Summary
In a featured session at the Microsoft Ignite conference, Gartner® VP Katell Thielemann spoke about cyber-physical systems (CPS) and how to talk to business stakeholders about the new types of risks they pose to safety and production.1
The topic is particularly relevant now in the light of recent ransomware attacks on a gas pipeline operator and food processor, which have raised management- and board-level awareness about IoT and Operational Technology (OT) risk.
In addition to the substantial ransomware payouts ($4M and 11M, respectively), the attacks resulted in tens or hundreds of millions in lost revenue from unplanned downtime. The pipeline operator has also been hit with two class action lawsuits alleging negligence in securing their operational infrastructure.
Security and risk management (SRM) leaders are now responsible for new types of threats and risks – such as safety and production risks – from parts of the organization they never worried about in the past, when they were mainly focused on the security of information and digital assets (like databases and containers) rather than physical processes and assets (like turbines, mixing tanks, and industrial robots).
Katell is ideally suited to analyzing trends in this domain because her background includes extended stints at both General Electric and Honeywell. At the end of the blog post, we include a link to Katell’s full report, as well as a recorded interview she recently conducted with Jeffrey Wheatman, VP Advisor and Chair of the Gartner Security & Risk Management Summit.
What are Cyber-Physical Systems?
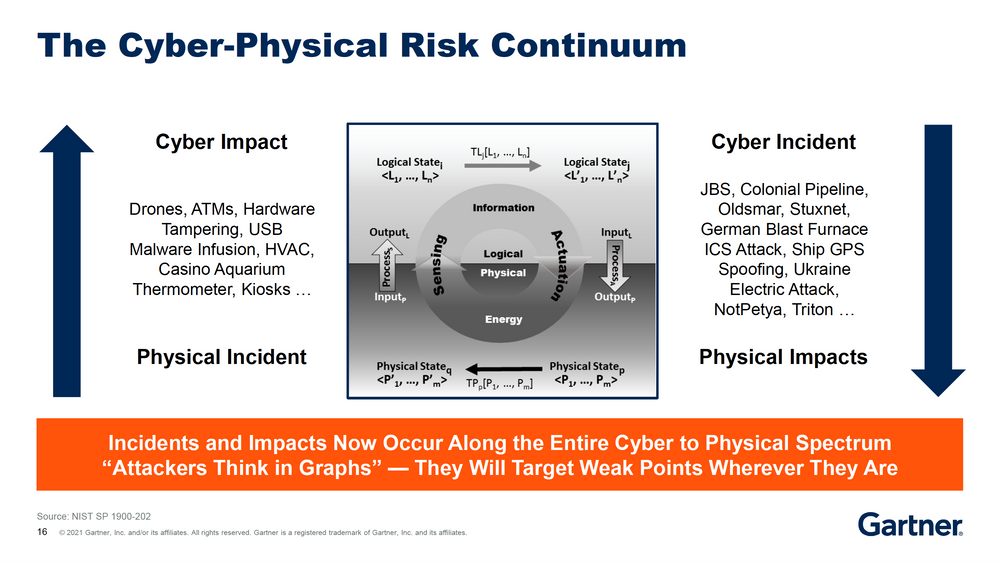
Gartner defines cyber-physical systems as “engineered systems that orchestrate sensing, computation, control, networking and analytics to interact with the physical world (including humans). They enable safe, real-time, secure, reliable, resilient and adaptable performance.2
CPS process more than information; they manage and optimize physical outcomes, from individual processes to entire ecosystems. Some examples include robotic arms, gas and oil processing technology, water purification systems, meat cutting, grain processing, baggage handling, and building management systems. Our entire civilization relies on these assets.
Gartner uses the term CPS not to replace OT and IoT, but instead to encompass the entire cyber-physical spectrum.
Why should businesses and IT security teams care about cyber-physical security? Why does it matter?
As the number of interconnected CPS increase to support digital business transformation, the attack surface and risk are also increasing.
In fact, in a recent Gartner survey, security and risk leaders ranked the Internet of Things (IoT) and cyber-physical systems as their top concerns for the next three to five years.
CPS are where the business value of an organization is created. If you’re a manufacturer, for example, value isn’t created in your payroll system, it’s created in your plants. When your plants get shut down, it directly impacts your revenue and profits. And that gets the board’s attention.
Other impacts that get the board’s attention include loss of life and environmental incidents; theft of sensitive corporate IP like proprietary formulas and manufacturing processes; and corporate liability.
What are some examples of CPS attacks?
First, let’s talk about motives: CPS largely hold your secret sauce. So, they’re going to be targeted by everyone: nation-states with geo-political, espionage and IP exfiltration motives, terrorists who may want to destabilize critical infrastructure, cybercriminal gangs who want to compel you to pay ransoms, disgruntled employees motivated by revenge or fraud, hacktivists with a political cause or societal gripe.
In addition to the recent ransomware attacks on the gas pipeline and food processor, we’ve seen the TRITON attack on the safety systems of a petrochemical company; destruction of a blast furnace in a steel plant; and the NotPetya attack which affected a global shipping and logistics firm, snack company, manufacturer of construction materials, and pharmaceutical firm (where it halted production of a critical vaccine and led to $1.3B in losses).
We’ve also seen IoT attacks on what Gartner calls “carpeted areas,” such as the nation-state attack on VoIP phones and printers discovered by Microsoft, in which attackers leveraged vulnerable IoT devices as entry points to the corporate network.
Why is this a new area for CISOs and their teams?
CISOs have traditionally been focused only on protecting the confidentiality of data in the corporate IT network.
To support business resilience and growth goals simultaneously in today’s fast-evolving environments, SRM leaders need to expand their risk lenses. They need to develop a compelling unified vision and strategy across the cyber and physical places under a cyber-physical system security (CPS-Sec) umbrella.
What are some best practices for developing a CPS vision statement? How do you make this real for senior management and the board?
To get past “data breach fatigue” that boards may be experiencing, highlight the real-world impacts of recent attacks, such as gas stations running out of fuel up and down the US east coast.
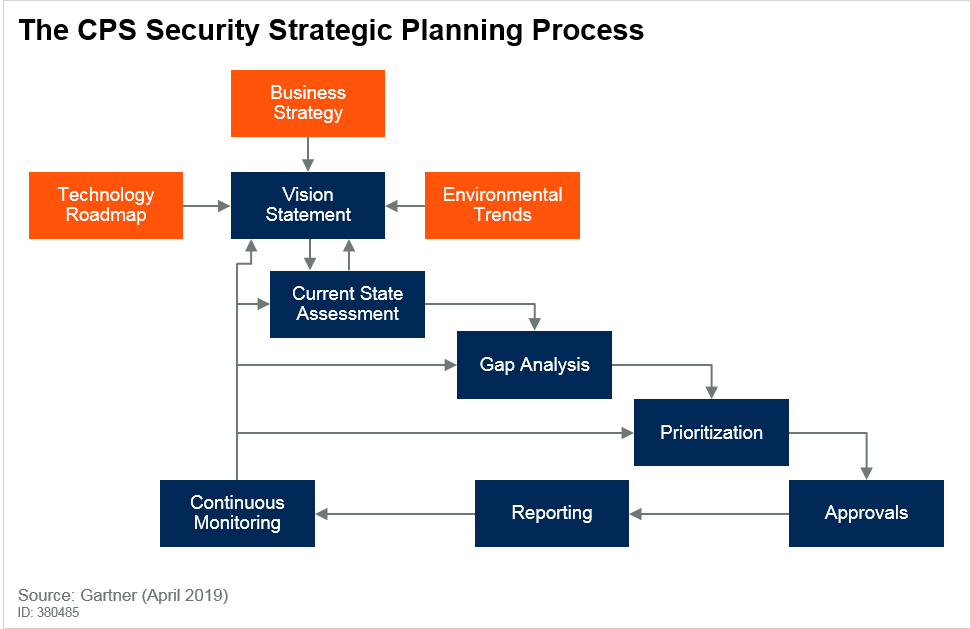
Gartner recommends the following approach when developing a CPS vision statement3:
“Start by documenting your organization’s business strategy, and enumerating the technology drivers and environmental trends that are unique to your enterprise. This will lay the foundation for articulating a clear vision statement, and will act as an anchoring document for the other steps.
The vision statement needs to be presented using voice-of-the-business language to resonate. Too often, SRM leaders are pigeon-holed into an alarmist, an obstructionist or a last-line-of-defense position. Communicating risks in the context of business or mission outcomes helps shift these perceptions.
Good vision statements share several characteristics:
- They are concise: a maximum of 40 words.
- They are clear: they do not require someone to interpret and are free of jargon.
- They are relevant: directly linked to the enterprise vision statement.
- They are goal-oriented: what will be achieved.
Characteristics of CPS security that should be woven in as appropriate:
- It enables assured and trusted environments, processes, data and outcomes.
- It protects specific organizational assets: people, property, operations, information and environments.
- It prioritizes safety, availability, security, reliability, resilience, adaptability and privacy.
- It cuts across organizational silos.
- It relies on skillsets that bridge IT, operations, engineering, facilities, health and safety, or supply chain disciplines.
Examples of CPS-oriented SRM vision statements in business and mission contexts include:
- For a Public Utility: “We will enable delivery of reliable, economical and high-quality electricity services by ensuring safe, resilient, compliant and secure operations from our processing facilities and transmission infrastructure all the way to our client interactions.”
- For a Manufacturing Organization: “We will directly support Company Inc.’s revenue and profit goals by ensuring that safe, high-quality, trustworthy and secure materials, processes and data are assured from the supply chain to client delivery.”
- For a University Campus: “We will work relentlessly with our facilities, administrative and public safety partners to create a safe and secure campus environment where our students, faculty and staff can learn, share and create.”
- For a Defense Maintenance Squadron: “We will directly support the Department of Defense’s efforts to deter war and protect the security of our nation by ensuring the security and safety of all weapons systems and assets from theater to depots.”
What are the seven steps for developing a CPS vision and strategy?
- Vision Statement – Important to be business centric, not security geek speak.
- Current State Assessment – It means going out of traditional comfort zones and reaching out to operations, engineering, maintenance, facilities, supply chain or product managers — talking to anyone who may manage or develop CPS. Getting out of your IT office and getting a clear picture of the security situation out there.
- Gap Analysis – This is where we see the shock register for most. Networks are flat, open ports are everywhere, ancient unsupported operating systems, shared passwords as shift personnel change, OT equipment suppliers and contractors remoting in, no skilled security personnel – you name it. It’s not a pretty picture out there.
- Prioritization – you can’t tackle it all. Figure out what your CPS crown jewels are and start there with a hybrid IT and CPS security approach that enhances security without hindering operations.
- Approvals – because this will take investments in both people and budgets. The legacy technical debt is tremendous.
- Reporting – Increasingly important, and not just internally. We could spend another session just like this one talking about the new regulations and directives rapidly emerging, particularly when it comes to critical infrastructure.
- Continuous Monitoring – Because the CPS landscape changes constantly. continuous monitoring is about tracking the execution of the strategy (the roadmap/projects), as well as the changes in the business, technology and environmental drivers, and refining/adapting the strategy, if required.
What are some of the technologies required to reduce CPS risk?
Too many organizations still think that “security by obscurity” is OK, or they can simply deploy a few firewalls and network segmentation.
While segmentation is an important control because it makes it more difficult for attackers to move laterally, we also recommend the following technologies at a minimum:
- Asset discovery, asset inventory, network topology mapping
- Vulnerability management
- Continuous monitoring with anomaly detection is also available with some platforms
- Analytics, AI, automation and orchestration in the SOC, integrated with IT security tools like SIEM and XDR
How do you see these technologies evolving?
What is needed moving forward are CPS Protection Platforms, that bring an asset-centric view of security and tackle issues such as:
- Baselining and configuration management
- Secure communications whether the CPS use a network, Wi-Fi, GPS, upcoming 5G..
- Risk scoring, prioritization and modeling
- Privilege access management
- Ports and removable media management
- Incident response management and automated playbooks
- Supplier software and hardware assurance – supply chain security concerns are HUGE in CPS
- Executive and regulatory compliance reporting
Graphics in this blog post were published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from here.
Gartner does not endorse any vendor, product or service depicted in its research publications and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Learn more about CPS security
- Gartner report on “How to Develop a Security Vision and Strategy for Cyber-Physical Systems”4
- Interview with Katell Thielemann conducted by Jeffrey Wheatman, VP Advisor and Chair of the Gartner Security & Risk Management Summit.
- Smarter with Gartner: Develop a Security Strategy for Cyber-Physical Systems, April 13, 2021
Microsoft's agentless IoT/OT asset discovery and security monitoring
- Microsoft Defender for IoT product summary
- Enabling IoT/OT threat monitoring in your SOC with Microsoft Sentinel
- Ninja technical training
- Microsoft achieves #1 score for threat coverage visibility in MITRE ATT&CK for ICS evaluation
- How a global manufacturing company secured production and bridged the IT/OT gap
- How a smart building company proactively secures its operational networks
Compare to your peers
1 Microsoft Ignite Session featuring Katell Thielemann on Cyber-Physical Systems (November 3, 2021)
2,3,4 Gartner, How to Develop a Security Vision and Strategy for Cyber-Physical Systems, Katell Thielemann, Refreshed 1 September 2020, Published 4 April 2019.
Posted at https://sl.advdat.com/33bKT0N