Last July we announced the acquisition of CloudKnox Security, a leader in Cloud Infrastructure Entitlement Management (CIEM). As an important move in our multicloud security vision, we have made tremendous progress integrating CloudKnox into our technology stack. Today, I’m excited to announce the public preview of CloudKnox Permissions Management, a unified CIEM solution that manages permissions of any identity across any cloud.
As I’m sure you’ve experienced, the explosion of identities and permissions across clouds has created new security challenges. IT teams lack visibility into identities and their permissions and struggle with ever increasing permission creep. These challenges require a comprehensive, unified solution for full visibility and risk remediation.
Here is a rundown of how CloudKnox Permissions Management continuously monitors and remediates your permission risks to secure your critical cloud resources:
Get a comprehensive view of your permission risk
CloudKnox Permissions Management offers detailed visibility into all identities and their permissions granted and permissions used, across your cloud infrastructure, so you can uncover any action performed by any identity on any resource. This is not limited to just user identities, but also includes workload identities such as virtual machines, access keys, containers, and scripts, across the three key cloud providers – Amazon Web Services (AWS), Google Cloud Platform (GCP), and Microsoft Azure. The dashboard gives you an overview of your organization’s permission profile to locate where the riskiest identities and resources are across your infrastructure. It leverages the Permission Creep Index, which is a single metric ranging from zero to 100 that calculates the gap between permissions granted and permissions used. The more unused actions and untouched resources, the higher the gap and the index.
You can easily pinpoint specific identities with a high Permission Creep Index and look at what permissions they are granted versus what they used, and what resources they can get to. This level of visibility is needed to identify where the highest risks are and remediate them.
Automate least privilege access
Once you identify the most critical permission risks across your infrastructure, CloudKnox Permissions Management allows you to right-size excessive permissions and automate least privilege policy enforcement. The solution continuously analyzes historical permission usage data for each identity and you can right-size permissions of that identity to only the permissions that are being used for day-to-day operations. All unused and other risky permissions can also be removed.
For any break glass or one-off scenarios where an identity needs to perform a certain set of actions on a set of specific resources, the identity can request those permissions on-demand for a limited period with a self-service workflow. You can use the built-in workflow engine or your favorite ITSM tool. The user experience is the same for any identity type (human or non-human), identity source (local, enterprise directory, or federated), and any cloud.
Streamline anomaly detection to accelerate incident response
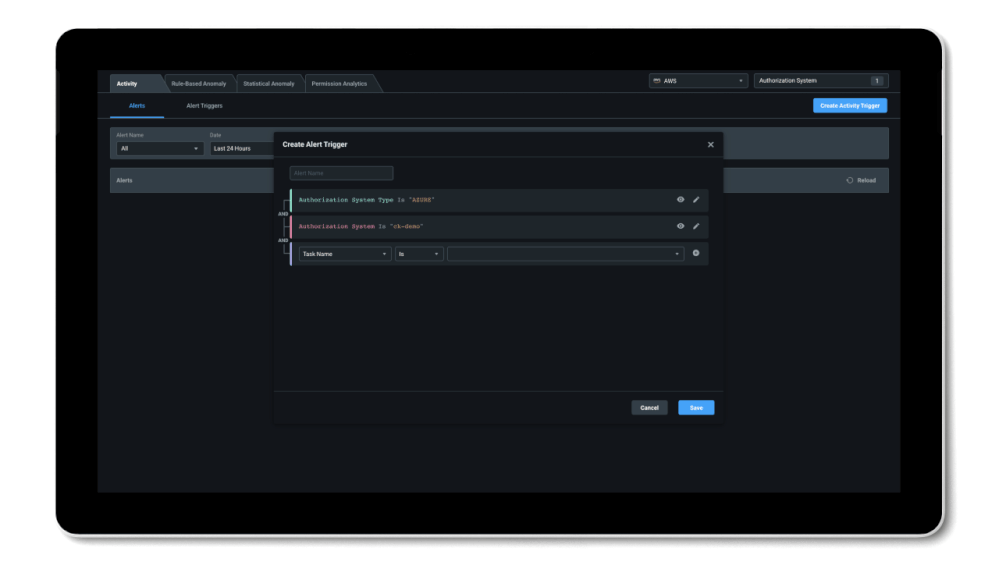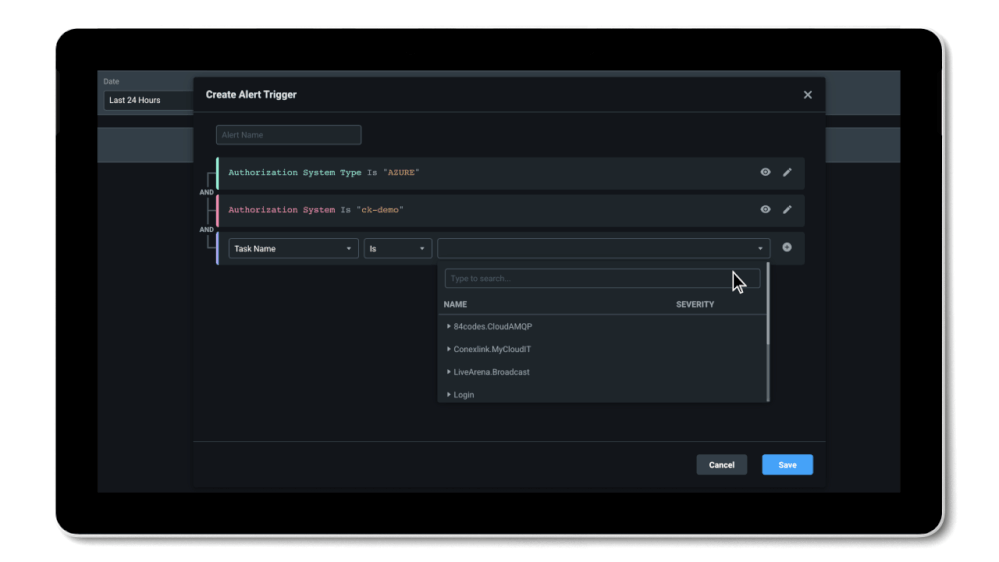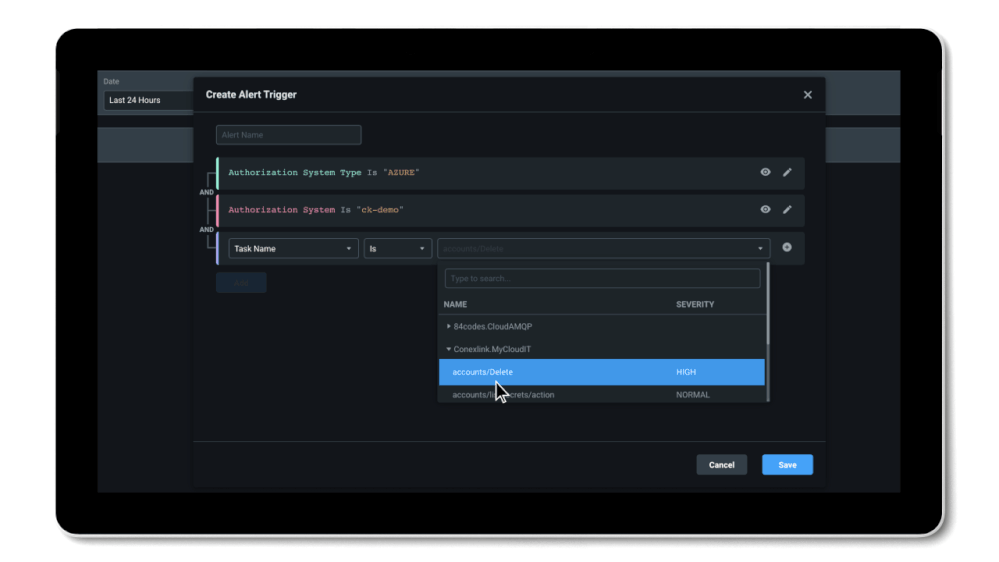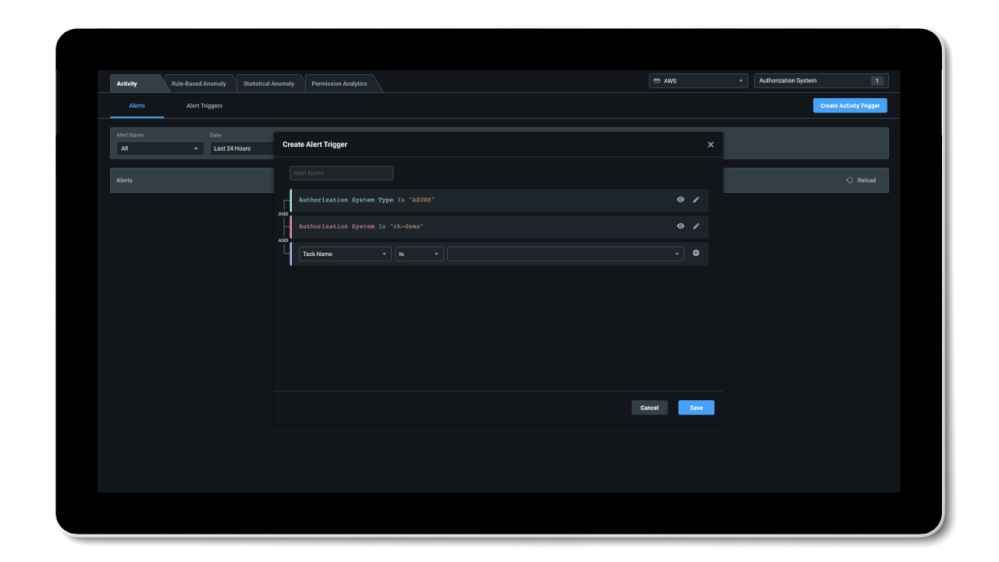
To prevent privilege misuse and a potential data breach, machine learning-powered anomaly and outlier detection alerts will notify you in case of suspicious activity. You can also set up custom alert triggers for a specific set of actions or resources or any combination to automate your monitoring and perform incident response.
Another way you can monitor your infrastructure to support rapid remediation is by generating custom forensic reports. For example, the Permissions Analytics Report will generate a summary of key permission risks across your cloud environments. These reports can be customized to a target set of cloud accounts and delivered via email at pre-configured intervals.
We’d love to have you try out CloudKnox Permissions Management. If you have any questions or are interested in joining our Public Preview, please fill out this form. If you’d like to learn more, don’t miss Balaji Parimi and Joseph Dadzie’s speaking session with one of our customers at the “What’s Next in Security” event on February 24th.
Best regards,
Alex Simons (Twitter: @Alex_A_Simons)
Corporate Vice President
Microsoft Identity and Network Access Division
Learn more about Microsoft identity:
- Related Articles: Microsoft Security delivers new multi-cloud capabilities / CloudKnox Permissions Management Documentation
- Return to the Azure Active Directory Identity blog home
- Join the conversation on Twitter and LinkedIn
- Share product suggestions on the Azure Feedback Forum