By Lothar Zeitler – Senior Program Manager | Microsoft Endpoint Manager – Intune
The pandemic rapidly evolved the way we work, and as more people work from home, IT administrators need to manage their devices remotely. According to the Microsoft Work Trend Index, in 2021, 46% of the workforce plan to work remotely (source: Work Trend Index: Microsoft's latest research on the ways we work).
A central method to increase security on your physical Windows devices is to configure Unified Extensible Firmware Interface (UEFI) settings. This article will guide you through the process of configuring Microsoft Intune to manage UEFI settings for Microsoft Surface Devices. We will use the Microsoft open-source project, Project Mu - Device Firmware Configuration Interface (DFCI).
About DFCI
Microsoft leverages DFCI to provide automated UEFI settings with Microsoft Endpoint Manager. While traditional UEFI implementations require physical configuration, DFCI securely enables zero-touch remote configuration of these settings and is built on Intune and authorized by Windows Autopilot. DFCI provides a straightforward way to easily configure hardware settings, such as disabling cameras and microphones, or disabling boot to USB on Surface devices. These settings cannot be bypassed by a physical attacker or from the Operating System-level because the checks happen even before the system boots an OS.
DFCI and Windows Autopilot
To use DFCI, the device needs to be registered with Windows Autopilot by an OEM or a Microsoft Cloud Service Provider (CSP) and managed by Intune. Self-registered devices are not trusted for the purpose of DFCI management. See Windows Autopilot registration overview and Configure Autopilot profiles for more information.
Supported OEM and devices
Currently, Microsoft Surface devices are the only devices that support DFCI configuration with Intune. Note that older Surface devices do not support DFCI either. For a list of the specific Surface devices that support DFCI, see Manage DFCI on Surface devices.
DFCI integration flow
Let's look at the process of DFCI integration.
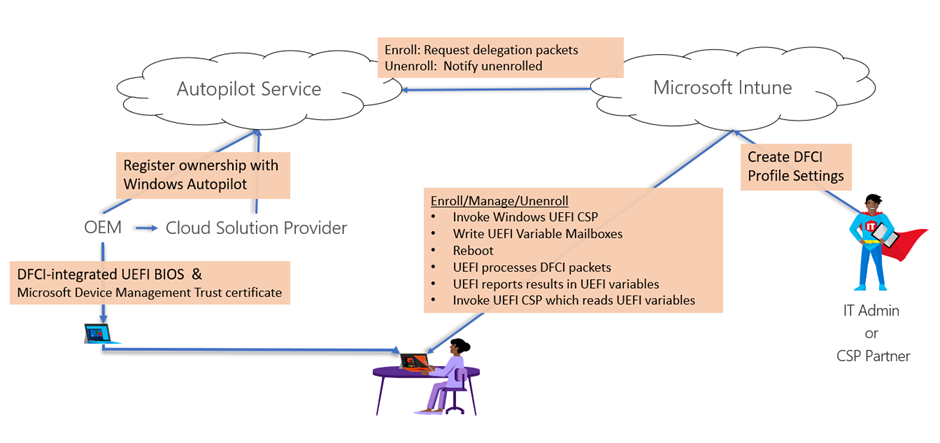
First, the PC UEFI (BIOS) integrates the DFCI code and includes the Device Management Trust certificate. The second step ensures that the device ownership is registered in Windows Autopilot by an OEM or CSP. Only trusted devices can be configured; this is essential to ensure that no one can take a device hash and perform setting changes. In the third step, the IT Admin creates a DFCI policy in addition to the enrollment profile and additional policies as needed. Fourth, we enroll the device with Autopilot in our corporate environment. The policies will get applied, and the UEFI-related settings will be written to the UEFI mailboxes. The device will reboot and process the packages and report the status back (for example, USB port disabled).
More details can be found on: Scenarios – Project Mu (microsoft.github.io).
DFCI Settings Removal and Recovery
There are several scenarios that we need to consider in planning when we are thinking about the device lifecycle. While enrollment sets the DFCI policies for the device, we also need to consider reuse, reinstall and retirement of the device.
Reuse
If you plan to reuse a device, do not remove the Autopilot record from Intune. After you wipe the device, make sure that the device is a member of the group that is assigned the new DFCI and Autopilot profiles.
Retire
When you're ready to retire the device and release it from management, update the DFCI profile to the UEFI (BIOS) settings you want at the exit state. Ensure that the DFCI configuration profiles settings for this specific device are set to Not configured and the policies will be applied before you retire the device. This will unlock the devices’ UEFI (BIOS) menus. Once you wipe the device, you can delete the Autopilot record.
Recover
If you wipe a device and delete the Autopilot record before unlocking the UEFI (BIOS) menus, all the device’s UEFI settings will remain locked and Intune can’t send profile updates to unlock it.

To unlock these settings, you need to request the unenroll packages via the web. These packages will allow you to reset the UEFI configuration settings. Recovery unlocks the menus but leaves all UEFI (BIOS) settings set to the values in the previous Intune DFCI profile.
Start the machine into the UEFI (BIOS) setup and make sure that you have a supported ethernet adapter available (i.e., Surface Ethernet Adapter). You need to download the unenroll packages over wired internet; Wi-Fi will not work for the UEFI (BIOS) settings. In the Surface UEFI settings, choose Management > Configure > Refresh from network > Opt Out and then restart the device.

For more information, see Update Windows BIOS features using MDM policies in Microsoft Intune and Removing DFCI management.
Configuring DFCI settings in Intune
This section explains how to configure DFCI settings for a Surface device in Intune. For this example, I'll use a Surface Laptop 3.
Note: Before you can deploy DFCI settings, the device must be registered with Windows Autopilot by a CSP or OEM and enrolled in Intune. Autopilot self-registration is not supported with DFCI configuration.
First, I will create a new static group that includes computers that will receive DFCI configurations. In the Microsoft Endpoint Manager admin center, I create a new group.

In the New group dialog, leave the default group type Security and specify a group name. I name my example group "W_Surface_UEFI_Protected" and leave the membership type Assigned. Then I select No Members Selected to manually add devices.
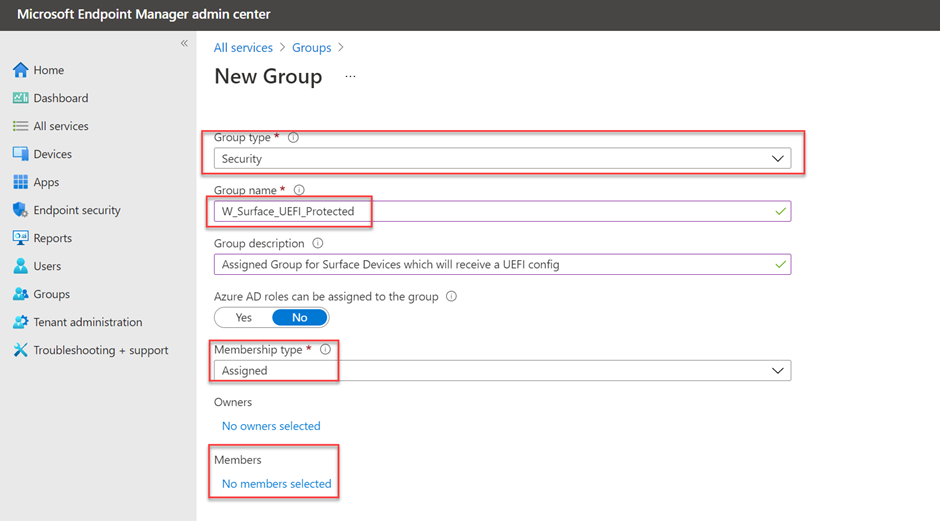
For this example, I select "LOZTECH-1483", which is my Surface Laptop 3 Test device, and then select Create to create the group.
The group will show up after a minute with the device as a member. Now, we can create the DFCI policy.
To create the configuration profile, select Devices > Configuration profiles, and then select Create profile. In the Create a profile section, choose Windows 10 and later as the platform and Templates as the profile type, and select Device Firmware Configuration Interface.

In Create profile, add a name and an optional description, and Select Next. I use "W_Surface_UEFI_Settings" for my example.

In Configuration settings, you'll find all the settings that are available in the UEFI configuration.
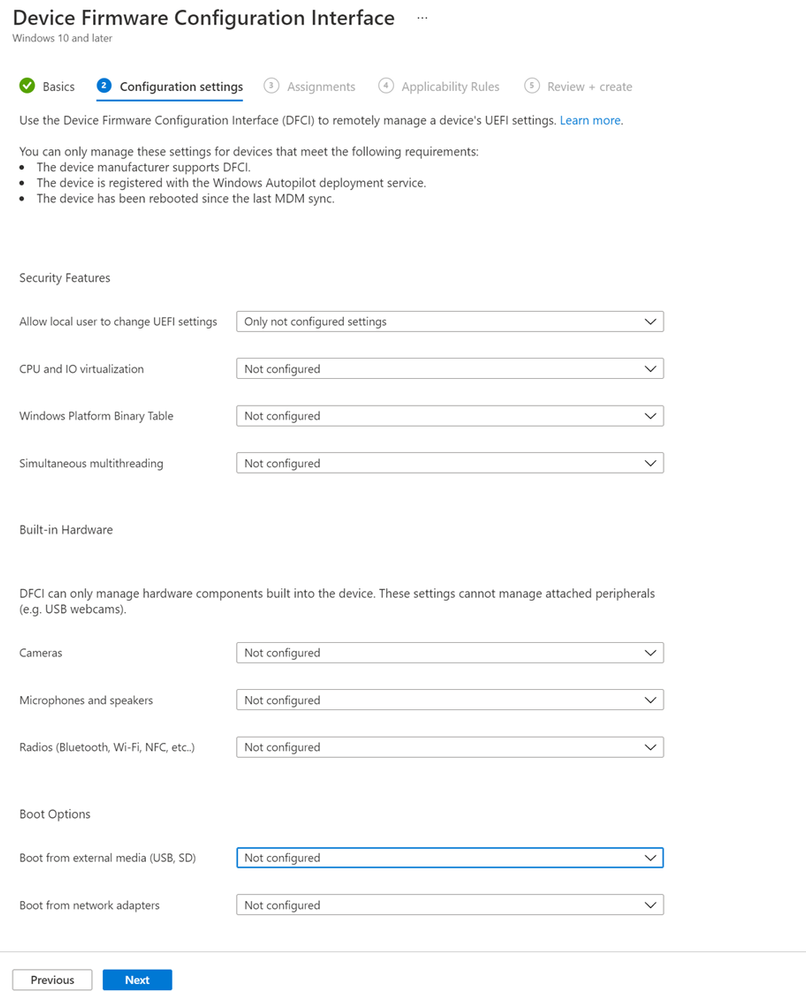
In our example configuration, we'll modify only one setting. For our example, we want to allow the user to change unconfigured settings when entering the UEFI settings on the machine. So, we leave Allow local user to change UEFI settings to its default value (Only not configured settings).
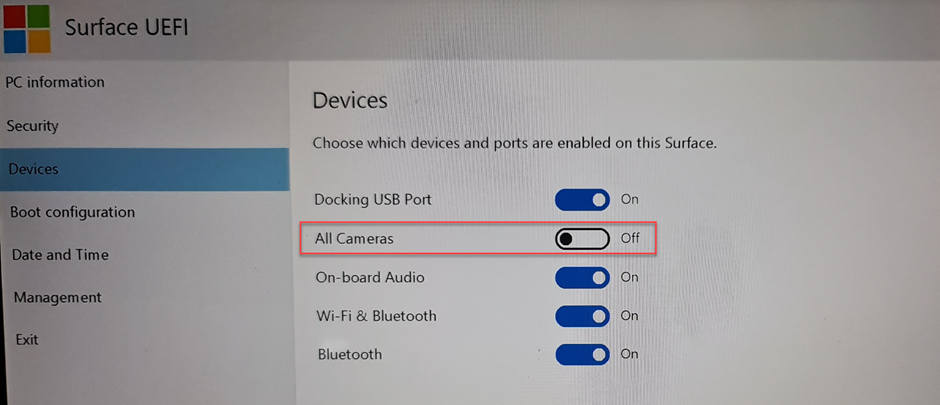
For our example, we want to disable all built-in cameras. To do this, we change the Cameras setting to Disabled.
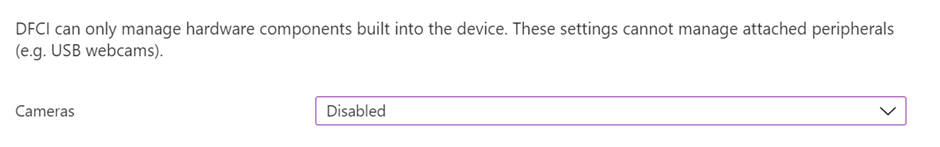
Select Next to continue. In the Assignments section, we add the group we created earlier, "W_Surface_UEFI_Protected".
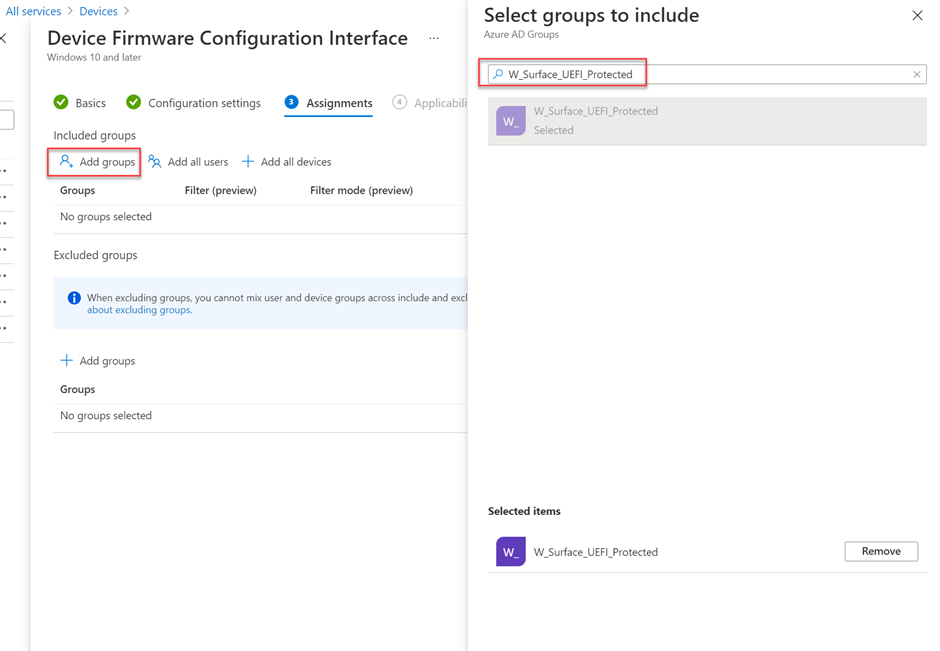
Select Next to continue through Applicability Rules, and then review the group settings and select Create.
Let's take a quick look at the local UEFI setting before the policy is assigned.
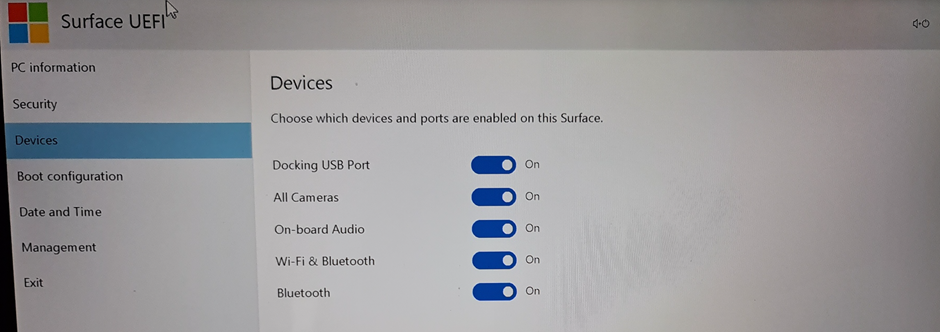
When the settings are applied to the device, the user will no longer be able to turn on the device cameras. The UEFI menu also shows the statement “Some settings are managed by your organization.” All other settings, as we specified, can still be configured by the user.

To confirm whether the policy has been correctly applied, you can check on the device and also in Intune.
On the Intune side, in the Microsoft Endpoint Manager admin center, go to Devices, select the device, and then select Device Configuration and the DFCI profile we created (for our example, "W_Surface_UEFI_Settings"). If a setting was successfully applied, you will see it in the details.
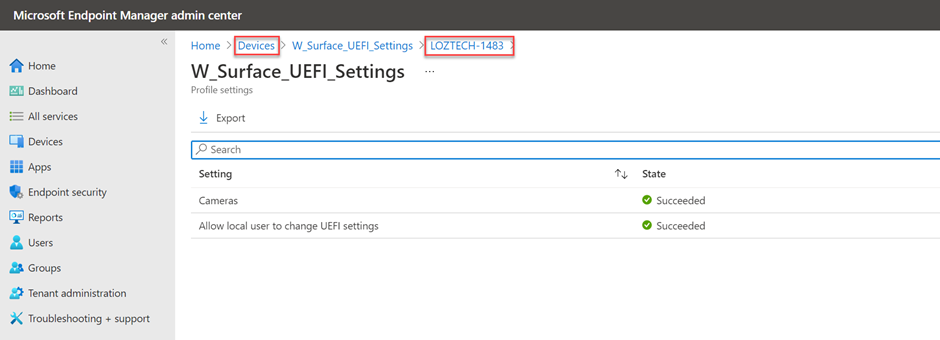
To remove a setting configuration (the organization will no longer manage that UEFI setting), reset it in the Intune device profile to Not configured. The setting will return to the last value from the profile (in this example, All Cameras returns to Off) and the user can now configure the setting.
Now that you have a better understanding of enabling UEFI configuration with Microsoft Surface devices in Intune, you can help your company take advantage of this technology. If you have any questions, reply to this post or reach out to @IntuneSuppTeam on Twitter.
Posted at https://sl.advdat.com/3qHJx5Y