In May 2021, Microsoft announced a new threat monitoring protection for SAP systems in Microsoft Sentinel.
Since then, we’ve continuously increased our capabilities, and today another important feature goes to Public Preview.
Microsoft Sentinel collects logs and alerts from all its connected data sources, analyzes them, and builds baseline profiles of your organization’s entities, such as users, hosts, IP addresses, and applications, across time and peer group horizons. Microsoft Sentinel can identify malicious activity and help you determine if an asset has been compromised and evaluate the potential impact of any given compromised asset (its “blast radius”). Armed with this information, you can effectively prioritize your investigation and incident handling.
Microsoft Sentinel’s core features can be leveraged together with the SAP logs that are connected to your Microsoft Sentinel workspace. The UEBA features in Microsoft Sentinel eliminates the drudgery from your analysts’ workloads and the uncertainty from their efforts, and delivers high-fidelity, actionable intelligence, so they can focus on investigation and remediation.
This combined support enables customer entity behavior analytics insights through the SAP system across the entire enterprise, correlated with other sources, devices and applications in the Microsoft Sentinel workspace.
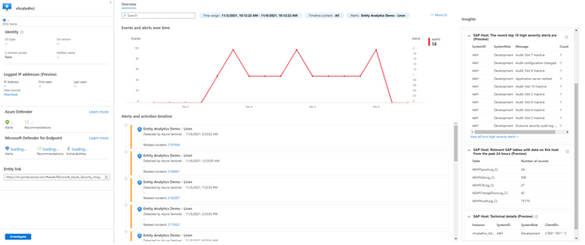
The greatest value of our new support with SAP logs for UEBA is that for the first time, when a user has the same email for their SAP accounts and for their Azure Active Directory, the email address is automatically associated to the AD account and we know users have access to the SAP systems. This knowledge is important, because if this user is hacked, we know that the SAP systems are also at risk. On the UEBA page in Microsoft Sentinel, when we select a user, we can see the user’s top 10 security log entries in the account insights, along with related alerts on the timeline. There is also an option to search insights on a specific time range.
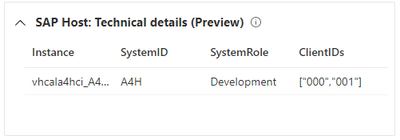
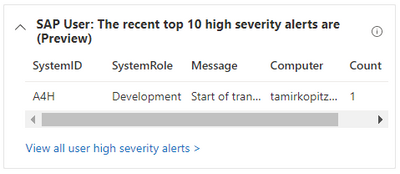
In addition to user insights, in case a host runs SAP, we provide insights regarding that as well, such as top 10 high severity security logs entries, how many records ingested to SAP tables and details about the host, like system ID and its role (production, testing, development etc.). This is also a huge benefit, it is relevant for an optional attack if happens, to evaluate risks and to know which hosts in your company runs SAP systems.
We just launched this UEBA feature in public preview, but we are working to add more capabilities to this feature, more functionalities to enrich the insights for the UEBA entities pages.
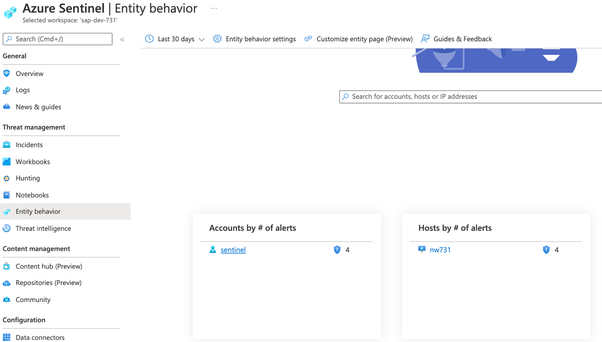
To view the UEBA entities pages, please click on the entity behavior button on the left side of the workspace:
And then you can select to view the users’ insights or the hosts insights:
If we click the user, this is the UEBA entity page in Microsoft Sentinel workspace:
On the right side of the page, you’ll find insights regarding the user or host, depends on your choice. These are some examples for the host insights: you can find the different tables with number of records per table:
Technical details regarding the different hosts:
Top 10 high severity alerts for the hosts:
Learn more
Call for action
- Deploy SAP continuous threat monitoring
- Identify advanced threats with User and Entity Behavior Analytics (UEBA) in Microsoft Sentinel