Insider risk management remains at the forefront of priorities in protecting federal information systems. Federal requirements such as Executive Order 13587 and the National Industrial Security Program Operating Manual (NISPOM) provide respective guidance and requirements for defending against insider risk scenarios. Recent work trend indexes demonstrate shifts between on-premises and remote work during the pandemic. These indexes also highlight workforce exhaustion due to extended remote work hours and challenges to work-life balance. These shifts increase insider risk scenarios including both witting (intentional) and un-witting (accidental or negligent) circumstances. Managing these risks and aligning to government compliance directives requires development of comprehensive insider risk management capabilities across Zero Trust architectures.
Managing and minimizing risk in your organization starts with understanding the types of risks found in the modern workplace. Some risks are driven by external events and factors that are outside of direct control. Other risks are caused by internal events and user activities that can be minimized and avoided. Some examples are risks from illegal, inappropriate, unauthorized, or unethical behavior and actions by users in your organization. These behaviors include a broad range of internal risks from users:
- Leaks of sensitive data and data spillage
- Confidentiality violations
- Intellectual property (IP) theft
- Fraud
- Insider trading
- Regulatory compliance violations
Zero Trust architectures are based in "assume breach" fundamentals which reinforce the requirements for tripwires and multiple levels of trust validations for access to resources. Cloud and hybrid-based computing environments facilitate these approaches because assets must communicate with the cloud by the fabric. The Microsoft Sentinel: Microsoft Insider Risk Management Solution leverages comprehensive signals across the entire computing environment, including identity, endpoints, applications, data, infrastructure, networks, and automation platforms. Extensible technologies such as Azure Arc, Microsoft Defender for Endpoint, and Microsoft Cloud App Security extend coverage into hybrid, on-premises, and multi-cloud environments. Advanced correlations in Artificial Intelligence, Machine Learning, Fusion, UEBA, and geospatial orientation are applied to aggregated signals for granular analysis of risk-based behavior across numerous products.
This solution enables insider risk management teams to investigate risk-based behavior across 25+ Microsoft products. This solution is a better-together story between Microsoft Sentinel and Microsoft 365 Insider Risk Management. The solution includes the Insider Risk Management Workbook, (5) Hunting Queries, (5) Analytics Rules, (1) Playbook automation and the Microsoft 365 Insider Risk Management connector. While only Microsoft Sentinel is required to get started, the solution is enhanced with numerous Microsoft offerings, including, but not limited to:
- Microsoft 365 Insider Risk Management
- Microsoft 365 Communications Compliance
- Microsoft 365 Advanced eDiscovery
- Microsoft 365 Defender
- Microsoft Information Protection
- Azure Active Directory
- Microsoft Defender for Cloud
- Microsoft Sentinel Notebooks (Bring Your Own Machine Learning)
- Microsoft Defender for Endpoint
- Microsoft Defender for Identity
- Microsoft Defender for Cloud Apps
- Microsoft Defender for Office 365
Privacy is a key component of the Microsoft Sentinel Insider Risk Management Solution. This solution is based on both user trust and confidentiality for the protection of respective data. Detection algorithms are tuned to remove false positive alerts while aligning to regulatory and compliance requirements. This solution doesn't incur net-new capabilities as it leverages existing signals within the security architecture. Azure Active Director enforces strict Role-Based Access Control (RBAC) to control confidentiality, integrity, and data availability.
Benefits
- Build/design insider risk management capabilities through existing tooling
- Detect, analyze, and respond to insider risk via intuitive workflows
- Advanced correlations for AI/ML, UEBA, and geospatial location of risk-based behavior
- Privacy and regulatory compliance alignment
Audience
- Insider Risk Professionals: Risk-based behavior analysis
- Forensics Professionals: Investigations
- SecOps: Alert/Automation building
Getting Started
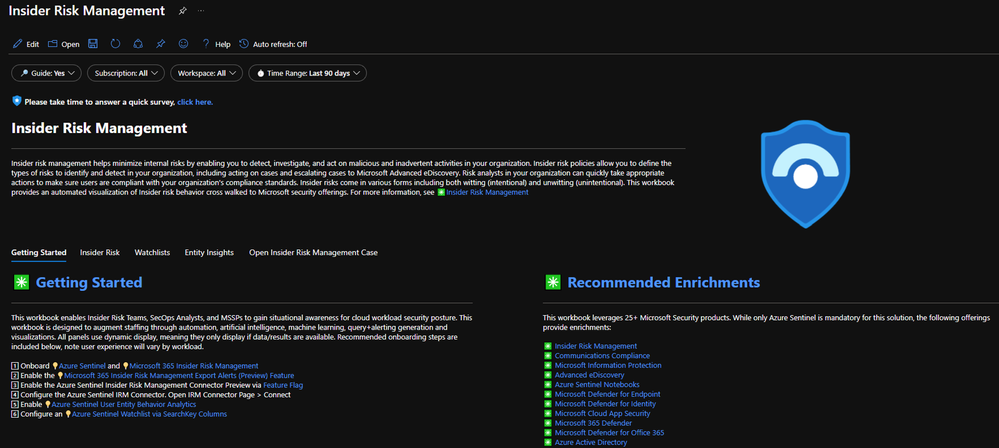
This content is designed to provide the foundation for building and operating an insider risk management program. Below are the steps to onboard required dependencies, enable connectors, review content, and provide feedback.
- Onboard Microsoft Sentinel and Microsoft 365 Insider Risk Management
- Access the Microsoft Sentinel Insider Risk Management Solution
- Microsoft Sentinel > Content Hub (Preview) > Select Microsoft Insider Risk Management Solution >Configure deployment options > create
- Enable the Microsoft 365 Insider Risk Management export alerts (preview) feature
- Enable the Microsoft Sentinel Insider Risk Management Connector
- Microsoft Sentinel > Data connectors >Search Microsoft 365 Insider Risk Management (Preview) > Open connector page > Connect
- Enable Microsoft Sentinel User Entity Behavior Analytics
- Configure an Microsoft Sentinel Watchlist via SearchKey columns
- Review the Insider Risk Management Workbook
- Microsoft Sentinel > Workbooks > Select Microsoft Insider Risk Management
- Review/Enable Analytics Rules
- Microsoft Sentinel > Analytics > Search Insider Risk Management
- Review Hunting Queries
- Microsoft Sentinel > Hunting > Queries >Search Insider Risk Management
- Review Playbook Automation
- Microsoft Sentinel > Automation > Active playbooks > Search Notify-InsiderRiskTeam > Enable
- Create Automation Rule
- Analytics > Search Insider Risk Management > Edit > Automated Response > Add new > Select Actions: Run Playbook > Select Notify-InsiderRiskTeam and configure automation options > Review > Save > Mirror configuration across all insider risk management analytics rules.
- Review the content and provide feedback through the survey
Learn More About Insider Risk Management with Microsoft Security
- Drive efficiency and accelerate time to action in managing insider risks
- Insider Risk Solutions in Microsoft 365
- Identify advanced threats with User and Entity Behavior Analytics (UEBA) in Microsoft Sentinel
Posted at https://sl.advdat.com/3c9yeMR