Insider risk solutions are often based on singular User Entity Behavior Activity (UEBA) capabilities which are greatly dependent on complex configurations and endpoint agent deployments. These approaches place the burden on the analyst to tune respective analytics and manage endpoint agent configurations. This approach loses sight of the simple fact that insider risk exists across the entire enterprise environment.
Zero Trust architectures are based on "assume breach" fundamentals which reinforce the requirements for tripwires and multiple levels of trust validations for access to resources. Cloud and hybrid-based computing environments facilitate these approaches because assets must communicate with the cloud by the fabric. The Microsoft Sentinel: Microsoft Insider Risk Management Solution leverages comprehensive signals across the entire computing environment, including identity, endpoints, applications, data, infrastructure, networks, and automation platforms. Extensible technologies such as Azure Arc, Microsoft Defender for Endpoint, and Microsoft Cloud App Security extend coverage into hybrid, on-premises, and multi-cloud environments. Advanced correlations in Artificial Intelligence, Machine Learning, Fusion, UEBA, and geospatial orientation are applied to aggregated signals for granular analysis of risk-based behavior across numerous products.
This solution enables insider risk management teams to investigate risk-based behavior across 25+ Microsoft products. This solution is a better-together story between Microsoft Sentinel and Microsoft 365 Insider Risk Management. The solution includes the Insider Risk Management Workbook, (5) Hunting Queries, (5) Analytics Rules, (1) Playbook automation and the Microsoft 365 Insider Risk Management connector. While only Microsoft Sentinel is required to get started, the solution is enhanced with numerous Microsoft offerings, including, but not limited to:
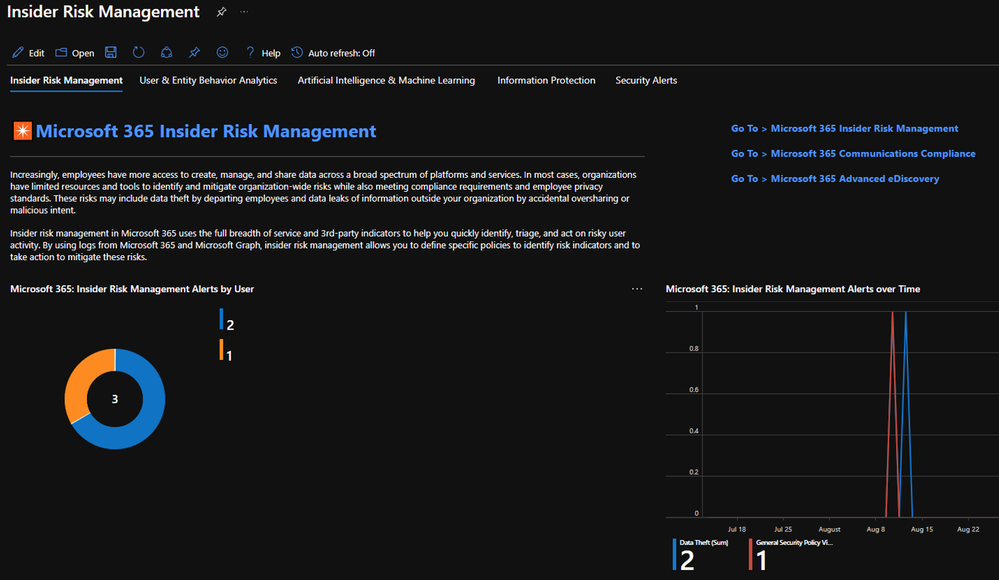
- Microsoft 365 Insider Risk Management
- Microsoft 365 Communications Compliance
- Microsoft 365 Advanced eDiscovery
- Microsoft 365 Defender
- Microsoft Information Protection
- Azure Active Directory
- Microsoft Defender for Cloud
- Microsoft Sentinel Notebooks (Bring Your Own Machine Learning)
- Microsoft Defender for Endpoint
- Microsoft Defender for Identity
- Microsoft Defender for Cloud Apps
- Microsoft Defender for Office 365
Managing and minimizing risk in your organization starts with understanding the types of risks found in the modern workplace. Some risks are driven by external events and factors that are outside of direct control. Other risks are caused by internal events and user activities that can be minimized and avoided. Some examples are risks from illegal, inappropriate, unauthorized, or unethical behavior and actions by users in your organization. These behaviors include a broad range of internal risks from users:
- Leaks of sensitive data and data spillage
- Confidentiality violations
- Intellectual property (IP) theft
- Fraud
- Insider trading
- Regulatory compliance violations
Privacy is a key component of the Microsoft Sentinel Insider Risk Management Solution. This solution is based on both user trust and confidentiality for the protection of respective data. Detection algorithms are tuned to remove false positive alerts while aligning to regulatory and compliance requirements. This solution doesn't incur net-new capabilities as it leverages existing signals within the security architecture. Azure Active Director enforces strict Role-Based Access Control (RBAC) to control confidentiality, integrity, and data availability.
Content Use Cases
Microsoft Sentinel: Insider Risk Management Workbook: A dashboard for simple navigation across dozens of functional areas and 250+ customizable visualizations for advanced analysis and reporting of risk-based behavior. Workbook sections include:
- Getting Started - Build/Design an Insider Risk Management capability
- Insider Risk - Evaluate risk across all entities
- Insider Risk Management
- User & Entity Behavior Analytics
- Artificial Intelligence & Machine Learning
- Information Protection
- Security Alerts
- Watchlists - Analyze risk-based behavior by entity groups (within organization regulatory compliance and privacy directives)
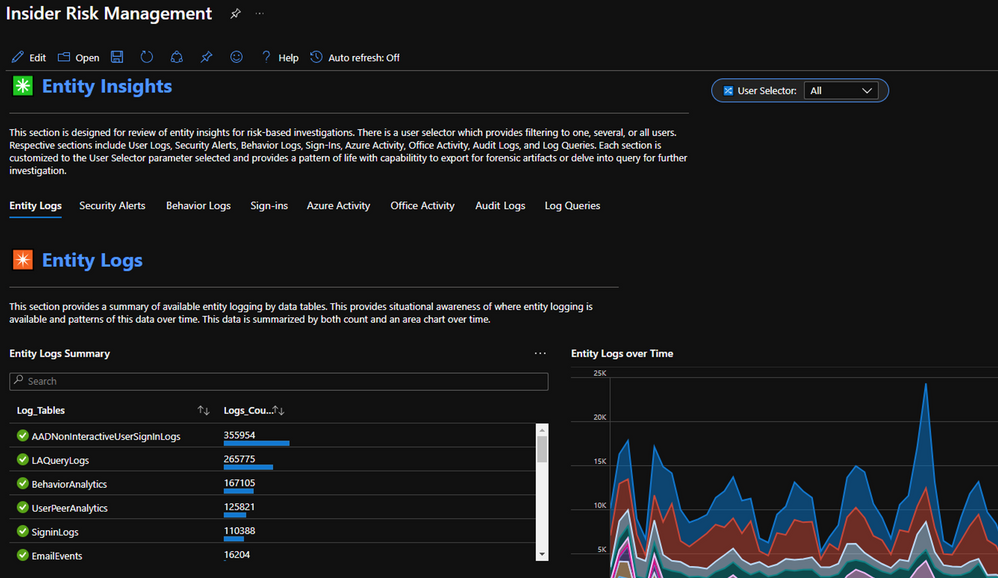
- Entity Insights - Analyze entity risk-based behavior
- Entity Logs
- Security Alerts
- Behavior Logs
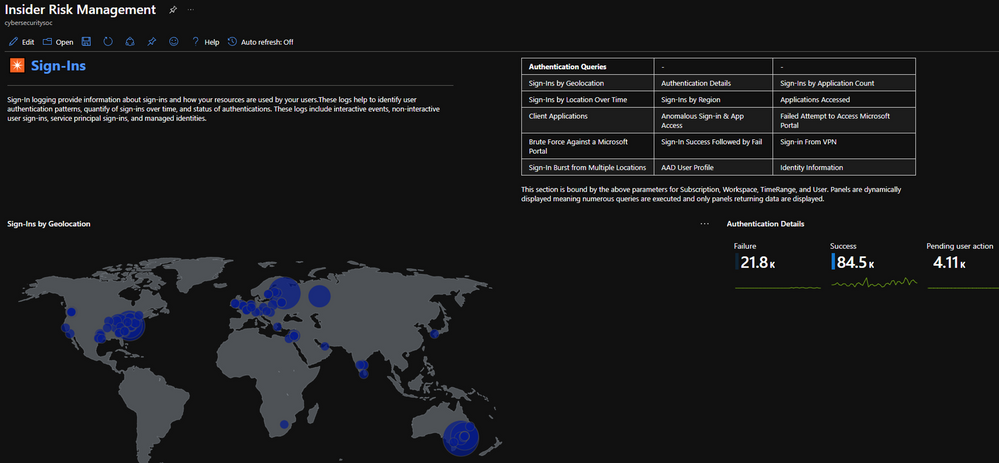
- Sign-Ins
- Azure Activity
- Office Activity
- Audit Logs
- Log Queries
- Open Insider Risk Management Case - Act on risk-based behavior by routing cases to Microsoft 365 Insider Risk Management for response.
Analytics Rules: (5) Microsoft Sentinel rules generate incidents and alert insider teams with aggregation of risk-based behavior across numerous signals.
- High user alerts correlations
- High user incidents correlations
- Microsoft 365 Insider Risk Management alerts observed
- Sensitive data accessed outside organizational geo
- Risky access by application
Hunting Queries: (5) Microsoft Sentinel hunting queries proactively search for risk-based behavior outside standard alerting schemas.
- Entity anomaly followed by Insider Risk Management alert
- Internet Service Provider anomaly correlated to data exfiltration alert
- Multiple entity-based anomalies
- Possible sabotage
- Sign-in risk followed by sensitive data access
Microsoft 365 Insider Risk Management Connector: Enables connection of Microsoft 365 Insider Risk Management to Microsoft Sentinel for single-pane visibility and aggregation of alerting data.
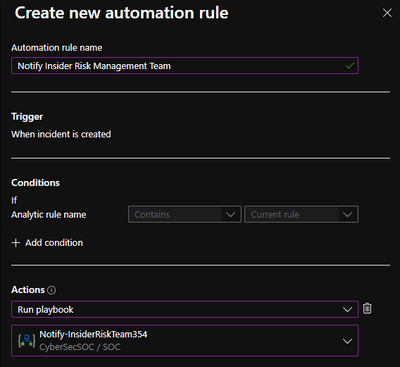
Playbook: Notify Insider Risk Management Team provides the capability to automatically monitor insider risk management alerts and notify the insider risk management team with the relevant details in both email and Microsoft Teams message.
Benefits
- Build/design insider risk management capabilities through existing tooling
- Detect, analyze, and respond to insider risk via intuitive workflows
- Risk-based behavior correlations across 25+ Microsoft products
- Advanced correlations for AI/ML, UEBA, and geospatial location of risk-based behavior
- Privacy and regulatory compliance alignment
- Query/Alert generation
- 250+ insider risk visualizations, recommendations, queries
- Single-click report exports
Audience
- Insider Risk Professionals: Risk-based behavior analysis
- Forensics Professionals: Investigations
- SecOps: Alert/Automation building
Getting Started
This content is designed to provide the foundation for building and operating an insider risk management program. Below are the steps to onboard required dependencies, enable connectors, review content, and provide feedback.
- Onboard Microsoft Sentinel and Microsoft 365 Insider Risk Management
- Access the Microsoft Sentinel Insider Risk Management Solution
- Microsoft Sentinel > Content Hub (Preview) > Select Microsoft Insider Risk Management Solution >Configure deployment options > create
- Enable the Microsoft 365 Insider Risk Management export alerts (preview) feature
- Enable the Microsoft Sentinel Insider Risk Management Connector
- Microsoft Sentinel > Data connectors >Search Microsoft 365 Insider Risk Management (Preview) > Open connector page > Connect
- Enable Microsoft Sentinel User Entity Behavior Analytics
- Configure an Microsoft Sentinel Watchlist via SearchKey columns
- Review the Insider Risk Management Workbook
- Microsoft Sentinel > Workbooks > Select Microsoft Insider Risk Management
- Review/Enable Analytics Rules
- Microsoft Sentinel > Analytics > Search Insider Risk Management
- Review Hunting Queries
- Microsoft Sentinel > Hunting > Queries >Search Insider Risk Management
- Review Playbook Automation
- Microsoft Sentinel > Automation > Active playbooks > Search Notify-InsiderRiskTeam > Enable
- Create Automation Rule
- Analytics > Search Insider Risk Management > Edit > Automated Response > Add new > Select Actions: Run Playbook > Select Notify-InsiderRiskTeam and configure automation options > Review > Save > Mirror configuration across all insider risk management analytics rules.
- Review the content and provide feedback through the survey
Frequently Asked Questions
- Are endpoint agents required?
- No, most analytics are geared towards common data tables including sign-in logs, Azure activity, Office activity, audit logs, and security alerts.
- Are additional products required?
- No, this solution leverages your existing Microsoft Security architecture. The recommended products provide additional use case enrichments, but only Microsoft Sentinel is required to get started.
- Is this solution RBAC/privacy compliant?
- Yes, there are no net new features as this solution is based in your existing Microsoft security architecture. Follow Microsoft RBAC best practice guidance for securing access to respective products and features.
- Where is the data stored?
- Does this solution provide historic recall?
- Yes, no additional algorithm training or configurations are required as this solution leverages your existing Microsoft security architecture. You can immediately gain insights from historic data sets in both Log Analytics Workspaces and Azure Data Explorer clusters. This capability also facilitates connected/disconnected use cases.
- Is Multi-Subscription, Multi-Cloud & Multi-Tenant supported?
- Yes, via Workbook Parameters, Azure Lighthouse, and Azure Arc
- Is custom reporting available?
- Yes, via guide, time, workspace, & subscription parameters.
- Is 3rd Party integration supported?
- Yes, workbooks and analytics are customizable for integration with 3rd party products.
- Is this available in government regions?
- Yes, this solution is in Public Preview in Commercial/Government regions
- Can this content be exported as a report?
- Yes, via Print Workbooks and Download Artifacts features.
- What is Dynamic Display?
- Dozens of queries are executed, and only panels with data display
- What rights are required to use this content?
- Microsoft Sentinel Contributor can create and edit workbooks, analytics rules, and other Microsoft Sentinel resources. Microsoft Sentinel Reader can view data, incidents, workbooks, and other Microsoft Sentinel resources. Note: Role-Based Access Control is controlled/configured in Microsoft Sentinel and Microsoft 365 Insider Risk Management. A secondary Microsoft Sentinel instance for insider risk management with cross-workspace query is recommended for additional access controls per organizational requirements.
Learn More About Insider Risk Management with Microsoft Security
- Drive efficiency and accelerate time to action in managing insider risks
- Insider Risk Solutions in Microsoft 365
- Identify advanced threats with User and Entity Behavior Analytics (UEBA) in Microsoft Sentinel
Posted at https://sl.advdat.com/3nknvWk