When news breaks of a major security story like the Log4j bug (CVE-2021-44228), vendors and organizations move as fast as they can to understand the issue, determine their exposure, and mitigate the risks.
The Microsoft Security Response Center was quick to release guidance and background on this issue. And we continue to update that page as we and the rest of the infosec community continue to gain a deeper understanding of the impact of this threat.
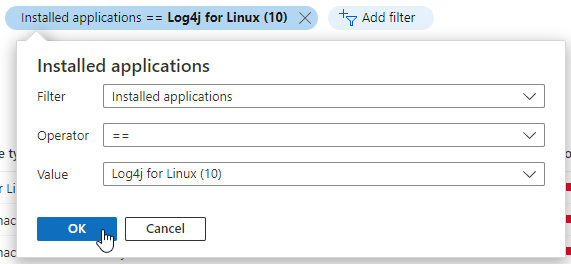
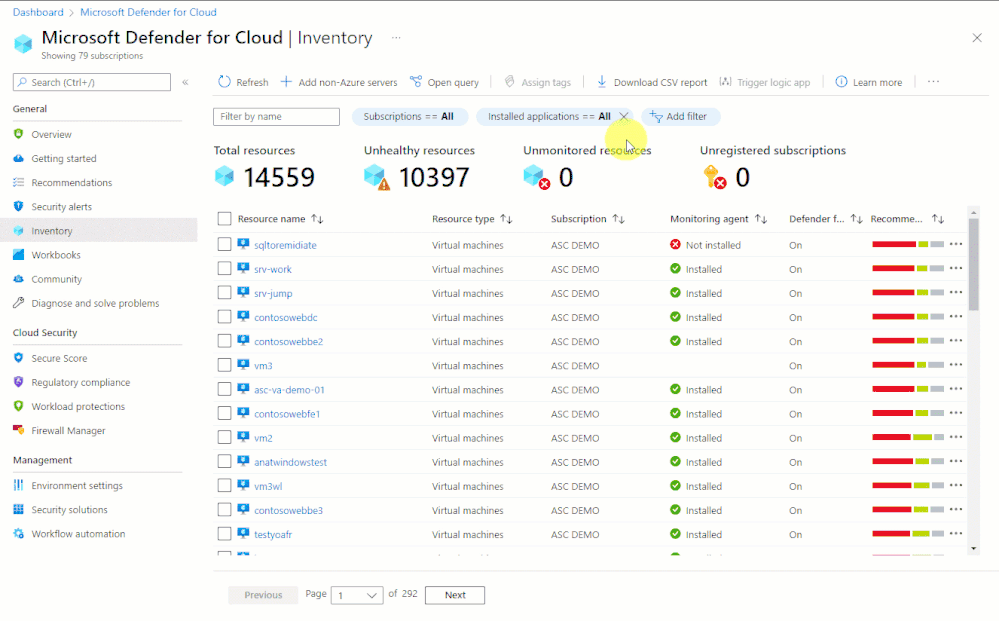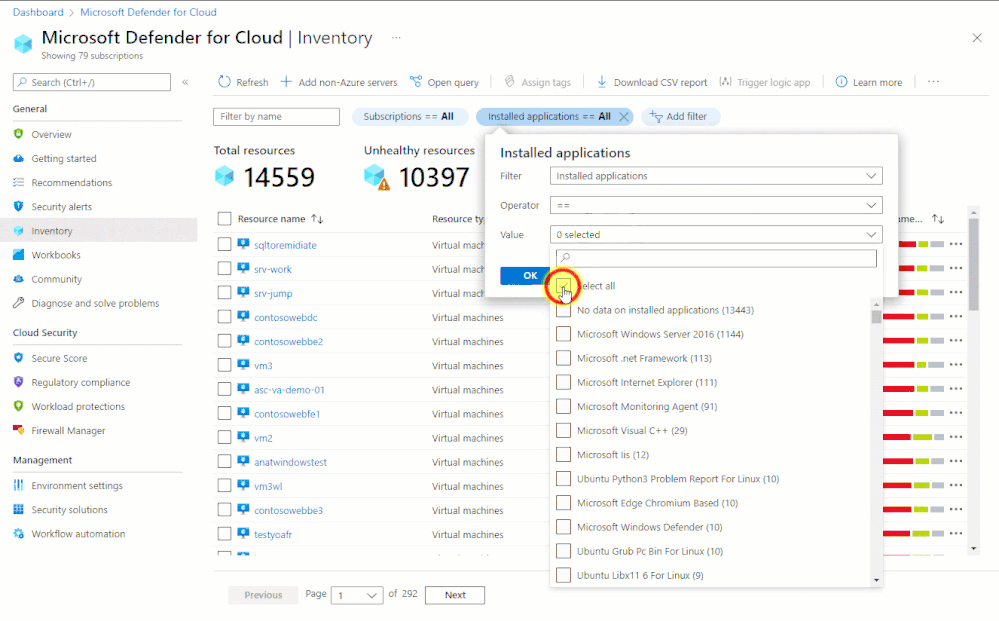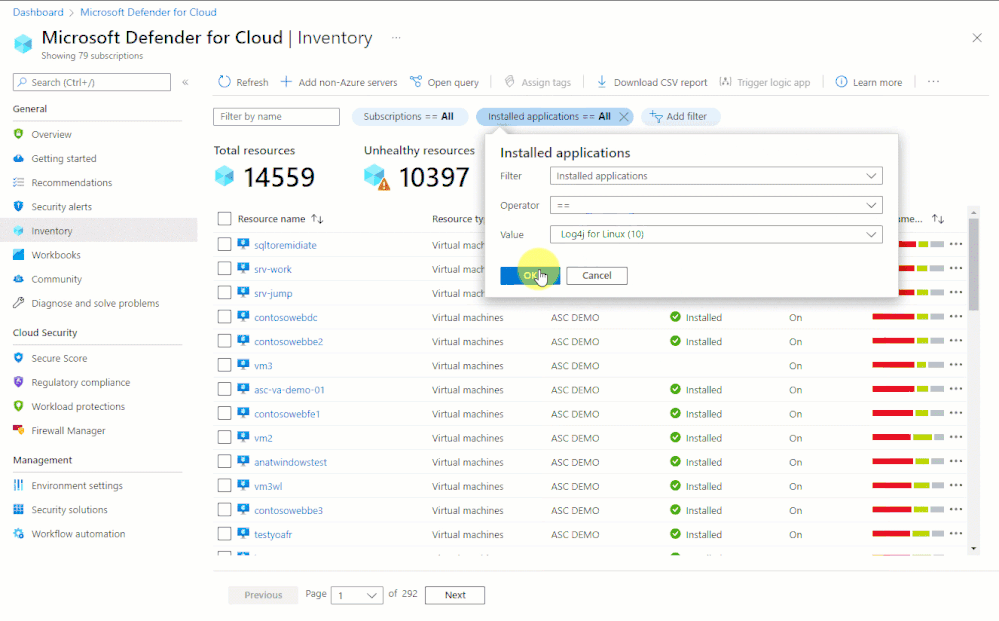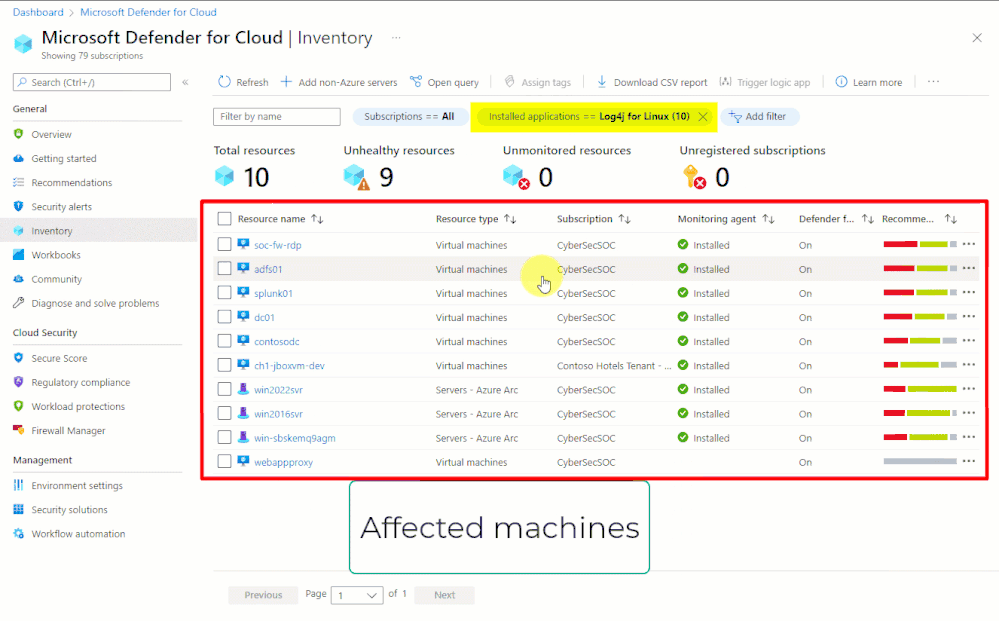
In situations like this, organizations that are using Microsoft Defender for Cloud can immediately begin investigations - even before there's a CVE number to search for - with our Inventory tools.
Using inventory, you have two powerful ways to determine your exposure:
- Software inventory - If you've enabled the integration with Microsoft Defender for Endpoint and enabled Microsoft Defender for servers, you can search your resources by installed applications:
-
Vulnerability assessment findings - If you've enabled any of the vulnerability assessment tools for your machines (whether it's Microsoft Defender for Endpoint's threat and vulnerability management module, the built-in Qualys scanner, or a bring your own license solution), you can search by a CVE identifier when it's released:
A quick demo of how you'd search for all your resources to see which ones have Log4j installed is shown below.
For extensive guidance, workarounds, background, analysis of the vulnerability, and the latest updates, check the continually maintained post on the Microsoft Security Response Center (MSRC) blog.
Posted at https://sl.advdat.com/3pVpeS4