It's a common scenario that the certificate used in Cloud Service Extended Support (CSES) is expired. To replace the original certificate, other than creating and uploading the new certificate into Key Vault, we still have multiple necessary steps to do. We can do them by multiple tools such as Azure Portal, PowerShell command and Visual Studio. In this blog, we’ll talk about how to update the necessary information by these three ways to update the certificate configuration and make it work.
Pre-requirements:
We must have a validated .pfx format certificate and upload it into a Key Vault, Certificate page.
Follow https://docs.microsoft.com/en-us/azure/cloud-services/cloud-services-certs-create#powershell to self-sign the certificate or you already have a CA certificate.
Follow step 1 to step 6 of https://docs.microsoft.com/en-us/azure/cloud-services-extended-support/certificates-and-key-vault#upload-a-certificate-to-key-vault to upload the certificate into Key Vault resource.
Then let’s talk about what we need to do for this configuration change.
By Portal:
1. In Portal, CSES page, we can find the Configuration page on the left side. And on the right side, modify the configuration file and add/modify the necessary lines (highlighted) for the certificate used. Please make sure the thumbprint here must match the real thumbprint of the certificate which we uploaded into Key Vault at first.
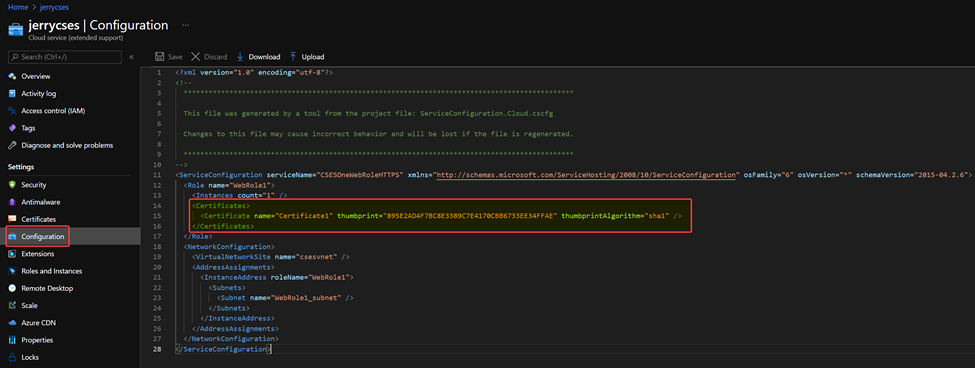
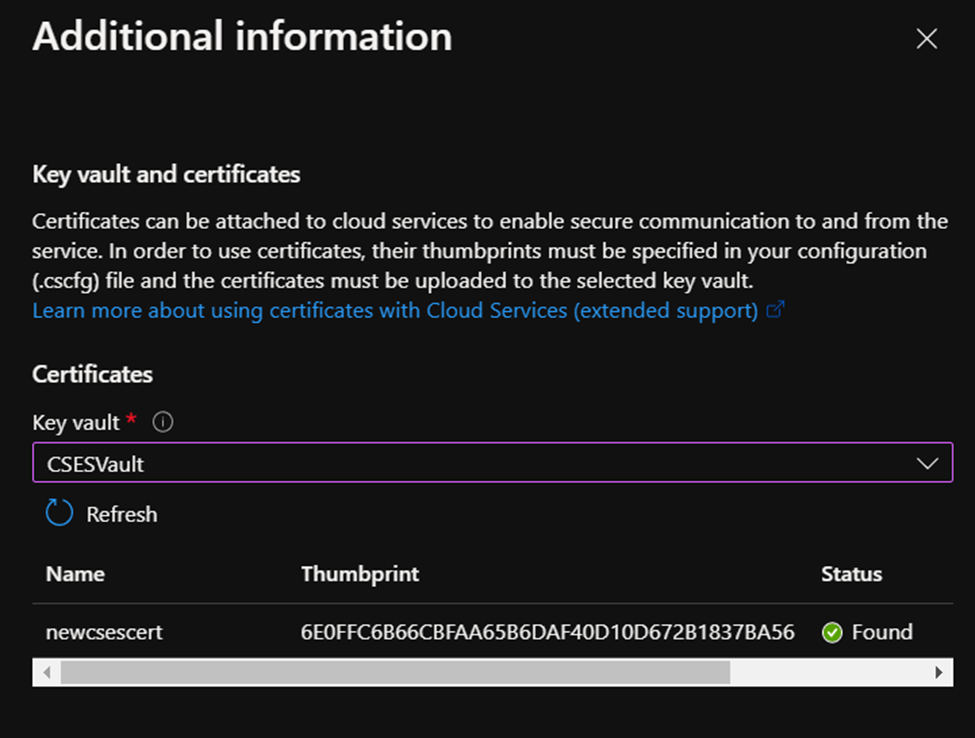
2. Once we click on Save button, there will be a new page on the right side. Select the Key Vault where we uploaded the certificate and wait for the validation turn to Found status, then click OK on the bottom side.
By Visual Studio:
1. Modify the .cscfg file and add/modify the necessary lines for the certificate used. Please make sure the thumbprint here must match the real thumbprint of the certificate which we uploaded into Key Vault in pre-requirement part. (The code change is same as Portal configuration change part, point 1. Only difference is that it’s on local .cscfg file, not in Portal.)
2. Deploy the Visual Studio CSES project again. In the deployment window, second setting page, please kindly select the correct Key Vault where we uploaded the certificate.

By PowerShell:
1. Same step as Visual Studio way.
2. Upload your .cspkg file into a storage account container, generate a SAS token and note it down. For detailed instruction, please kindly check step 7 to step 9 of https://techcommunity.microsoft.com/t5/azure-paas-blog/manual-migration-from-classic-cloud-service-to-cloud-service/ba-p/2263817.
3. Open PowerShell window and login with the account which has enough permission by command Connect-AzAccount. Then use following script to update the CSES. (Please remember to follow the table to replace the values before running the script.)
|
Variable or command name |
The expected value |
|
Cspkgurl |
The SAS token URL of .cspkg file we get from step 2 |
|
cscfgFilePath |
The local path to your .cscfg file |
|
Get-AzKeyVault |
ResourceGroupName for the name of resource group where Key Vault is deployed and VaultName for the name of Key Vault resource |
|
Get-AzKeyVaultCertificate |
VaultName for the name of Key Vault resource and Name for the name of the certificate saved in KeyVault |
|
Get-AzCloudService |
Name for the name of CSES resource, SubscriptionId for the subscription ID and ResourceGroupName for the resource group where the CSES is deployed. |
$cscfgFilePath = "C:\Users\zhangjerry\Desktop\VisualStudioproject\CSESOneWebRoleHTTPS\bin\Release\app.publish\ServiceConfiguration.Cloud.cscfg"
$keyVault = Get-AzKeyVault -ResourceGroupName CSES -VaultName CSESKVault
$certificate = Get-AzKeyVaultCertificate -VaultName CSESKVault -Name csescert
$secretGroup = New-AzCloudServiceVaultSecretGroupObject -Id $keyVault.ResourceId -CertificateUrl $certificate.SecretId
$osProfile = @{secret = @($secretGroup)}
$cses = Get-AzCloudService -Name jerrycsesps -SubscriptionId 5102f0a2-xxxx-xxxx-xxxx-2834a4473453 -ResourceGroupName CSESPS
$cses.Configuration = Get-Content $cscfgFilePath | Out-String
$cses.PackageUrl = $cspkgurl
$cses.OSProfile = $osProfile
$cses | Update-AzCloudService
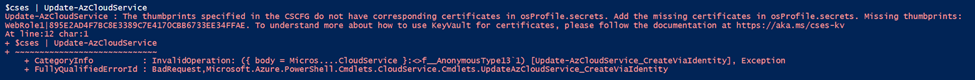
P.S. If we only update the .cscfg file of the CSES but don’t update the OSProfile of the CSES service, which means we missed the lines in red, this will cause CSES is unable to download the new cert from correct Key Vault and unable to install it into underlying instances. And it will return an error such as following:
Posted at https://sl.advdat.com/3eDmLXc