The recent Biden Administration Executive Order (EO) 14028 highlights the need for strong cloud security among federal agencies. Azure Security Center (ASC) addresses the three most pressing security challenges customers are experiencing today including rapidly changing workloads, increasingly sophisticated attacks, and security skills that are in short supply.
ASC is a powerful tool for federal agencies regardless of where they may be in their digital transformation journeys. ASC continuously scans your hybrid cloud environment and recommendations to help you harden your attack surface against threats. Azure Security Benchmark (ASB) is the baseline and driver for these recommendations. ASB is a Microsoft-authored, Azure-specific set of guidelines for security and compliance best practices based on common compliance frameworks.
For customers leveraging multiple products within the Azure Security suite, it can be difficult to have a single plan for hardening. Customers spend time manually pivoting across products rather than conducting proactive cloud security posture management or responding to alerts.
This “better together” content offering enriches granular ASC assessments with Azure Sentinel logging for alerts/configuration over time to provide one place for security professionals to understand their cloud security posture over time. With actionable insights and real time information, this workbook empowers teams by equipping them with a single source of visibility and remediation across security products.
Check out a demo: Azure Security Benchmark Workbook | Azure Security Center in the Field #35 - YouTube
What is the Azure Security Benchmark?
The Azure Security Benchmark (ASB) provides prescriptive best practices and recommendations to help improve the security of workloads, data, and services on Azure. Many organizations rely on standard frameworks such as CISv7.1 or NIST 800-53 R4 to improve their cloud defenses. Mapped to both CISv7.1 and NIST 800-53 R4, ASB brings consistency of security capabilities across the Azure platform. Compliance and security baselines are critical for successful cloud migration and adoption by providing consistent security standards. Whether you are new to Azure or not, ASB provides streamlined guidance for improving the security and compliance posture of your Azure resources.
Getting Started
While the Azure Security Benchmark workbook aggregates and builds on telemetry from 25+ Microsoft Security products, only Azure Security Center is mandatory for this offering. Azure Sentinel, Microsoft Defender for Endpoint, Microsoft Defender for Identity, Microsoft Cloud App Security, Microsoft 365 Defender, Microsoft Defender for Office, Azure Firewall, Azure Virtual Networks, Azure Web Application Firewall, Azure ExpressRoute, Azure Lighthouse, Azure Active Directory, and additional offerings enhance this workbook with alignment to ASB.
- Onboard Azure Security Center
- Onboard Azure Sentinel (optional)
- Enable Continuous Export of SecurityRecommendation data
- Consolidate Azure Security Center and Azure Sentinel Logging in a Log Analytics Workspace
- Access the Azure Security Benchmark Workbook on Github, Select Deploy to Azure (or Azure Gov)
- Authenticate to your Azure subscription
- Configure options > Review + Create
- Navigate to Azure Security Center
- Select Workbooks > Workbooks tab > AzureSecurityBenchmark
- Review the workbook and provide feedback through our survey
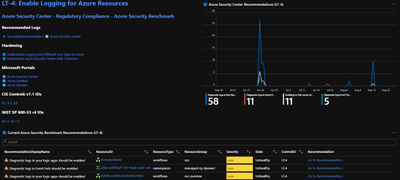
The Azure Security Benchmark Workbook breaks down each control family into sub-controls with their own control card. The control cards centralize telemetry across Microsoft products around the relevant ASB sub-control. Here, security professionals can view actionable insights into recommendation data over time by filtering on resource, resource type, severity, state, and more. For example, teams can use filters to understand the most prevalent recommendation then navigate directly to the ASC portal to address that recommendation and harden their attack surface. Understanding recommendation data over time empowers security teams to understand where they need to build in guardrails and focus on getting secure by default. Direct links to ASB, CIS and NIST documentation provides necessary context for teams looking to drive compliance in Azure. Recommended logs also empower auditors to easily pivot to supplementary information required as part of an audit or to meet a compliance requirement.
Use Cases
Built-in filters, including time, subscription, and workplace filters, facilitate the creation of custom reports. For example, security governance professionals preparing for an audit can create a report with historical compliance data for a set of ASC recommendations that apply to a control, which can easily be printed or exported for sharing. Teams can also export additional artifacts to supplement the report, like relevant logs that are surfaced in the workbook. Best of all, even without expertise in Kusto Query Language, teams can adjust predefined queries to bring in additional evidence data as required!
Key Benefits
- Single pane of glass for aggregating, managing, and actioning data from 25+ Microsoft products to address ASB control requirements
- Deep links for seamless pivots between products
- Over-time analysis for more complete understanding of security and compliance posture
- One-click, customizable reporting
- Leverage pre-written KQL queries to gain insights from log telemetry with the option to customize for further analysis
Learn More About Hardening Workloads with Microsoft Security
- Azure Security Benchmark Introduction
- Meeting the Cybersecurity Executive Order requirements with Azure Security
- Announcing the Azure Sentinel: Zero Trust (TIC3.0) Workbook
- Azure Sentinel Cybersecurity Maturity Model Certification (CMMC) Workbook
Disclaimer
The Azure Security Center: Azure Security Benchmark Workbook demonstrates best practice guidance. This workbook provides visibility and situational awareness for cloud workload protection delivered with Microsoft technologies in predominantly cloud-based environments. Customer experience will vary by user and some panels may require additional configurations for operation. Recommendation cards do not imply coverage of respective controls as they are often one of several courses of action for approaching requirements which is unique to each customer. Recommendations should be considered a starting point for planning full or partial coverage of respective areas.
Posted at https://sl.advdat.com/3vx4ItB