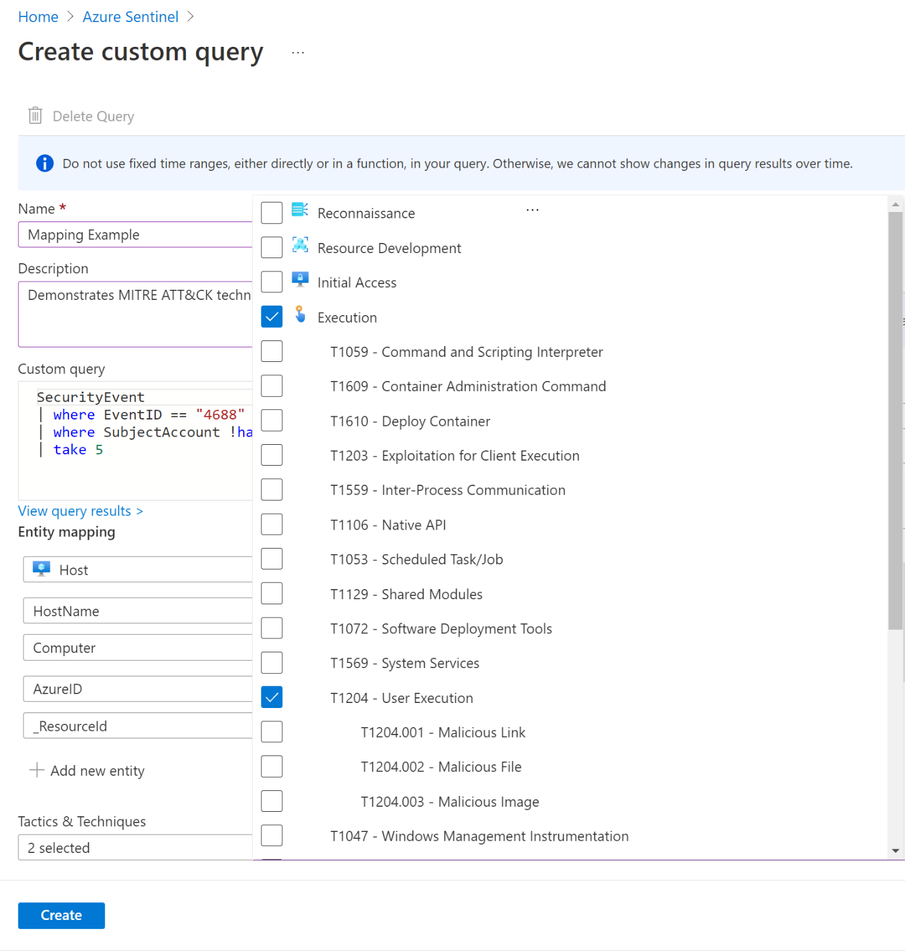
Now in preview, you can verify, identify, and address gaps in MITRE technique coverage by mapping your custom hunting queries to MITRE ATT&CK techniques.
Additionally, you can now investigate more types of entities while hunting by mapping the full set of entity types and identifiers supported by Microsoft Sentinel Analytics in your custom queries. This enables you to use bookmarks to explore the entities returned in hunting query results using Entity Pages, Incidents and the Investigation graph.
Customize your queries with MITRE ATT&CK techniques
Our users have told us repeatedly how important MITRE ATT&CK techniques are when identifying which specific kinds of malicious activity are present in their environments. This framework also helps analysts measure how many malicious behaviors can be identified and where improvements can be made.
That is why we have integrated MITRE ATT&CK techniques into the custom query and bookmark experiences. If a threat hunter wants to start a hunt for the user execution technique (T1204), in a couple clicks they can select T1204 from a drop-down menu containing all MITREv9 MITRE ATT&CK tactics, techniques and sub-techniques.
With this capability, when one of the mapped hunting queries generates results, you know specifically which MITRE ATT&CK techniques may be active in your environment.
Create a full MITRE coverage map for your built-in and custom hunting queries
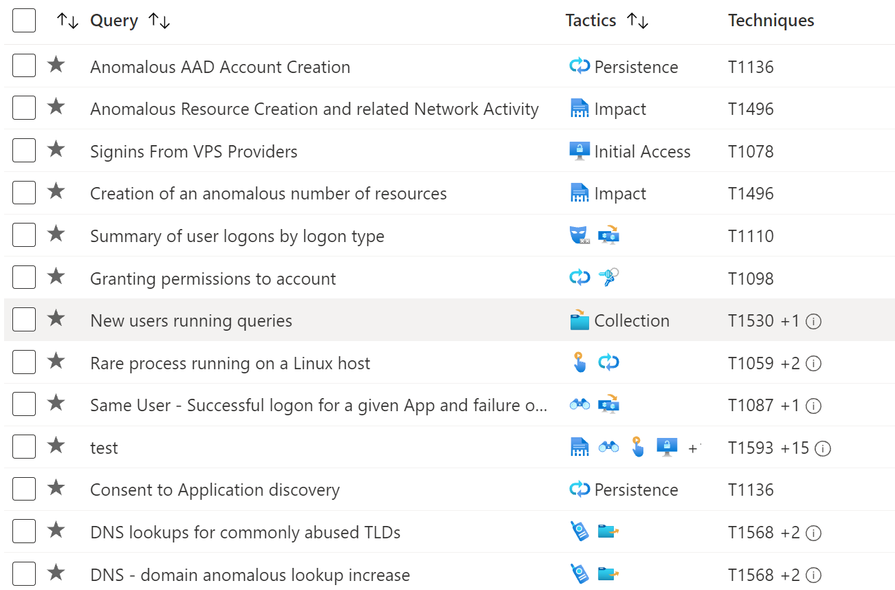
The ability to map your custom queries to techniques complements our recent announcement around our built-in hunting queries supporting MITRE ATT&CK techniques. Learn more here.
With both your built-in and custom queries mapped to techniques, you can measure your hunting query technique coverage. This is especially useful for identifying gaps and expanding your coverage by creating new custom queries.
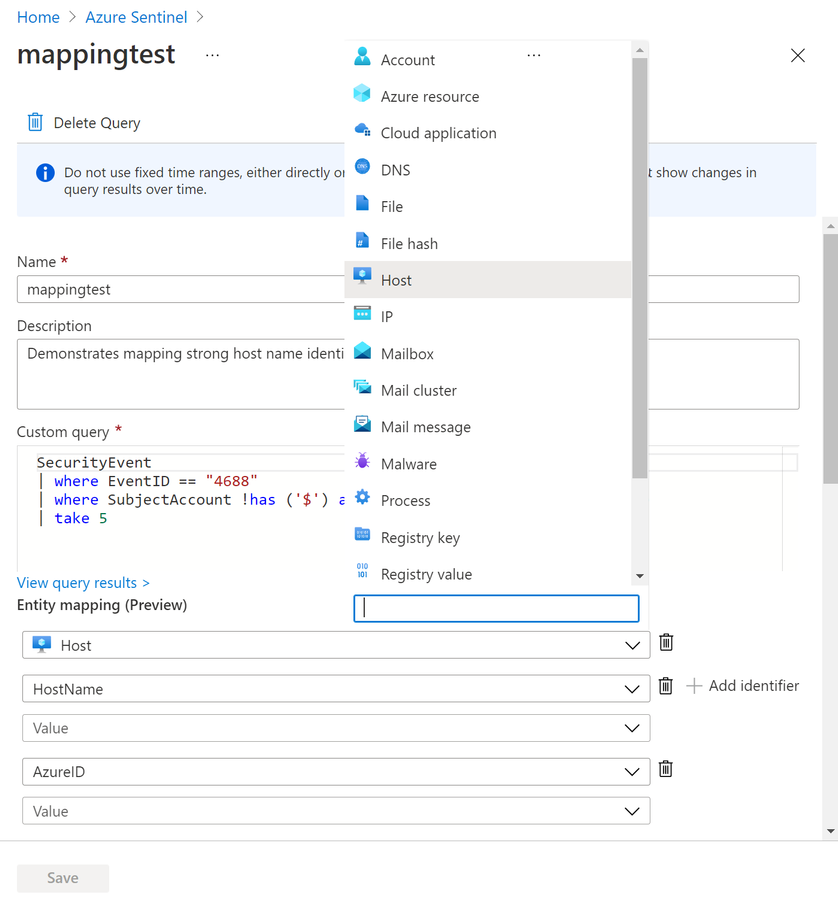
Hunt for more entities and entity types
Now that the hunter can hunt for the user execution technique (T1204) they will want to investigate further. This is where support for more entity types come in. When analysts can map query results to entities, they can use bookmarks to explore the entities returned in hunting query results using Entity Pages, Incidents and the Investigation graph. This helps you verify which results are worth exploring and which are dead ends.
Previously, users could only map one instance and one identifier for each of 4 entity types: account name, host, IP and URL. However, this is insufficient for strongly identifying a host or when hunting on a process or a file. You would want to strongly identify all 3 of these entity types, or more, when investigating techniques like user execution (T1204). Now you can map multiple instances of any of the entity types and identifiers supported by Microsoft Sentinel Analytic Rules.
To enable a faster and more convenient hunting experience when you create a bookmark, all the MITRE technique and entity mappings are inherited from the hunting query. This way there are no other steps needed to extract and preserve the entities for further investigation.
Further Reading
- Hunting capabilities in Microsoft Sentinel: https://docs.microsoft.com/en-us/azure/sentinel/hunting
- Microsoft Sentinel hunting queries on GitHub: https://github.com/Azure/Azure-Sentinel/tree/master/Hunting%20Queries
- Hunting bookmarks: https://docs.microsoft.com/en-us/azure/sentinel/bookmarks
Posted at https://sl.advdat.com/3kl1h4R