The Microsoft Sentinel: Zero Trust (TIC3.0) Workbook was released earlier this year with an overwhelmingly positive reception from our user community. We are announcing the next evolution of this content in the Microsoft Sentinel: Zero Trust (TIC3.0) Solution. This content features a redesigned user interface, new control card layouts, dozens of new visualizations, better-together integrations with Microsoft Defender for Cloud for assessments and alerting rules to actively monitor/alert on compliance posture deviations across each TIC3.0 control family.

This solution enables governance and compliance teams to design, build, monitor, and respond to Zero Trust (TIC3.0) requirements across 25+ Microsoft products. The solution includes the new Zero Trust (TIC3.0) Workbook, (11) Analytics Rules, and (1) Playbook. While only Microsoft Sentinel is required to get started, the solution is enhanced with numerous Microsoft offerings, including, but not limited to:
- Microsoft 365 Defender
- Microsoft Information Protection
- Azure Active Directory
- Microsoft Defender for Cloud
- Microsoft Defender for Endpoint
- Microsoft Defender for Identity
- Microsoft Defender for Cloud Apps
- Microsoft Defender for Office 365
What is Zero Trust?
Zero Trust is a proactive, integrated approach to security that explicitly and continuously verifies every transaction, asserts least privilege, and relies on intelligence, advanced detection, and real-time response to threats, across all layers of the digital estate. The core to Zero Trust strategy is strict access control. This concept is critical to prevent attackers from pivoting laterally and elevating access within an environment. At Microsoft, we define Zero Trust around those three principles.
- Verify Explicitly: Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
- Use Least Privileged Access: Limit user access with just-in-time and just-enough-access (JIT/JEA), risk-based adaptive policies, and data protection to secure both data and productivity.
- Assume Breach: Minimize blast radius for breaches and prevent lateral movement by segmenting access by the network, user, devices, and app awareness. Verify all sessions are encrypted end to end. Use analytics to get visibility, drive threat detection, and improve defenses.
What is Trusted Internet Connections (TIC3.0)?
Trusted Internet Connections (TIC) is a federal cybersecurity initiative to enhance network and perimeter security across the United States federal government. The TIC initiative is a collaborative effort between the Office of Management and Budget (OMB), the Department of Homeland Security (DHS), Cybersecurity and Infrastructure Security Agency (CISA), and the General Services Administration (GSA). The TIC 3.0: Volume 3 Security Capabilities Handbook provides various security controls, applications, and best practices for risk management in federal information systems.
Content Use Cases
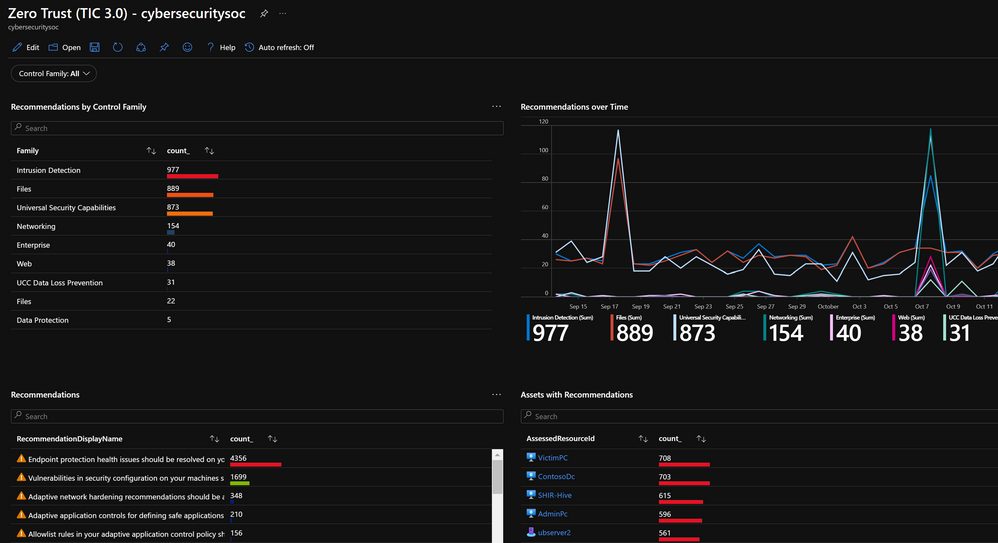
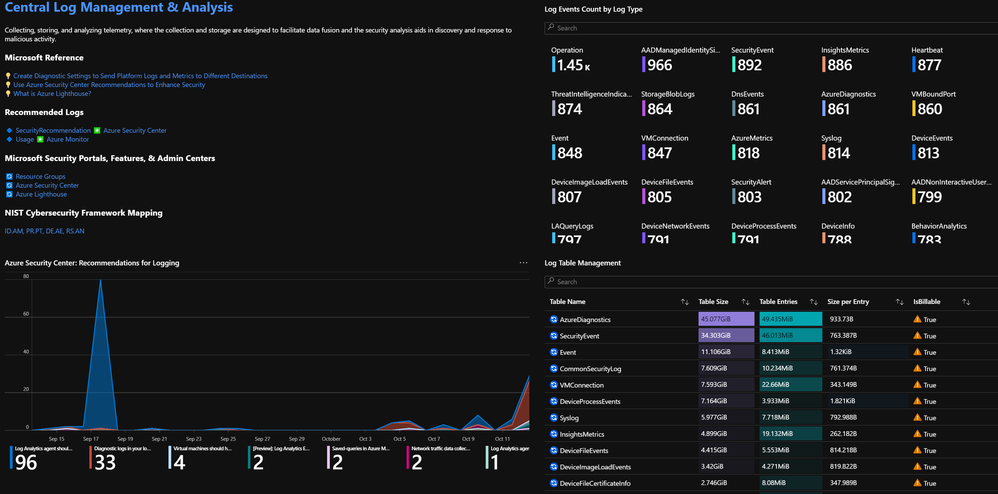
Microsoft Sentinel: Zero Trust (TIC3.0) Workbook: The Microsoft Sentinel Zero Trust (TIC3.0) workbook provides a mechanism for viewing log queries, azure resource graph, metrics, and policies aligned to Zero Trust (TIC3.0) controls across 25+ Microsoft products across Azure, Office365, Windows, and many more. This workbook enables Compliance Professionals, Security Architects, Engineers, SecOps Analysts, Managers, and IT Pros to gain situational awareness visibility for the security posture of cloud workloads. There are also recommendations for selecting, designing, deploying, and configuring Microsoft offerings for alignment with respective Zero Trust and TIC3.0 requirements.
Microsoft Sentinel: Zero Trust (TIC3.0) Analytics Rules: (11) new analytics rules aligned to actively monitoring Zero Trust (TIC3.0) posture by control family. Thresholds are customizable for alerting compliance teams to changes in posture. For example, suppose your workload's resiliency posture falls below 80% in a week. In that case, an alert is generated detailing respective policy status (passing & failing), assets identified, last assessment time, and deep links to Microsoft Defender for Cloud for remediations.
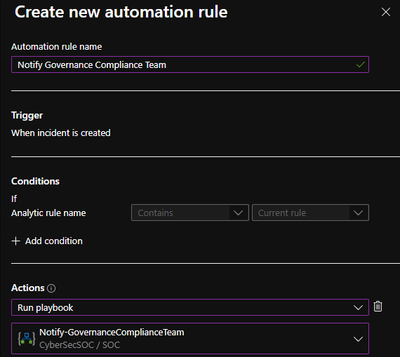
Playbook: Notify Governance Compliance Team provides the capability to automatically monitor CMMC alerts and notify the Governance Compliance team with the relevant details in both email and Microsoft Teams message.
Benefits
- Build/design workloads within Zero Trust and TIC3.0 requirements
- Customizable reporting for subscription, workspace, time, and control family.
- Redesigned Control Cards, Coverage across (11) TIC 3.0 control families
- Fully customizable panels for 3rd party product integration
- Deep links integration for seamless pivots between security products
- Compliance crosswalks to NIST CSF, configuration guidance, and alignment with Microsoft references/telemetry
- Query/Alert generation with (11) new analytics rules
Reporting
- 150+ visualizations, recommendations, queries across logs, azure resource graph, policy, metrics, and APIs
- Single-click report exports via Print Workbooks feature
- Integration with Microsoft Defender for Cloud: Regulatory Compliance Assessments
Audience
- Security Governance, Risk, Compliance Professionals: Compliance posture assessment and reporting
- Engineers/Architects: Design Zero Trust and TIC3.0 aligned workloads
- SecOps: Alert/Automation building
- Managed Security Service Providers: Consulting services
Getting Started
This content is designed to provide the foundation for designing, building, and monitoring workload compliance within Zero Trust and TIC3.0 requirements. Below are the steps to onboard required dependencies, enable connectors, review content, and provide feedback.
- Onboard Microsoft Sentinel and Microsoft Defender for Cloud
- Add the Azure Security Benchmark and NIST SP 800-53 R5 Assessments to Your Dashboard
- Continuously Export Security Center Data to Log Analytics Workspace
- Deploy the Microsoft Sentinel Zero Trust (TIC3.0) Solution
- Commercial Regions: Microsoft Sentinel > Content Hub (Preview) > Select Zero Trust (TIC3.0) Solution > Configure deployment options > Create
- Government Regions: Access Solution on Microsoft Sentinel’s GitHub Repo. Select Deploy to Azure Government Button > Configure Options > Create
- Review the Zero Trust (TIC3.0) Workbook
- Microsoft Sentinel > Workbooks > Select Zero Trust (TIC3.0)
- Review/Enable Zero Trust (TIC3.0) Analytics Rules
- Microsoft Sentinel > Analytics > Search Zero Trust (TIC3.0)
- Review Playbook Automation
- Microsoft Sentinel > Automation > Active playbooks > Search Notify-GovernanceComplianceTeam > Enable
- Create Automation Rule
- Analytics > Search Zero Trust > Edit > Automated Response > Add new > Select Actions: Run Playbook > Select Notify-GovernanceComplianceTeam and configure automation options > Review > Save > Mirror configuration across all Zero Trust (TIC3.0) analytics rules.
- Review the content and provide feedback through the survey
Frequently Asked Questions
- Are custom views and reports supported?
- Yes, via subscription, workspace, time, control family, maturity level parameters. You can select everything, specific control families, maturity level reports as needed, and export via the print/save workbooks feature.
- Are additional products required?
- Microsoft Sentinel and Microsoft Defender for Cloud are required. Each control card is based on telemetry from multiple products, including which product is leveraged and what type of telemetry is used for the visualization. 25+ Microsoft security products provide enrichment to this solution.
- Are panels with no data bad?
- No, this provides a starting point for addressing Zero Trust and TIC3.0 control requirements, including recommendations for addressing respective controls.
- Is Multi-Subscription, Multi-Cloud & Multi-Tenant supported?
- Yes, via Workbook Parameters, Azure Lighthouse, and Azure Arc
- Is 3rd Party integration supported?
- Yes, workbooks and analytics are customizable for integration with 3rd party products.
- Is this available in government regions?
- Yes, this solution is in Public Preview and deployable to Commercial/Government regions
- What rights are required to use this content?
- Microsoft Sentinel Contributor can create and edit workbooks, analytics rules, and other Microsoft Sentinel resources. Microsoft Sentinel Reader can view data, incidents, workbooks, and other Microsoft Sentinel resources.
Learn More About Zero Trust with Microsoft Security
- Introducing Microsoft Sentinel Content hub!
- Zero Trust Deployment Center
- Zero Trust: 7 Adoption Strategies from Security Leaders
- Microsoft Zero Trust Video
Posted at https://sl.advdat.com/3dstbYN