service or feature |
30 minutes |
24 hours |
|
Defender for Microsoft 365 and Threat Intelligence |

|
|
|
Azure Active Directory (user login events) |
|

|
|
Azure Active Directory (admin events) |
|

|
|
Data Loss Prevention |

|
|
|
Dynamics 365 CRM |
|

|
|
eDiscovery |

|
|
|
Exchange Online |

|
|
|
Microsoft Power Automate |
|

|
|
Microsoft Stream |

|
|
|
Microsoft Teams |

|
|
|
Power Apps |
|

|
|
Power BI |

|
|
|
Microsoft 365 compliance center |

|
|
|
Sensitivity labels |
|

|
|
SharePoint Online and OneDrive for Business |

|
|
|
Workplace Analytics |

|
|
|
Yammer |
|

|
|
Microsoft Forms |

|
|
How can data be accessed?
There are three methods that can be used to access the UAL data, and each comes with a set of limitations.
- Graphical
- PowerShell
- Office Management API
Graphical:
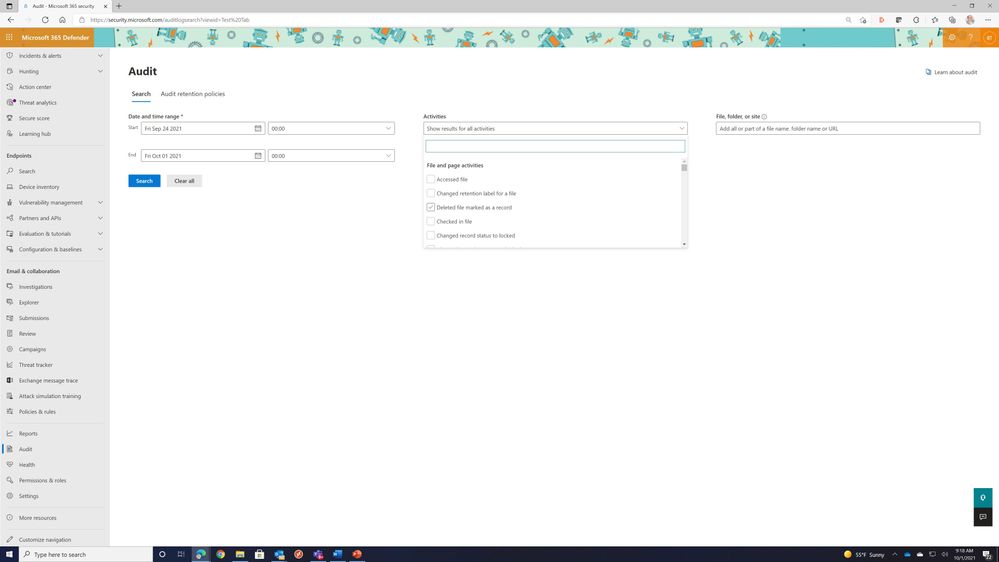
The simplest way to access the UAL is to logon to the portal and perform a search. Historically, this was done by going to the Security and Compliance portal however, the UAL is being moved to the unified security portal located at security.microsoft.com (note this is still being rolled out to GCC+ customers). Once signed into the security.microsoft.com portal select Audit in the lower left-hand corner to access the UAL.
Figure 1: Unified Audit Log
In the portal there are three items that can be used to manipulate the search results.
- Data range
- Activities
- Files/Folder
When manipulating the date range note the license requirements and limits that was outlined earlier in the article. Basic will provide 90 days of retention vs Advanced Audit which can be up to 10 years based on policy.
Limits to consider with the graphical search:
- Maximum of 5k events returned in chunks of 150 and the most recent 5k will be returned
- 90-day limit for users without advanced licensing
- Limited performance for large searches
Tips:
- Attempt to focus the search as much as possible
- Scope the activities
- Scope the date and time
- Targe the appropriate files\folders
- Export larger searches via the CSV export for more granular searching
- Best practice to ingest data into a SIEM or big data solution
Office Management API
The Office Management API is a rest API provided to customers using industry standard approaches included OAuth V2, ODATA V4 and JSON. The API is commonly used to export data to a SIEM, central storage location, or by security teams to automate activities. To use the API there are a few steps that need to be completed before we can access the data.
Setup steps are outlined here
- Register accessing application into Azure Active Directory
- Tenant Consent
- Request Access tokens from Azure Active Directory
- Make data calls to API
API urls
- Commercial: https://manage.office.com/api/v1.0/{tenant_id}/activity/feed/{operation}
- GCC government: https://manage-gcc.office.com/api/v1.0/{tenant_id}/activity/feed/{operation}
- GCC High government: https://manage.office365.us/api/v1.0/{tenant_id}/activity/feed/{operation}
- DoD government: https://manage.protection.apps.mil/api/v1.0/{tenant_id}/activity/feed/{operation}
After completing the step above your application can now connect to the management API to retrieve data from Microsoft 365.
The API comes with its own limitation and should be used only when appropriate. It does solve some issues we saw in the graphical approach around performance but it not always the correct method.
Limits:
- Limited to last 7 days of history
- API provides event details for a log you must download the data to implement additional queries
- Limited to 2,000 requests per minute however G/E5 customer will get twice as much bandwidth allocated
Additional information can be found in the FAQ here
Tips:
- For busy tenants, page content using a logical loop and check the NextPageUrl header value
- Push data into a tool like Azure Sentinel or other data lakes for better search ability
Powershell
The Search-UnifiedAuditLog provides a command line interface into the UAL. This method provides staff and security teams with a richer set of capabilities beyond the graphic interface. However, if your organization wants to download the logs; using the Management API is the preferred method assuming the data you are looking for is in the last 7 days.
To use the Exchange Online powershell module several steps need to be complete before a search can run.
*Note: if you have not installed the Exchange Online Module you will need to run Install-Module ExchangeOnlineManagment first.
Step 1: connect to Exchange Online Powershell by using the Import-Module ExchangeOnlineManagement command
*If you get an error you may need to set the exaction policy with the Set-ExecutionPolicy RemoteSigned command
Step 2: Run Connect-ExchangeOnline command
*Refer to the documentation for the various switches
Step 3: run Search-UnifiedAuditLog with the appropriate switches
Example Search-UnifiedAuditLog -StartDate 09/1/2021 -EndDate 09/26/2021
The Search-UnifiedAuditLog has the following parameters
-EndDate <ExDateTime>
-StartDate <ExDateTime>
[-Formatted]
[-FreeText <String>]
[-IPAddresses <String[]>]
[-ObjectIds <String[]>]
[-Operations <String[]>]
[-RecordType <AuditRecordType>]
[-ResultSize <Int32>]
[-SessionCommand <UnifiedAuditSessionCommand>]
[-SessionId <String>]
[-SiteIds <String[]>]
[-UserIds <String[]>]
[<CommonParameters>]
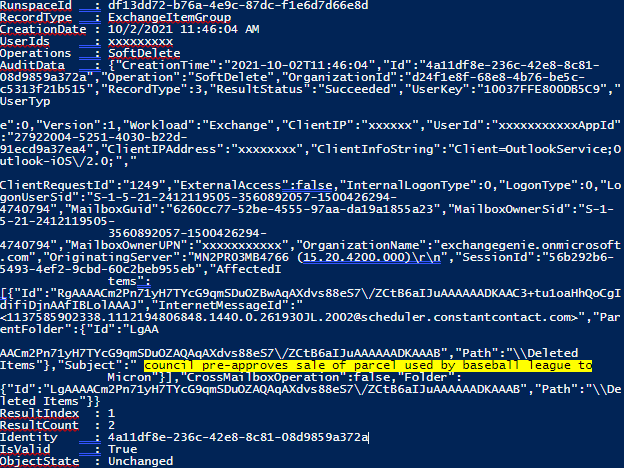
To search for text in the logs run the following command : Search-UnifiedAuditLog -StartDate 10/1/2021 -EndDate 10/04/2021 -FreeText "baseball"
Limits:
- The ResultSize parameter specifies the maximum number of results to return. The default value is 100, maximum is 5,000.
Tips:
- The Search-UnifiedAuditLog provides some additional ability like text search over the graphic and API methods
- Pull logs to a SIEM is preferred to provide robust searching
- Always use the same SessionCommand value for a given SessionId value. Don't switch between ReturnLargeSet and ReturnNextPreviewPage for the same session ID. Otherwise, the output is limited to 10,000 results
- To pull data sets larger than the 5,000 results, using a time-slicing approach is recommended. The results from the Search-UnifiedAuditLog cmdlet will include a column for the ResultCount indicating the total number of records that were found matching the criteria. If that number is larger than the ResultSize specified, shortening the time window and repeating the search is recommended.
Azure Sentinel
Per NIST and industry recommendation, organization should have a Security Incident Event Management (SIEM) system in place to aggregate information for better searchability and retention. Azure Sentinel provides an out of the box experience to connect the Microsoft 365 UAL and pull data into a rich searchable environment. This single click experience can help staff rapidly connect to the data.
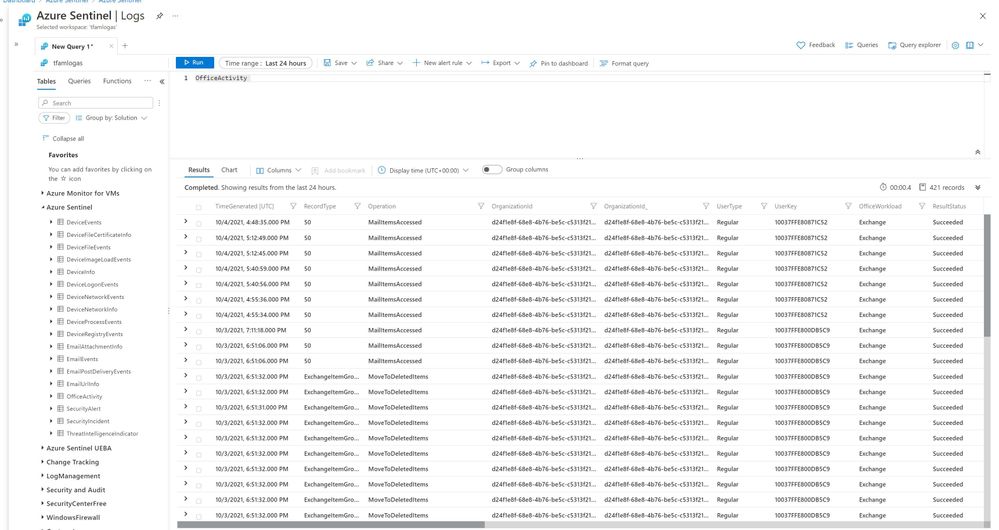
Azure Sentinel stores the Office log data in the OfficeActivity table helping organization use the powerful KQL query language to perform advanced searches and join multiple tables together to expand the investigation beyond the Microsoft 365 platform.
Azure Sentinel can store logs for up to 2 years and can work in conjunction with Azure Data Explorer or Azure storage for longer retention or archival purposes.
As the number of log locations increases and the number of API endpoints expand using Azure Sentinel to aggregate various logs can simple an organization access to those logs. Even if an organization may use other SIEM solutions pull data into Azure Sentinel and then pushing to the other SIEM can reduce the complexity of connecting to multiple APIs.
Links:
- Search-UnifiedAuditLog
- Office 365 Management API
- Unified Audit Logs
- Exchange Online Powershell
- Azure Sentinel Data connectors
- Enable Auditing in Microsoft 365
- Advanced Audit Licensing
Posted at https://sl.advdat.com/3lkNcoX