Yesterday we announced the public preview of a new integration between Microsoft Defender for Cloud and Azure Purview.
This unique integration extends security visibility from cloud infrastructure resources down into the data layer and enables an entirely new way to prioritize the investigation of cloud resources for security teams.
In this blog post we will recap key information about the new integration, how it can help keep your sensitive data in the cloud more secure, and how to get started.
“Azure Purview's classification of information in Defender for Cloud gives us visibility into our security posture and combined with security alerts should help mitigate and prevent any exposure or loss of sensitive data. Security recommendations help us take preventive measures on known or discovered vulnerabilities and enables us to improve our security posture and reduce our attack and data loss surface for the most valuable resources.”
– James Rajeshvincent, Head of Platform Development, Rockefeller Capital Management
An overview of Azure Purview
Azure Purview is a unified data governance service that provides rich insights into the sensitivity of your data within multi-cloud, and on-premises workloads. It helps you easily create a holistic, up-to-date map of the data landscape with automated data discovery, sensitive data classification, and end-to-end data lineage. Azure Purview can scan and classify a broad range of file and resource types including Word, PPT, and PDF documents in Azure Blob storage, SQL Servers hosted inside and outside of Azure, ADLS and AWS S3, and more.
Manage sensitive data in cloud resources with an aggregated view in Defender for Cloud
The integration with Azure Purview enriches Microsoft Defender for Cloud’s alerts, recommendations, and resources with sensitive information, giving you a high-level overview and the ability to manage resources more easily than contain sensitive data.
To make access simple and give security teams at-scale insights into the resources that are being scanned by Azure Purview, we added a dedicated Information protection tile to the Microsoft Defender for Cloud dashboard. The tile shows your current scan coverage, as well as a graph with the number of recommendations and alerts by classified resource types.
You will find Azure Purview integrated across many of the Defender for Cloud views, to make it easier for security admins to prioritize recommendations and the investigation of alerts based on the sensitivity of data within affected resources.

Enriched Cloud Security Posture Management
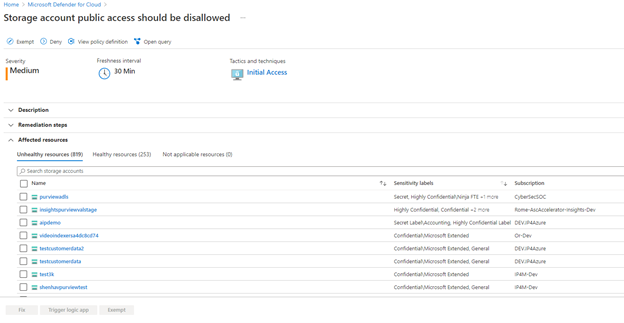
For an enriched CSPM experience, all scanned and classified resources will now show in the Inventory experience of Defender for Cloud. Here we created two new filters called Data sensitivity classification and Data sensitivity label. These new options allow security teams to filter specifically for sensitive data and provide a better understanding of their security posture. These new insights are designed to enable more targeted investigations of alerts and drive more effective prioritization and enforcement of security policies.

In addition, the Resource Health blade now provides additional metadata classification details at the resource level, giving you with an easy way to view the number of assets that contain sensitive information across your environment.
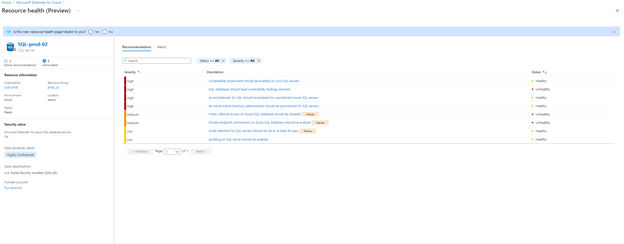
And because we know that prioritizing the remediation of recommendations can be challenging when large amounts of data resources are at play, we implemented the ability to sort resources by sensitivity label. This experience uses Azure Purview’s supported data stores and allows users to focus on remediating resources with sensitive data first.
Enriched Cloud Workload Protection
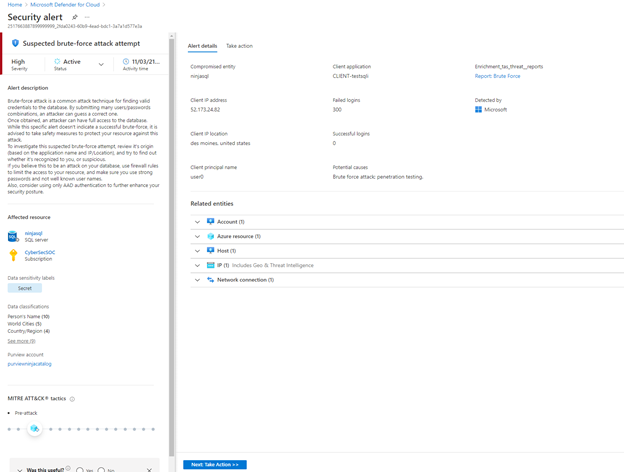
To ensure a consist experience across the different capabilities in Microsoft Defender for Cloud, we also implemented the Data sensitivity classification and Data sensitivity label filters within the Security alerts experience. These will filter alerts to only show sensitive resources, allowing for a more focused investigation.

Lastly, if you use the integration with Azure Purview, you will now find additional classification metadata information within your alerts. This provides more context to security teams including the number of assets that contain sensitive information in an affected resource, as well as information about the Azure Purview account that was used to scan the affected resource.
Get started today
Organizations using Azure Purview to classify their data resources can benefit from these capabilities automatically. If you aren’t using Azure Purview today, we encourage you to start scanning your data resources in the cloud.
- Get started using the documentation page.
- Check out the Azure Purview website.
- More Ignite news