By Erin Boris, Idan Basre and Yoann Mallet
One of the latest app connectors to be added to Microsoft Defender for Cloud Apps is for Smartsheet.
As we have in the past for other protected apps, we would like to share a few examples of how to use it to secure your Smartsheet deployment.
Why Connect Smartsheet?
As with other apps, connecting Smartsheet to Defender for Cloud Apps allows you to leverage some of the built-in features of your favorite CASB, such as:
|
Benefit |
Description |
Policy or template |
|
Threat and Anomaly Detection |
Detect cloud threats, compromised accounts, and malicious insiders |
The following built-in Threat detection policies automatically apply when Defender for Cloud Apps is connected to Smartsheet: · Unusual file share activities · Unusual file deletion activities · Unusual administrative activities · Unusual multiple file download activities
|
|
Audit, investigation, and hunting |
Use the audit trail of activities for forensic investigations |
Leverage Advanced Hunting Queries as part of the Microsoft 365 Defender Portal to audit the use of Smartsheet and create policies |
How to connect Smartsheet?
Let’s start with connecting Smartsheet.
Detailed instructions are available here, and if you prefer our video, check it out below:
Leverage Microsoft Defender for Cloud Apps with Smartsheet
The best way to get quick value from Defender for Cloud Apps when protecting Smartsheet, is to use the Advanced Hunting feature in the Microsoft 365 Defender portal.
If you have not used that portal just yet, simply visit http://security.microsoft.com and you will be redirected to it.
Once there browse to advanced hunting. This will enable you to write your own KQL queries to gather relevant information from the Defender for Cloud Apps activity logs.
Here are two relevant examples:
Scenario 1: New user invited, has an external email address
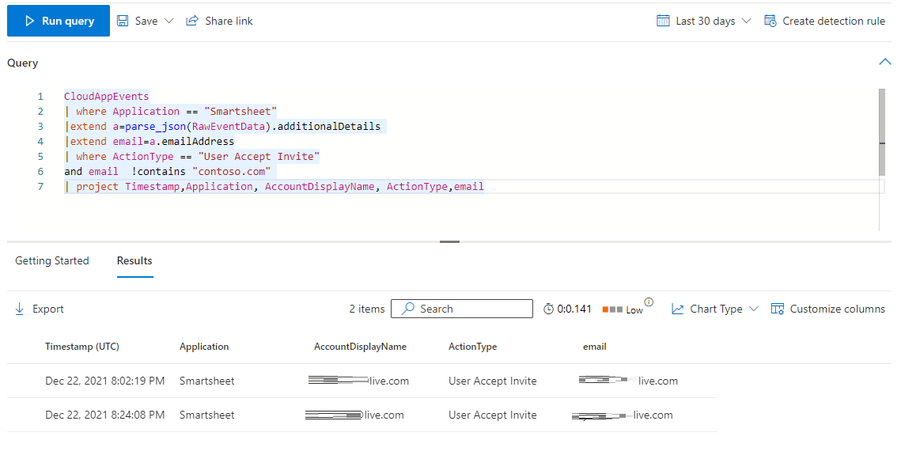
Having a new user invited to Smartsheet with an external email address may be suspicious. In order to detect this, you can leverage the following KQL Query:
CloudAppEvents
| where Application == "Smartsheet"
|extend a=parse_json(RawEventData).additionalDetails
|extend email=a.emailAddress
| where ActionType == "User Accept Invite"
and email !contains "contoso.com"
| project Timestamp,Application, AccountDisplayName, ActionType,email
Below is an example of the result of that query in Advanced Hunting:
This can potentially help you detect any attempt to exfiltrate data or identify a malicious user enabling an external account.
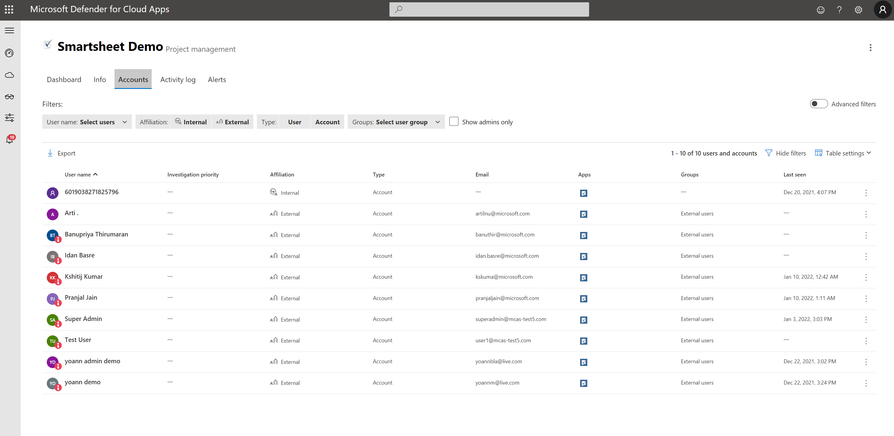
Another option to view all accounts with external email addresses that currently have access to Smartsheet, is from the API connector properties in Defender for Cloud Apps.
A filter can be used to see all external accounts that have accepted an invitation.
Scenario 2: File sent as attachment to external email address
When files are sent as an attachment from Smartsheet directly, to an external email address, this can be a sign of data exfiltration.
In order to identify such activities, you can leverage the following KQL Query:
CloudAppEvents
| where Application == "Smartsheet"
|extend a=parse_json(RawEventData).additionalDetails
|extend Recipient=a.recipientEmail
| where ActionType =="Sheet Send As Attachment"
and Recipient !contains "contoso.com"
| project Timestamp,Application, AccountDisplayName, ActionType,Recipient
Creating alerts from these queries
In addition to detecting these actions, Microsoft 365 Defender also allows you to create your own custom detections, and identify when these occur in near real-time, as described here.
As you can imagine, when using such powerful queries, the sky is the limit! Feel free to share any relevant KQL query you have identified for Smartsheet in the comments below.
Resources:
For more information about the features discussed in this article, please read:
- Advanced hunting overview
- Advanced hunting best practices
- Cloud App Security anomaly detection alerts investigation guide
- Microsoft 365 Defender Github
Feedback
We welcome your feedback or relevant use cases and requirements for this pillar of Cloud App Security by emailing CASFeedback@microsoft.com and mentioning the area or pillar in Cloud App Security you wish to discuss.
Learn more
For further information on how your organization can benefit from Microsoft Cloud App Security, connect with us at the links below:
|
Join the conversation on Tech Community. Stay up to date—subscribe to our blog. |
Upload a log file from your network firewall or enable logging via Microsoft Defender for Endpoint to discover Shadow IT in your network. |
|
Learn more—download Top 20 use cases for CASB. |
Connect your cloud apps to detect suspicious user activity and exposed sensitive data. |
|
Search documentation on Microsoft Cloud App Security. |
Enable out-of-the-box anomaly detection policies and start detecting cloud threats in your environment. |
|
Understand your licensing options. |
Continue with more advanced use cases across information protection, compliance, and more. |
|
Follow the Microsoft Cloud App Security Ninja blog and learn about Ninja Training. Read up on recent blogs: aka.ms/MCASMarch2021 Go deeper with these interactive guides: · Discover and manage cloud app usage with Microsoft Cloud App Security · Protect and control information with Microsoft Cloud App Security · Detect threats and manage alerts with Microsoft Cloud App Security · Automate alerts management with Microsoft Power Automate and Cloud App Security |
|
Posted at https://sl.advdat.com/3FgiwMl