We recently announced the preview of Azure Private Link support for the Hyperscale (Citus) option in our Azure Database for PostgreSQL managed service.
Private Link enables you to create private endpoints for Hyperscale (Citus) nodes, which are exhibited as private IPs within your Virtual Network. Private Link essentially brings Hyperscale (Citus) inside your Virtual Network and allows you to have direct connectivity from your application to the managed database service.
With Private Link, communications between your Virtual Network and the Hyperscale (Citus) service travel over the Microsoft backbone network privately and securely, eliminating the need to expose the service to the public internet.
If you’re not familiar, Hyperscale (Citus) is an option in the Azure Database for PostgreSQL managed service that enables you to scale out your Postgres database horizontally. Hyperscale (Citus) leverages the Citus open source extension to Postgres, effectively transforming Postgres into a distributed database.
As with all the other Azure PaaS services that support Azure Private Link, the Private Link integration with Hyperscale (Citus) in our PostgreSQL managed service implements the same battle-tested Azure Private Link technology, provides the same consistent experiences, and has the following features:
- Private access from Virtual Network resources, peered networks, and on-premise networks.
- In-built data exfiltration protection for Azure resources.
- Predictable private IP addresses for PaaS resources.
- Consistent and unified experience across PaaS services.
To learn more about Private Link technology and PaaS services that support Private Link functionality, you can review the general Azure Private Link documentation.

In this “how to” blog post about the Private Link preview1 for Hyperscale (Citus), you can learn how to bring your Hyperscale (Citus) server groups inside your Virtual Network, by creating and managing private endpoints on your server groups. You will also get to know some of the details to be aware of when using Private Link with Hyperscale (Citus).
Let’s take a walk through these 4 scenarios for using Azure Private Link with Hyperscale (Citus):
- How to create a Hyperscale (Citus) server group with a Private Endpoint
- How to add a Private Endpoint for an existing server group via Networking blade
- How to add a Private Endpoint for an existing server group via Private Endpoint resource creation
- How to manage a Private Endpoint Connection
Prerequisites
Before you can create a Hyperscale (Citus) server group with a private endpoint—or add a private endpoint for an existing Hyperscale (Citus) server group—you first need to setup a resource group and a virtual network with a subnet that has enough available private IPs:
- The resource group will hold your Hyperscale (Citus) server group.
- The virtual network is used to allocate private IPs for your private endpoints.
How to create a Hyperscale (Citus) server group with a Private Endpoint
As the database admin or owner, you can create a private endpoint on the coordinator node when you are provisioning a new Hyperscale (Citus) server group. For help on how to provision a Hyperscale (Citus) server group, take a look at this tutorial.
In the “Networking” tab (Figure 2 below), select by clicking the “Private access” radio button for the “Connectivity method”.

A “Create private endpoint” screen will appear (Figure 3 below). If this screen doesn’t appear, or you close it accidentally, you can manually re-open it by clicking “+ Add private endpoint” in the “Networking” tab showing above.
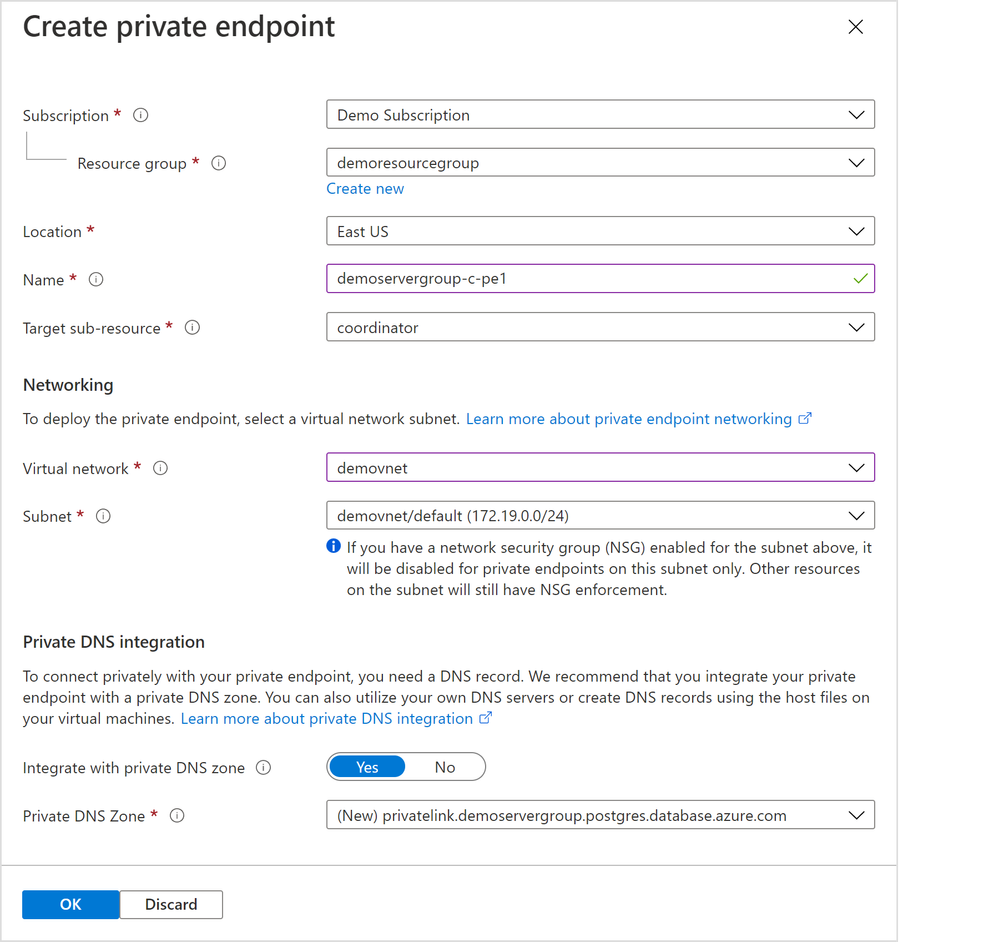
Select appropriate resource group, location, name, and networking values for your private endpoint. If you are just experimenting with Citus on Azure, the default values should work for most cases.
Please pay special attention to the Networking configurations. The networking configurations specify the Virtual Network and Subnet for the private IP from which the new private endpoint will be allocated. For example, you need to make sure there are enough private IPs available in the selected subnet.
The rest of the steps are exactly the same as in the tutorial for creating a Hyperscale (Citus) server group.
How to add a Private Endpoint for an existing server group via the Networking blade
You can also create a private endpoint on a node in an existing Hyperscale (Citus) server group.
In fact, if you need to create a private endpoint on a worker node in a cluster, you must first create the database cluster and then subsequently add the private endpoint to the worker node.
There are two places you can do this, and the first place is through the “Networking” blade for the Hyperscale (Citus) server group.
1. Navigate to the “Networking” blade for the Hyperscale (Citus) server group (Figure 4 below), click “+ Add private endpoint”.

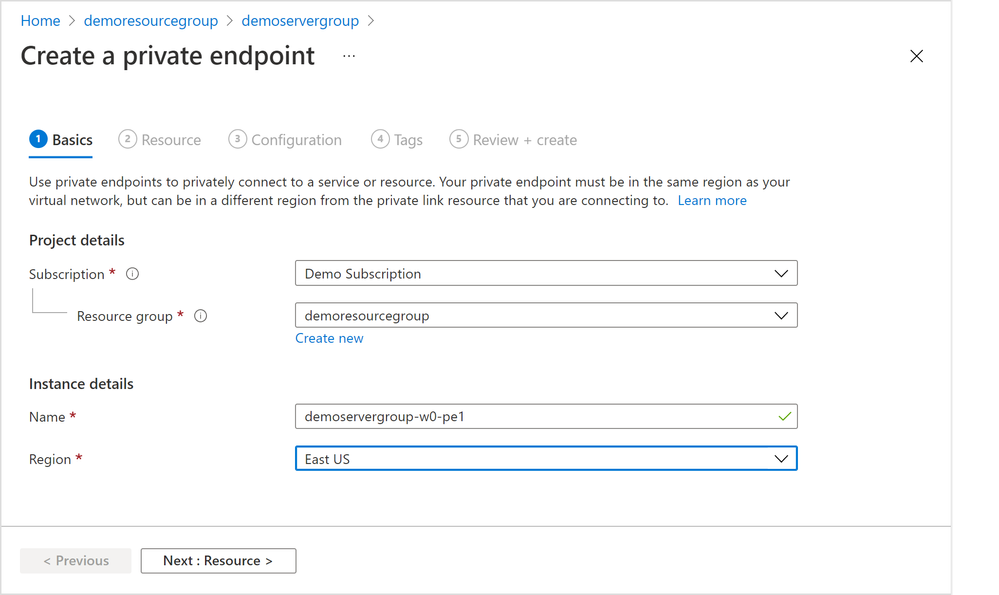
2. In the “Basics” tab (Figure 5 below), select the appropriate “Subscription”, “Resource group”, and “Region” information where you want your private endpoint to be created, and enter a meaningful “Name” for the private endpoint, e.g., you can use a naming convention like “ServerGroupName-NodeName-pe”. Select “Next: Resource >”.
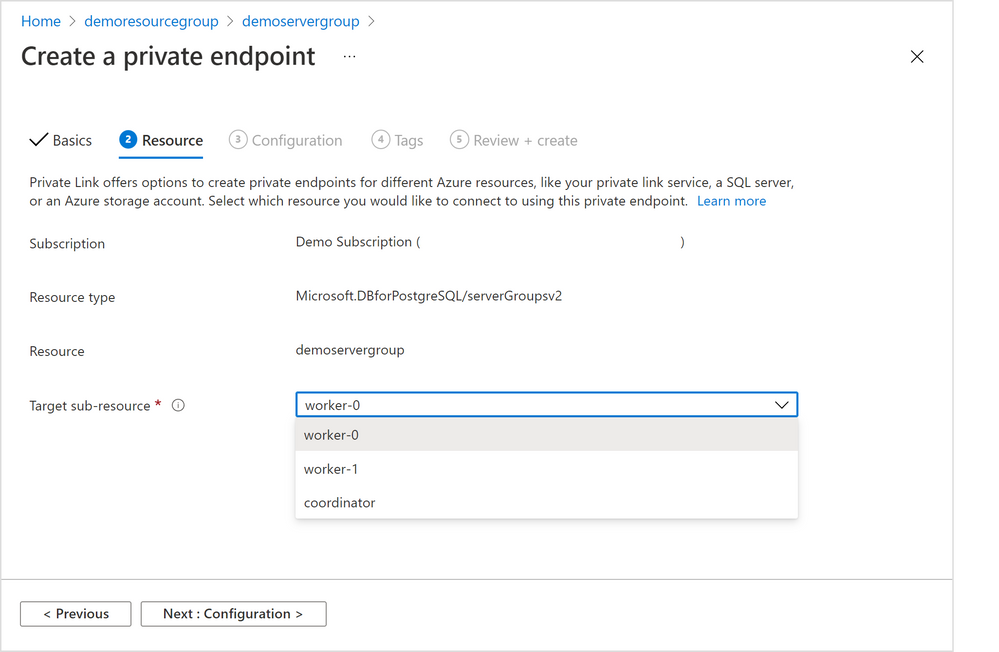
3. In the “Resource” tab in the screenshot below (Figure 6 below), choose the target node of the Hyperscale (Citus) server group. Generally, “coordinator” is the desired node unless you have reasons to access to the Hyperscale (Citus) worker nodes. (If you need private endpoints for all the worker nodes, you will need to repeat this process for all target sub-resources). Select “Next: Configuration >”.
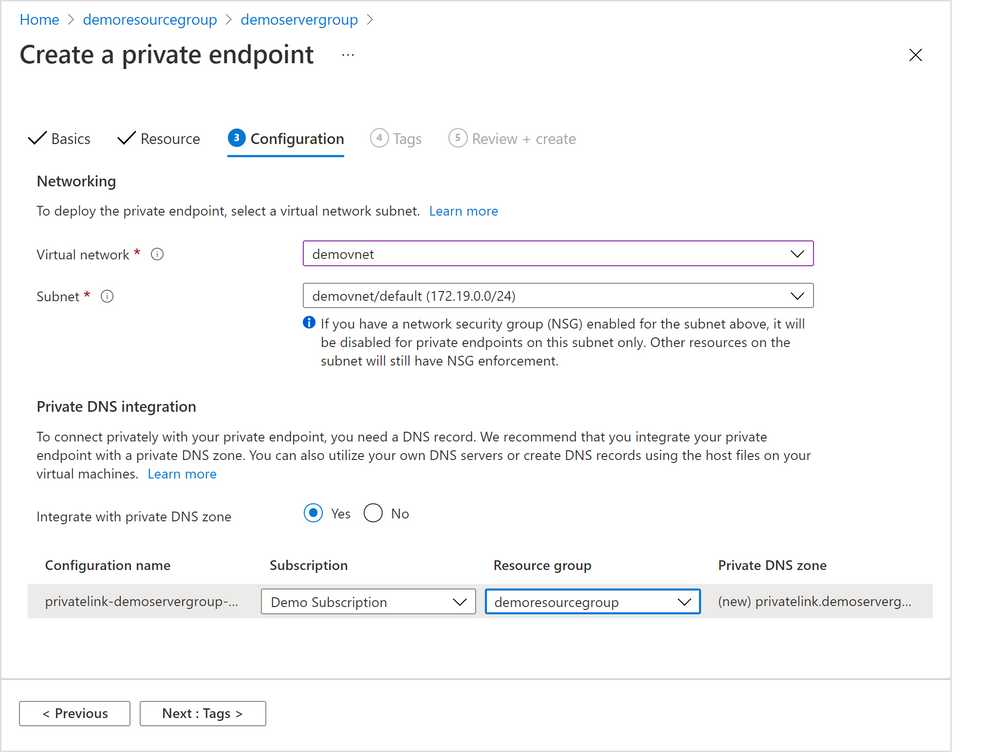
4. In the “Configuration” tab below (Figure 7 below), choose the “Virtual network” and “Subnet” from where the private IP for the private endpoint will be allocated.
It’s not required, but highly recommended to create all your private endpoints for the same Hyperscale (Citus) server group using the same Virtual Network / Subnet.
Select the “Yes” radio button next to “Integration with private DNS zone” to have private DNS integration.
5. Finish the rest of the steps by adding any tags you want, reviewing the settings and selecting “Create” to create the private endpoint.
How to add a Private Endpoint for an existing server group via Private Endpoint resource creation
If you need to create private endpoints for more than one Hyperscale (Citus) server group—or for multiple Azure managed services, perhaps you also manage other databases besides Postgres—you can choose to create a private endpoint using the generic private endpoint creation process provided by the Azure Networking team.
You might also want to use generic private endpoint resource creation if you don’t have access to the Hyperscale (Citus) server group, e.g., you are network admin instead of database admin, or you need to create a private endpoint to a database in another subscription you don’t have access to.
1. From the home page of Azure portal, select the “Create a resource” button and search for “Private Endpoint”. Click “Create” button (Figure 8 below) to start creating a private endpoint.
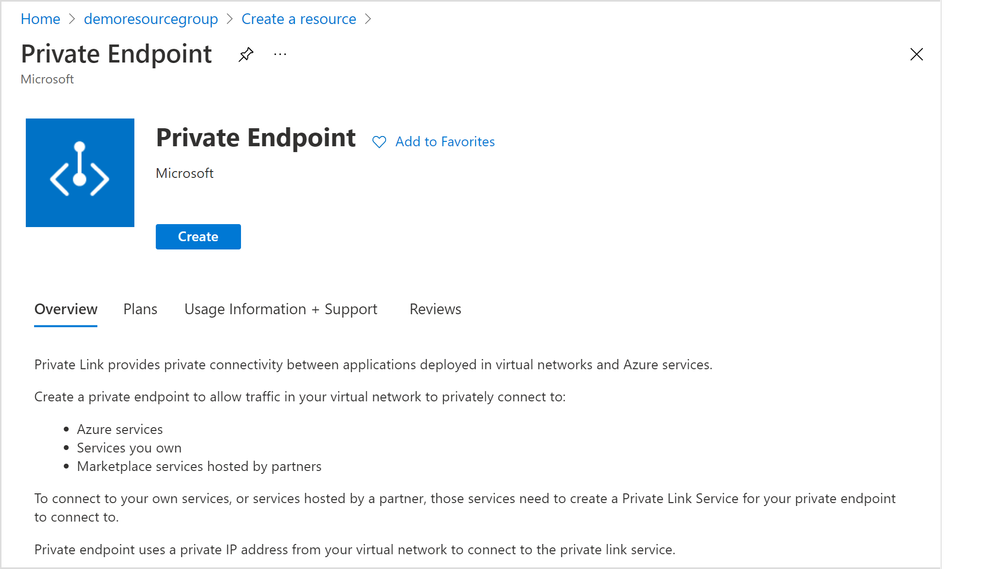
2. All the rest of the steps should be the same as illustrated in the section above, except for the “Resource” tab step (Figure 9 below).
For the “Resource” tab step, you will need to select the “Connection method” based on your permission to the Hyperscale (Citus) server group on which you want to create a private endpoint. You can learn more in the “Access to a private link resource using approval workflow” docs.
- “Connect to an Azure resource in my directory”: if you own or have access to the Hyperscale (Citus) server group (e.g., you are the server group admin), you can choose “Connect to an Azure resource in my directory”. For the “Resource Type” field, please select “Microsoft.DBforPostgreSQL/serverGroupsv2” from the dropdown; for the “Resource” field, you can browse to find the server group on which you want to create a private endpoint.
- “Connect to an Azure resource by resource ID or alias”: if you don’t own or don’t have access to the Hyperscale (Citus) server group, you will need to choose “Connect to an Azure resource by resource ID or alias.” Please obtain the resource ID for the Hyperscale (Citus) server group from the Hyperscale (Citus) server group owner.

How to manage a Private Endpoint Connection
As mentioned above, there are different connection and approval methods based on your permission on the Hyperscale (Citus) server group.
- Automatic approval: the private endpoint connection will be approved automatically if you own or have permission on the server group.
- Manual approval: the private endpoint connection request will go through the manual-approve workflow, if you don’t have the permission required and would like to connect to the server group.
As the Hyperscale (Citus) server group owner or admin, you can manage all the private endpoint connections created on your server group.
- Pending connections: if the “Connection state” for a private endpoint connection is “Pending”, you will be able to “Approve”, “Reject”, or “Remove” the connection.
- Approved connections: if the “Connection state” for a private endpoint connection is “Approved”, you will be able to “Reject” or “Remove” the connection.
Just like adding a Private Endpoint for an existing server group, there are two places you as the Hyperscale (Citus) server group admin can manage the private endpoint connections.
The 1st place is again using the Hyperscale (Citus) server group’s “Networking” blade (Figure 10 below).

The 2nd place you can manage the private endpoint connections is the “Private Link Center”. Search “Private Link” services from the Azure portal, and you will be navigated to the “Private Link Center”.
1. The “Pending connections” blade (Figure 11 below) in the “Private Link Center” lists all the private endpoints that are in “Pending” state. You can filter based on “Subscription”, “Name”, and “Resource Type” to the private endpoints you want to manage.

2. The “Private endpoints” blade (Figure 12 below) in the “Private Link Center” lists all the private endpoints in all connection state. Again, you can filter based on “Subscription”, “Name”, and “Resource Type” to the private endpoints you want to manage.

Private Link is now in preview for Hyperscale (Citus) in our PostgreSQL managed service
With the preview of the Azure Private Link for Hyperscale (Citus), you are now empowered to bring your Hyperscale (Citus) server groups—new or existing—into your private Virtual Network space. You can create and manage private endpoints for any of or all the Hyperscale (Citus) database nodes.
If you want to learn more about using Hyperscale (Citus) to shard Postgres on Azure, you can:
- Read our Azure docs for Hyperscale (Citus)
- Create your first Azure Database for PostgreSQL – Hyperscale (Citus) server group
- Review the multiple layers of data access and security that Hyperscale (Citus) provides in Azure Database for PostgreSQL
Your feedback and questions are welcome. You can always reach out to our team of Postgres experts at Ask Azure DB for PostgreSQL.
Footnotes
-
At the time of publication, Private Link is in preview in many Hyperscale (Citus) regions and will be rolling out to the rest of the Hyperscale (Citus) in the upcoming months. ↩
