Introduction
This is John Barbare and I am a Sr Customer Engineer at Microsoft focusing on all things in the Cybersecurity space. In this blog I will be focusing on Application Guard and the correct configuration/deployment for Microsoft Endpoint Configuration Manager (MECM). I have deployed with many of my customers and will show you what I have found useful in these deployments.
Microsoft Defender Application Guard
Microsoft Defender Application Guard is a hardware Isolation leveraging a Hyper-V enabled container. The container uses a lightweight Virtual Machine (VM) that is resistant to kernel attacks and runs on a separate kernel from the host. There are two types of modes - Enterprise Management Mode and Standalone Mode.
In Enterprise Management Mode, the administrator defines trusted sites through GPOs, Microsoft Intune, MECM, or your current mobile device management solution. Untrusted sites launch in the isolated Hyper-V container giving the user a malicious free browsing session.
In Standalone Mode, users start the isolated-based browser session independently without any administrators or policy configurations which I do not personally recommend as you are letting the user choose how to use your enterprise security tools and not Security Administrators. More Information on the details of Application Guard and pre-requisites can be found in my Tech Blog on App Guard for Office.
A method I use regularly with customers transitioning off GPOs (Group Policy Objects) and without access to Intune, is using MECM. This method is solidly reliable, easy to control Application Guard policy updates by scheduled interval or by manually trigger updates in CM Client Device. You could take the benefits of the SMS Agent to quickly deploy Application Guard and updates happen in several minutes – depending on connectivity. This seems to be a replaced solution if you face the obstacles when deploying Application Guard by other methods.
How the MECM Deployment of Application Guard Policy Works
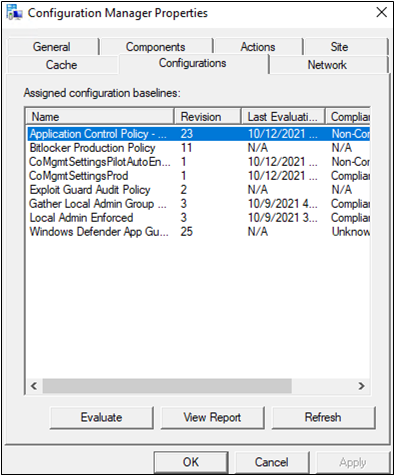
After the Application Guard Policy is deployed by the MECM Console and then on Clients of MECM, the machine policy will update the Application Guard Policy as Configuration Items. The following screenshot is shown in the Configuration Manager Client's Properties under Configuration Tab:
Just like with other Baseline Configuration Items, you could choose the Application Guard policy from the list, then click on the highlighted button to Refresh, Evaluate its compliance status, and View Report.
Whenever you make a change to the Application Guard Policy on the Client Device, you just need to use the Machine Policy Retrieval & Evaluation Cycle to get the latest version of Application Guard applied to the Client and manually evaluate the Application Guard Policy. The whole process usually only takes several minutes and it is convenient compared to Application Guard Deployment like GPOs.
Deployment Steps
The Application Guard Deployment Steps include:
- Create Application Guard Policy in MECM
- Configure Application Guard
- Define Network Boundaries: Cloud Resources (Cloud App URLs), Subnets, Enterprise Network Domain Names (AD (Active Directory) Domains FQDN (Fully Qualified Domain Name)), Neutral Resources (Search URLs, Redirection Endpoints’ URLs)
- Testing in Dev environment or small Proof of Concept
- Deployment Enterprise-wide
Create Application Guard Policy
In MECM Console
- Go to Asset and Compliance\Endpoint Protection
- Windows Defender Application Guard (Right Click)
- Create Application Guard Policy.
- Configure Application Behavior with the following options:
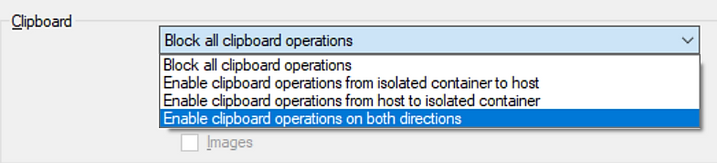
- Allow copy and paste of text, images from container’s clipboard to host direction or vice versa or both directions.
- Allow XPS Printing, PDF Printing, Local Printer Printing, Network Printer Printing from Applications running in Container or not.
- Allow Graphics from Virtual GPU or not.
- Allow save files from Applications running in Container to Host or not.
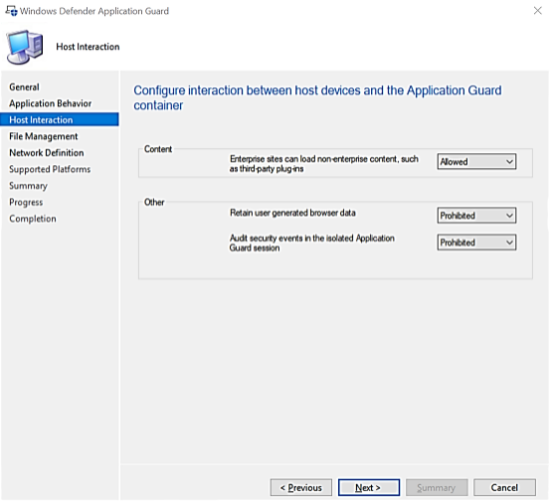
- Host Interaction
- Allow non-enterprise content, third-party plug-ins or not.
- Allow to save browser’s data originated from Virtual Container or not.
- Audit security events during sessions of Application Guard or not
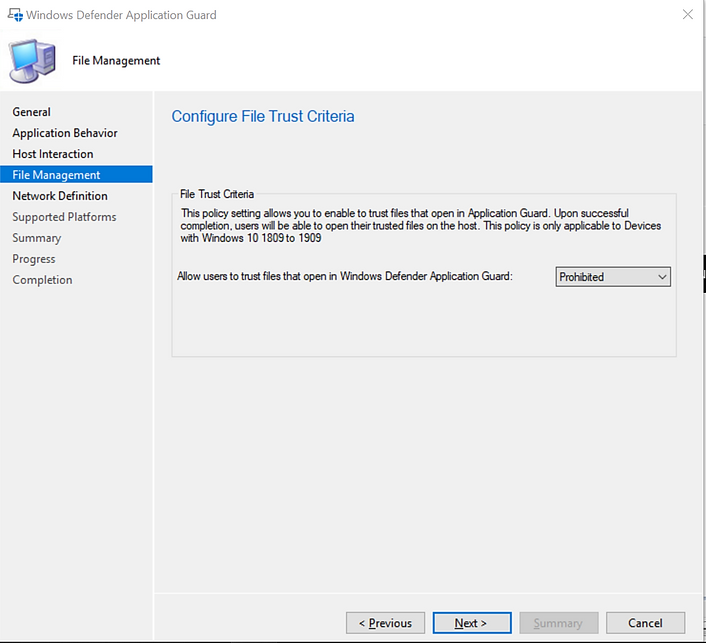
- File Management (obsolete in Windows 10 20H1 and later)
Starting in Configuration Manager version 1906, There's a policy setting that enables users to trust files that normally open in Application Guard. Upon successful completion, the files will open on the host device instead of in Application Guard.
- Allow trust files on Host to be opened by Application Guard:
Options:
- Prohibited: Don't allow users to mark files as trusted (default).
- File checked by antivirus: Allow users to mark files as trusted after an antivirus check.
- All files: Allow users to mark any file as trusted.
Known Issues with File Trust Management:
When you enable file management, you may see errors logged in the client's DCMReporting.log. The errors below typically do not affect functionality.
On compatible devices:
FileTrustCriteria_condition not found
- On non-compatible devices:
FileTrustCriteria_condition not found
FileTrustCriteria_condition could not be located in the map
FileTrustCriteria_condition not found in digest
- Devices running Windows 10, version 2004 will show failures in compliance reporting for Microsoft Defender Application Guard File Trust Criteria. This issue occurs because some subclasses were removed from the WMI (Windows Management Instrumentation) class MDM_WindowsDefenderApplicationGuard_Settings01 in Windows 10, version 2004
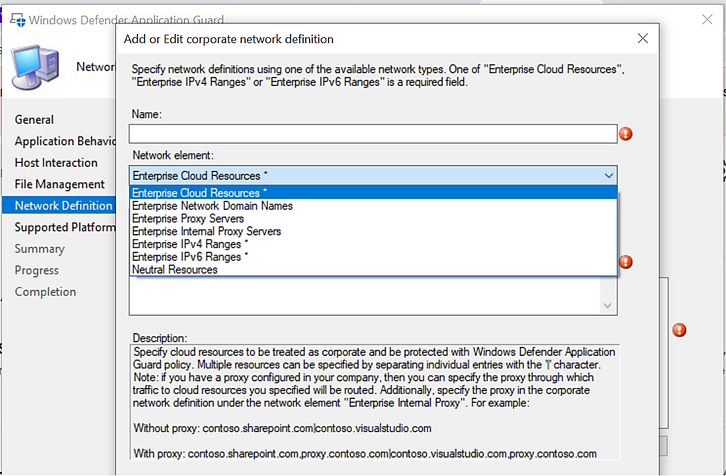
- Network Definition
- Enable auto-detect proxy server or not.
- Enable auto-detect Network IP (Internet Protocol) ranges or not
- Define Enterprise Network Boundaries and Resources:
Network Isolation Configuration
To support all sub-domains of Contoso we need a wildcard in the form of ".":
Ex: .contoso.com
for sub-sub-domain: ..contoso.com
|
Policy name |
Supported versions |
Description |
|
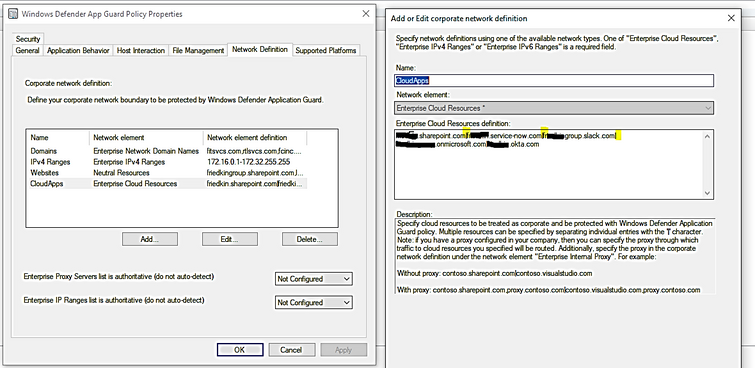
Enterprise Cloud Resource domains hosted in the cloud |
At least Windows Server 2012, Windows 8, or Windows RT |
Ex: contoso.sharepoint.com|my.adp.com|.adp.com|.service-now.com|.contoso.com In the above example, all in-house apps of contoso.com will be supported, like app1.contoso.com, app2.contoso.com, … Contoso.adp.com and Contoso.service-now.com will be supported. In our test, only one "." is accepted, sub-sub-domain (..) was not working. |
|
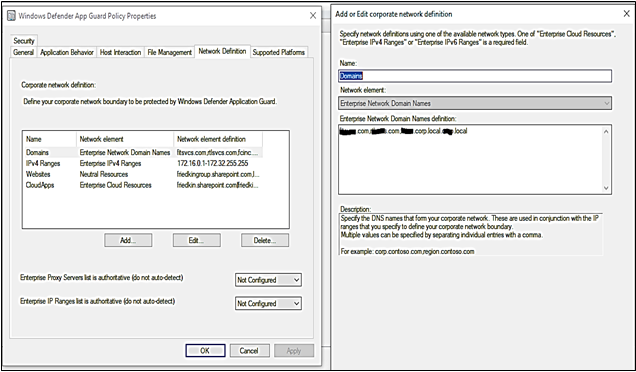
The private network ranges for apps |
At least Windows Server 2012, Windows 8. |
A comma-separated list of IP address ranges |
|
Domains categorized as both work and personal |
At least Windows Server 2012, Windows 8, or Windows RT |
|
|
Neutral Resources |
|
|
- Define Enterprise Cloud Resources:
- Define Network Domain Names:
- Define Neutral Resources:
Application Guard Limitations and Considerations for Office 365 and Windows 10
- Active content in documents like macros and ActiveX controls are disabled in Application Guard for Office. Users need to remove Application Guard protection to enable active content.
- Selecting web links (HTTP or HTTPS) does not open the browser.
- Files that are protected by Information Rights Management (IRM) are blocked by default. If users want to open such files in Protected View, an administrator must configure policy settings for unsupported file types for the organization.
- Any customizations to Office applications in Application Guard for Office will not persist after a user signs out or after the device restarts.
- Network connectivity is required for the first launch of Application Guard after installation. Connectivity is required for Application Guard to validate the license (E5).
- In the document's info section, the Last-Modified By property may display WDAGUtilityAccount as the user. WDAGUtilityAccount is the anonymous user configured in Application Guard. The desktop user's identity is not shared inside the Application Guard container.
- Updates to .NET might cause files to fail to open in Application Guard. As a workaround, users can restart their devices when they come across this failure.
- Some language keyboards based on Input Method Editor (IME) may not work:
- Vietnam Telex keyboard, Hindi phonetic keyboard, Bangla phonetic keyboard, Marathi phonetic keyboard, Malayalam phonetic keyboard, and several other IMEs not supported
- Only Windows 10 Enterprise will work on Application Guard Enterprise-Managed mode (with Application Guard Policy). The Windows 10 Pro edition only works on Application Guard Standalone mode.
- If an encryption driver prevents a VHD (Virtual Hard Disks) from being mounted or from being written to, Application Guard does not work and results in an error message
Conclusion
Thanks for taking the time to read this article and I hope you have a better understanding of the configurations required for deployment for Application Guard for MECM. Hope to see you in the next blog and always protect your endpoints!
Thanks for reading and have a great Cybersecurity day!
Follow my Microsoft Security Blogs: http://aka.ms/JohnBarbare and also on LinkedIn.
References
(0x80070013 ERROR_WRITE_PROTECT).
Application Guard Devices running Windows 10, version 2004 will show failures
Application Guard for Office 365 Limitations and Considerations
Configuration for Application Guard Network Isolation
Manage Application Guard policies - Configuration Manager | Microsoft Docs
Microsoft Defender Application Guard FAQ
Microsoft Application Guard Policy
Posted at https://sl.advdat.com/3kEskIy