The Microsoft 365 Defender team is thrilled to share that we have made several enhancements to the advanced hunting experience. Our new and improved hunting page now has multi-tab support, smart scrolling, streamlined schema tabs, and more. Also, among these improvements, is the ”link to incident” feature, which allows you to link advanced hunting query results to specific incidents.
New advanced hunting page
In response to popular requests and feedback, we have made the hunting experience more streamlined. Below are the changes and updates:
Improved navigation
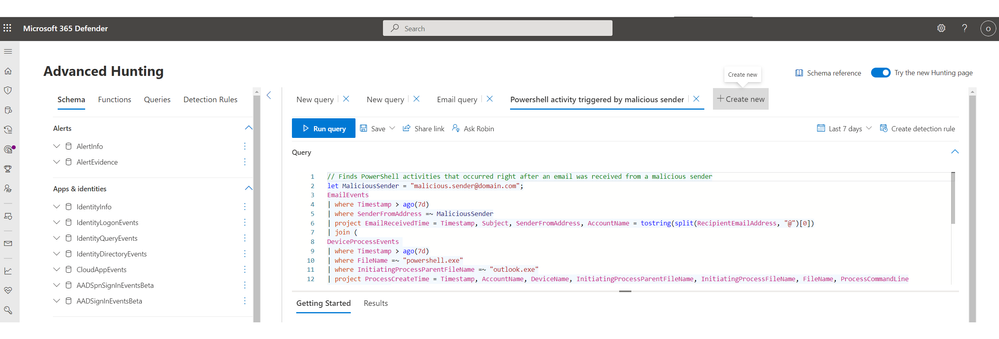
- Multi-tab support – You can now use multiple tabs. Every time you create a new query or open a saved query or a custom detection rule, it will launch in a new tab:
- Smart scrolling – Long query results are now rendered in a list that expands automatically as you scroll down, so you can focus on scanning the results.
You can even collapse the schema at the left to maximize your view of the whole screen:
- Streamlined schema tabs – Schema, functions, queries, and detection rules are now separate tabs so you can easily pivot between them.
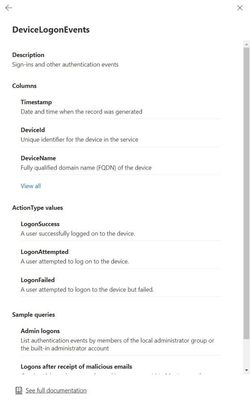
- Improved schema reference view – We’ve improved the schema reference view so you can easily navigate where you need to.
- More accessible “Getting Started” query set – You can now find the “Getting Started” query set next to the results tab. Selecting an operator in a sample query opens it in a new tab. You can always get back to the “Getting Started” section by switching to it from the Results view.
Fine-tune your queries
- Easier Kusto workflow – Query editor shortcuts and syntax highlight of new Kusto operators are now supported. The editor is updated to the latest version of Kusto editor.
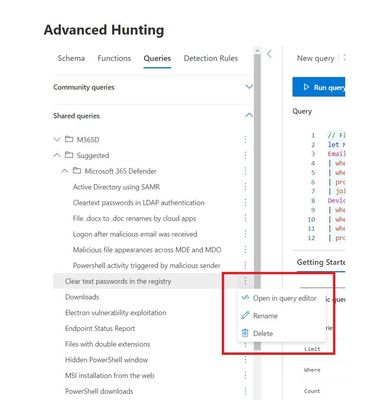
- Quick-edit queries – Select or double-click the three dots to the right of the query to open the query in the editor, delete the query, or rename the query.
- Refine your query by adding a filter from the results set – From your initial results set, go to the record side pane for one of the results, then select the three dots to the right of a column of interest to add it as a filter in your current query.
- Resource usage indicator - After running your query, you can see the execution time and its resource usage (Low, Medium, High) so you can tweak your query accordingly. High indicates that the query took more resources to run and could be improved to execute more efficiently.
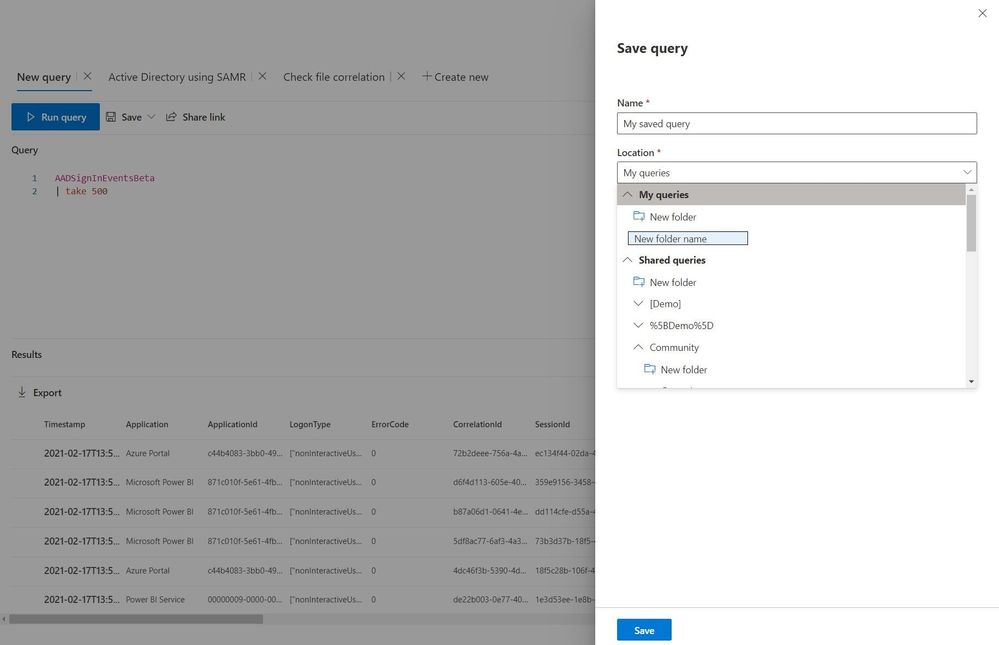
- Save query side pane – The Save query option is now located in a side pane for easier viewing.
For more information about working with query results, visit our full documentation at Work with advanced hunting query results.
Link query results to an incident
In addition to the enhancements above, we are happy to share that we have dded the much-requested option to link events from hunting to incidents. This capability can help you quickly add additional evidence for an ongoing investigation based on what you find in advanced hunting.
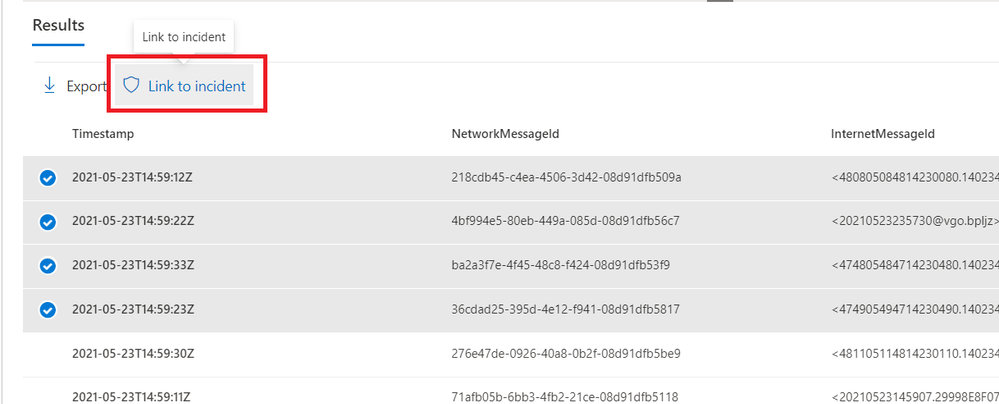
After you run your advanced hunting query, you can select which events are related to the investigation you are working on. The events you select can now be added as an alert to the incident of your choice.
1. Select the events you would like to add to an incident, and then select Link to incident.
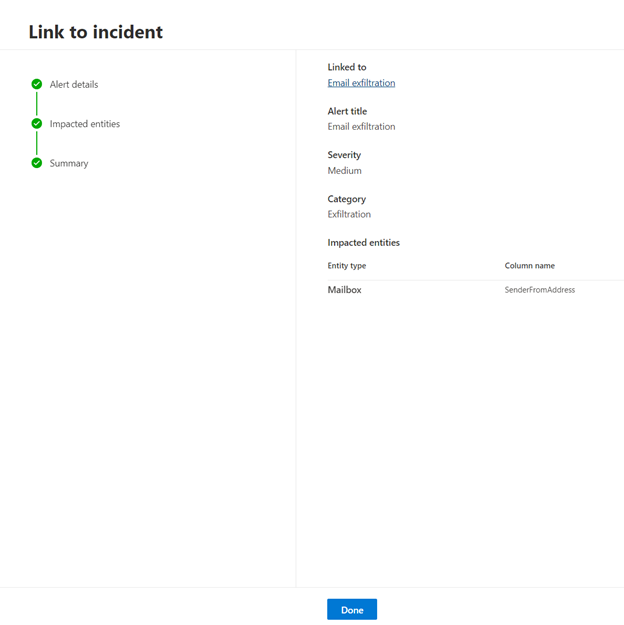
2. Select if you would like to link to an existing incident (Link to an existing incident). or to a new one (Create a new incident) Next, provide the alert details.
If you choose Link to an existing incident, you can select an existing incident from the dropdown menu. Type the first few characters of the incident name or ID to narrow down the options.
3. Next, select the impacted entities, which are the columns in your query results where you expect to find the main affected or impacted entity. Identifying which of these columns represent the main impacted entity helps the service aggregate relevant alerts.
For example, in our scenario, we are investigating events related to a possible email exfiltration incident, so the Sender is the impacted entity. We have four different senders, therefore four alerts will be created and linked to the chosen incident.
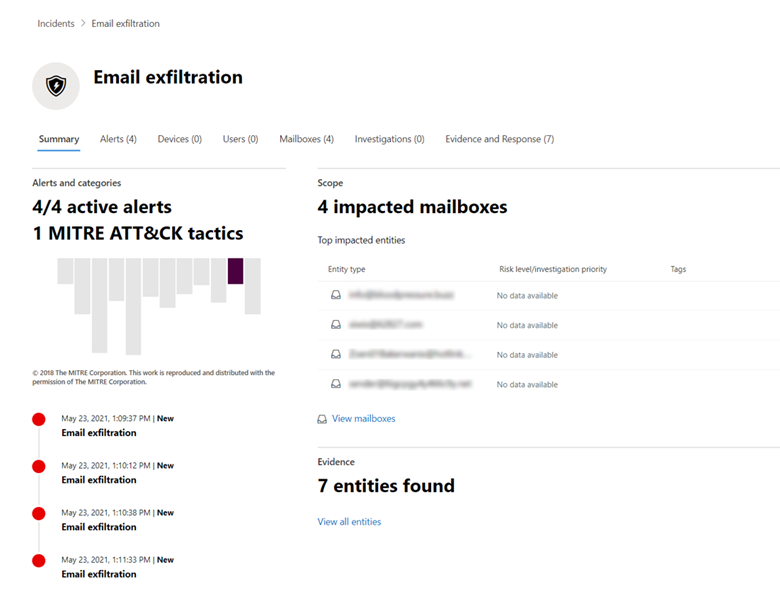
4. You can also select the incident name (Email exfiltration) to go to the incident that the events are linked to.
The four alerts, representing the four selected events, were linked successfully to a new incident.
For more information about the link to incident feature, visit our full documentation on Link query results to an incident.
NOTE: The expected use case for this feature does not currently include bulk linking of hunting query results to incidents. For example, you can currently link twenty results to a single incident. As we continue to develop how this feature helps you identify events that are likely to be related to an incident, we look forward to your feedback about the volume of events you reasonably expect to add manually to an incident.
Try the new hunting page now
The new hunting page is enabled by default. You can still use the old page by turning off the Try the new Hunting page toggle. If you prefer to continue using the old page, kindly share your feedback with us, so we can consider your reasons for preferring the old page.
These enhancements are available today for public preview customers. We would love to know what you think. Please share your feedback with us in the Microsoft 365 Defender portal or by emailing AHfeedback@microsoft.com.
- The Microsoft 365 Defender hunting team
Posted at https://sl.advdat.com/3BFrAZ2