Hunting Dashboard Refresh
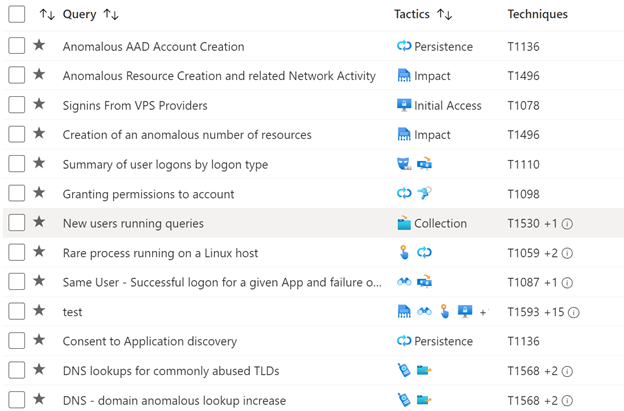
Now in GA, a refreshed hunting query experience helps you find undetected threats more quickly and with more precision. Hunting queries are now mapped to MITRE ATT&CK techniques and sub-techniques. This helps you identify which behaviors are present and your overall MITRE coverage for hunting. You can run all your queries at once, then filter on MITRE techniques and queries that had significant changes in the last 24 to 48 hours. This makes it much easier to zero in on the most promising leads for hunting.
Hunt for specific MITRE ATT&CK techniques
Our users have told us repeatedly how important MITRE ATT&CK techniques are to identifying which specific kinds of malicious activity are present in their environments. It also provides a framework to measure how many malicious behaviors can be identified, and where improvements can be made.
To respond to this need, we are mapping our built-in hunting queries with MITRE ATT&CK techniques and sub-techniques. With this capability, when one of the mapped hunting queries generates results, you know specifically which MITRE ATT&CK techniques may be active in your environment.
Also, now in preview, you can map your custom hunting queries to MITRE ATT&CK techniques and sub-techniques. See preview details here.
Create a full MITRE coverage map for your built-in and custom hunting queries.
These new capabilities enable you to enumerate the full list of techniques covered by your hunting queries. This is especially useful for identifying gaps and seeing progress as you create new custom queries and install hunting queries from solutions and Azure Sentinel’s GitHub community.
Hunting queries as starting points for authoring analytics
Along your MITRE ATT&CK technique journey you may find that you have hunting query coverage for a technique for which you don’t have analytic coverage. In these cases, you can use a hunting query as an initial starting point to develop a new analytic rule. By refining the query and filtering out noise, you can develop high fidelity detections.
Run all your hunting queries at once, or just a few to focus on specific behaviors over time
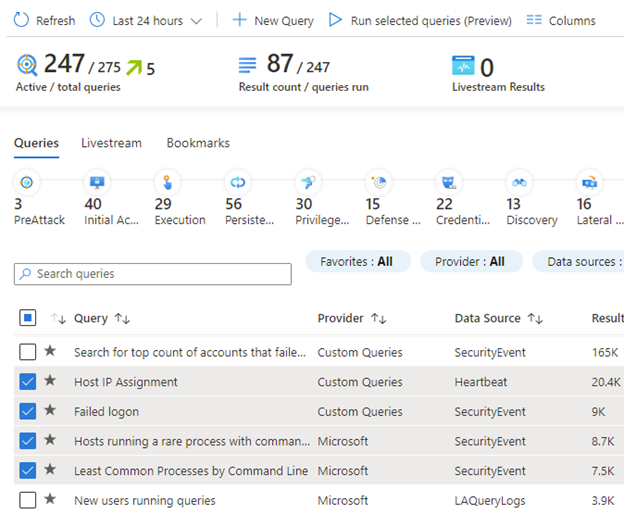
We have restored the “Run all queries” capability to the hunting dashboard, enabling you to run as many hunting queries as you want at one time to get a full view of all the potentially malicious behaviors that you have queries for.
Alternatively, you can run a selected subset of queries, such as for a recent attack campaign. This is especially useful when you want to run queries over a large set of data or a long time period.
See which MITRE tactics are present in your environment at a glance
We updated the MITRE ATT&CK tactic bar to show only the tactics related to the queries selected by your filters.
Want to quickly see which tactics may be active in your environment? Run all queries, then filter by queries with results. The new tactic bar updates to show only tactics with query result counts.
Identify spikes in potentially malicious activity
Want to identify spikes in activity between the last 24 and 48 hours? Filter on the results delta or results delta percent fields to show queries with notable changes in result counts. This helps you zero on the queries most likely to help you find evidence of malicious activity.
Further Reading
- Hunting capabilities in Azure Sentinel: https://docs.microsoft.com/en-us/azure/sentinel/hunting
- Azure Sentinel hunting queries on GitHub: https://github.com/Azure/Azure-Sentinel/tree/master/Hunting%20Queries
Posted at https://sl.advdat.com/3bQjwKz