Microsoft Cloud App Security, also known as MCAS, helps an IT of an organization by generating alerts for any suspicious activity/Policy violation/Misuse of data by their users; there are challenges in addressing the same in a timely manner due to the need of manual intervention by IT. This not only affects the overall resolution time of the alerts but may also affect the business for not addressing them on time. We can overcome this challenge by integrating Microsoft Teams with the MCAS to notify admins/Security Operation Center of any policy violations or suspicious activities being reported there, increasing the response and resolution time.
How it works?
MCAS has the ability to proactively monitor data and applications of an organization and then automatically enforce policies including classifying documents and messages that contain confidential and sensitive information like user’s credit card number and social security number etc. When we integrate the MCAS with Teams with the help of Microsoft Flow, it automatically notifies the admins/Security Operation Center about an issue by sending a message to a channel in Teams whenever an alert triggered in the MCAS.
Prerequisites
- A Valid Microsoft Power Automate plan - please refer the link below to know more in detail about the MS Power Automate plan
https://flow.microsoft.com/en-us/pricing/ - A dedicated Teams ID, ideally of Admins/Security Operation Center who should be notified in Microsoft teams about the MCAS Alert
- A dedicated Service Account with Security Administrator role for enabling integration between Microsoft Teams and MCAS
Steps to integrate Microsoft Teams with MCAS
Step 1: Generate your API token in Microsoft Cloud App Security
- Open MCAS portal(portal.cloudappsecurity.com)using your admin account
- Click the settings icon in the upper right hand corner of the portal
- Select “Security Extensions”
- Click on “API Tokens” Tab and click the blue + button on the upper right hand corner of the token list
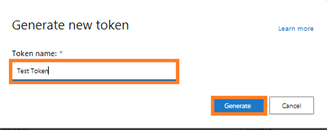
- Name your token and click Generate
- Save your token in a secure place, as it is needed in step 2 below.
Step 2: Create your trigger in Microsoft Flow
- Go to Flow.Microsoft.com
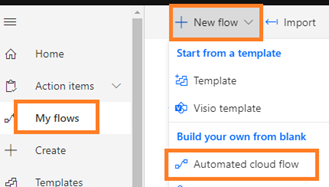
- Click “My Flows” in the left sidebar and click the “+ New” button and choose “Automated cloud flow” from drop down list
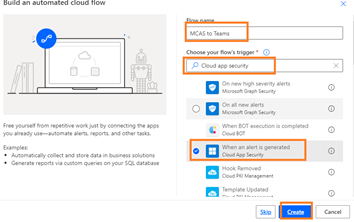
- Enter the Flow name and In the flow’s trigger search bar, search for “Cloud App Security” then select the trigger “When an alert is generated” and click on Select
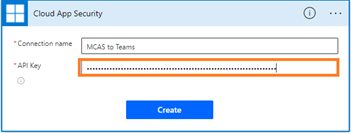
- When prompted, enter Connection name and your API token that were saved in Step 1
Step 3: Create the Teams message action in Microsoft Flow
- Click on “New step” , search for Teams in the search bar under Choose an Operation and click the Microsoft Teams icon
- Under Actions, select “Post Message in chat or channel”
- Enter “Post as” and “Post in”, select Team ID and Chanel ID
Note: Team ID and Channel ID will pull information from your instance of teams and teams respectively.
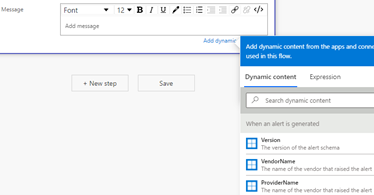
- Enter your message
- Once you click in the message box, you will be given a menu that lets you select Dynamic Content or Expressions
- The dynamic content list gives you any information available from the CAS alert.
- Click Alert Display Name, and Alert Category
Note: These will create blocks in the message box. You can enter any ancillary information you want here as well
- Click Save.
Step 4: Connecting the Flow in Cloud App Security
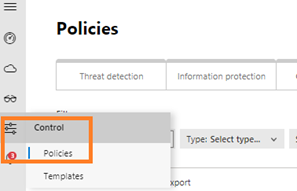
- Go to MCAS portal, portal.cloudappsecurity.com, click on “Control” in the left sidebar and select “Policies”
- Find the policy that you want to trigger under “Policy” the flow and select it
- In the Alerts section, select “Send Alerts to Power Automate” and In the select Playbooks dropdown, choose the name of the flow you created in step 3 and click “Update”
Bio:
Muniraja Krishnappa has 20+ years of experience across architecting, operations and maintenance of Microsoft Messaging, collaboration, and cloud Technologies. He is currently serving as a Sr. Infrastructure Architect with Cognizant Technology Solutions, with technical expertise across architecting and administration of Microsoft Exchange (On-premises), Microsoft 365(across Exchange Online, Cloud App Security, Azure AD, Power Automate platform and Graph API automation) and has been working for few of the Fortune 500 clients.
To write your own blog on a topic of interest as a guest blogger in the Microsoft Teams Community, please submit your idea here: https://aka.ms/TeamsCommunityBlogger