It’s a usual requirement to make our Service Fabric cluster safer to match business requirement. For example, by disabling TLS 1.0 and 1.1.
Since the TLS setting is not so related to Service Fabric cluster, but more related to the underlying VMSS, this blog will focus more on how we can easily modify the configuration of the underlying VMSS and what we need to pay attention to make sure everything is running smoothly.
The aim of this blog is to change the value of the registry table which is related to TLS 1.0, 1.1 and 1.2 setting. If you prefer, you can also RDP into every node to modify these values manually. But please check the Important points to explain before starting part at first for some very important notification.
The registry tables which need to be modified are:
- HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server with Enabled as 0 and
DisabledByDefault as 1
- HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client with Enabled as 0 and
DisabledByDefault as 1
- HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server with Enabled as 0 and
DisabledByDefault as 1
- HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client with Enabled as 0 and
DisabledByDefault as 1
-
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server with Enabled as 0xffffffff and DisabledByDefault as 0
- HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client with Enabled as 0xffffffff and DisabledByDefault as 0
Pre-requirements:
Before starting, you must setup the environment at first.
To set up a local development environment, you need to have:
- A running Service Fabric cluster with HTTPS enabled. If you don’t have one, please follow this tutorial.
Important points to explain before starting:
This process will cause some downtime of the whole cluster because we need to modify the registry table value on all the VMSS instances, and a restart operation is required. How long that the downtime will be, depends on multiple factors, such as the VM size of our VMSS, how many services we run on the same node etc. Please expect this downtime before using this way on a production environment. For the way without downtime but more complicated(manually), I’ll mention it at the end of this article.
Since this process is a little bit complicated and there are some points which may cause problem, if you have any difficulty or the process got blocked or unexpected, please kindly reach support team for help.
Before implementation:
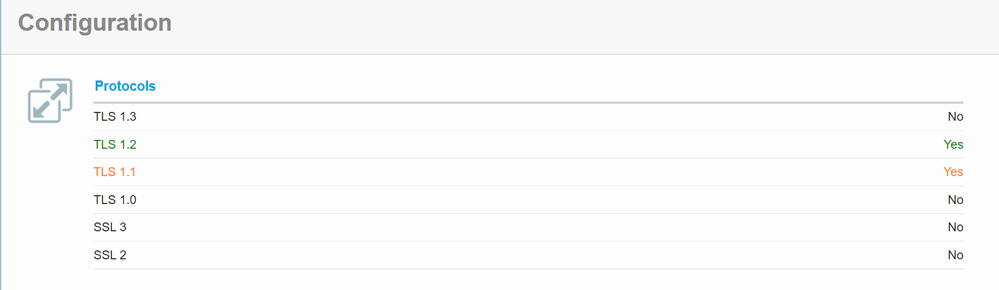
Once you are done with the preparation, you can use online tool https://www.ssllabs.com/ssltest to scan the status of TLS 1.0, 1.1 and 1.2. Please feel free to use other tools which you prefer.
Original status: TLS 1.0 disabled and TLS 1.1, 1.2 enabled.
Steps to implement:
- Download the script and save it with a name such as EnableTLS12.ps1. This script is to disable/enable the necessary registry table value for TLS setting.
- Upload script into storage. In this step, we need to create a new or use existing storage account, create a new container, set the container access level, upload the script file into storage and save the URL.
- Create a new storage account if you don’t have one. Please follow this tutorial.
- Create a new container.
Create container in Storage account
- Enter the created container and change the access level to Container.
Container access level configuration
- Upload the script file into the new container.
Upload script into container
- Check the property of the uploaded script and save the URL somewhere. We’ll use it later. In my example, it’s https://storagecsjerry.blob.core.windows.net/powershellscript/EnableTLS12.ps1
The property menu of blob
Storage URL of the script
- Please visit the URL in previous step in your web browser and make sure the script file can be downloaded directly without any other action.
- We need to add a new extension into the underlying VMSS. We can use multiple ways to do this such as deploying ARM template, using CLI command etc. But the resource explorer is the clearest way to see how we modify the configuration.
- Visit Resource Explorer https://resources.azure.com/ and login.
- On the left side, look for the correct subscription, resource group, resource type, then resource name of our underlying VMSS of Service Fabric cluster.
VMSS path in resource explorer
- Switch to Edit mode
Edit mode of resource explorer
- According to our official document, we can use the same way to add a new VMSS extension to run our PowerShell script. Scroll down the JSON format file and at almost the end, we’ll be able to find the setting of the extension. (Your last extension may not be called MicrosoftMonitoringAgent but it doesn’t matter)
Original VMSS extensions
- Add one more new extension like following: (Do not forget the comma at the end of original last extension to make sure it’s a valid JSON file, in the example, the comma is at line 208)
VMSS JSON file after adding new extension
- The text version of the new extension configuration: (Remember to replace the storage URL by the one from step 2 and the script name at line 10 and 12.)
{ "name": "EnableTLS12", "properties": { "autoUpgradeMinorVersion": true, "publisher": "Microsoft.Compute", "type": "CustomScriptExtension", "typeHandlerVersion": "1.7", "settings": { "fileUris": [ "https://storagecsjerry.blob.core.windows.net/powershellscript/EnableTLS12.ps1" ], "commandToExecute": "powershell.exe -ExecutionPolicy Unrestricted -File EnableTLS12.ps1" } } } - After adding the extension configuration into JSON file, scroll up to the top of page and send the request out by clicking on PUT. Then please keep monitoring the window. If everything is OK, you’ll see a green icon and the mode will be switched back to GET automatically.
PUT request button
PUT request result
- Keep monitoring to see whether the VMSS can be updated successfully. If we check through the JSON result, we will find one item called ProvisioningState (normally at the end of the JSON file). Once we click on PUT button, the ProvisioningState will be Updating. Please periodically click on GET and check the ProvisioningState until it becomes Succeeded.
VMSS in updating status
VMSS successfully updated
- Keep monitoring the status of the cluster from Service Fabric Explorer. It can be accessed from the Service Fabric cluster Azure Portal page. The URL will be like https://{clustername}.{region}.cloudapp.azure.com:19080
Service Fabric Explorer in Azure PortalOnce the new VMSS extension is provisioned successfully, we should see all the nodes of this VMSS is down. Please wait until all the nodes come back to green/healthy status.
Service Fabric Explorer with healthy status
After implementation:
If you aren’t blocked by any step, congratulations, you’ve done everything needed. You can use the same tool or whichever tool you want to scan again, and we’ll find that the TLS 1.1 is disabled.

The tips about the way without downtime:
As mentioned in the first part, this way of using VMSS extension will cause some downtime since the installing of the extension is proceeded at same time and the PowerShell will require a restart operation to make the registry table value change take effect.
The way without downtime is with the same idea but doing this manually instead of using VMSS extension.
To summarize the steps simply, it will be:
- Open the Service Fabric Explorer and keep it open
- RDP into one instance of your VMSS
- Run the same PowerShell script manually in RDP window
- Restart the instance as required by the PowerShell script
- Monitor the Service Fabric Explorer and wait until everything is coming back to green/healthy status
- Repeat step 2 to 5 for every instance.
Attention! Please remember that we must wait until the status of node in Service Fabric Explorer is green/healthy, including the System Services in the last part. The status of the node in Azure Portal will only show that the node is healthy but not containing the System Service.
Posted at https://sl.advdat.com/3nLq5E7