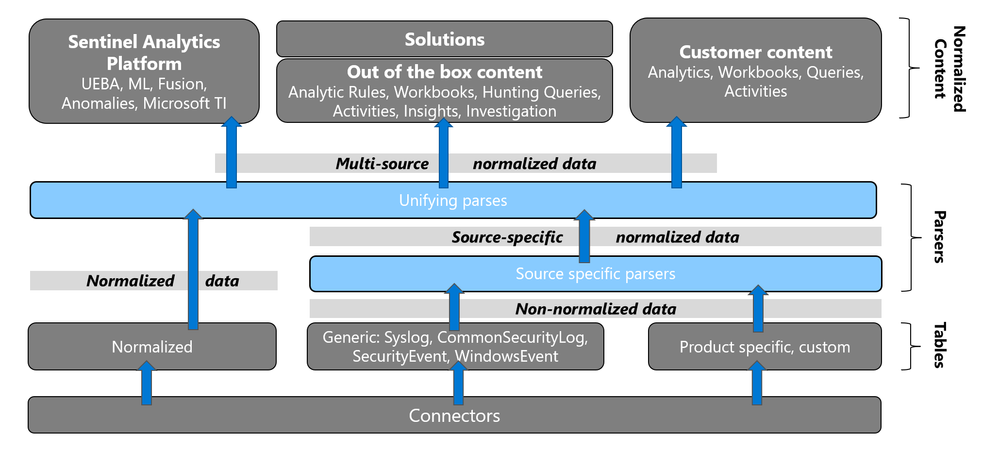
Normalization is at the core of every SIEM, and Microsoft Sentinel is no exception. The Advanced Security Information Model (ASIM) is Microsoft Sentinel's normalization engine. Until now, you had to deploy ASIM from Microsoft Sentinel's GitHub. Starting today, ASIM is built into Microsoft Sentinel. Once onboarding Microsoft Sentinel, you can immediately:
- Query normalized data.
- Use out-of-the-box normalized content such as analytic rules.
- Make sure the out-of-the-box content analyzes your unique event sources.
- Create your own normalized content.
Just use ASIM views such as _Im_Dns as your table names in a query and ensure you query all relevant normalized information in a consistent, well-documented, and easy-to-use schema.
To make ASIM part of Microsoft Sentinel, we had to double down on parsers' quality. To do that, we have created the ASIM tester, which we have used to test the built-in parsers, but you can also use it for your custom ASIM parsers. Interestingly, we found that the testing tools are great in evaluating the quality of the data you send to Microsoft Sentinel, not just the parsers. After all, even the best parser cannot convert partial or inaccurate data to gold.
Why normalization and ASIM?
Microsoft Sentinel ingests data from many sources. Working with various data types and tables together requires you to understand each of them and write and use unique data sets for analytics rules, workbooks, and hunting queries for each type or schema. Sometimes, you'll need separate rules, workbooks, and queries, even when data types share common elements, such as firewall devices. Correlating between different data types during an investigation and hunting can also be challenging.
ASIM provides a seamless experience for handling various sources in uniform, normalized views by providing the following functionality:
- Cross source detection. Normalized queries work across sources. For example, analytics rules can easily capture on-premises and cloud sources to detect attacks such as brute force or impossible travel across systems, including Okta, AWS, and Azure.
- Source agnostic content. The coverage of built-in and custom content using ASIM automatically expands to any source that supports ASIM, even if the source was added after the content was created. For example, process event analytics support any source that a customer may use to bring in the data, such as Microsoft Defender for Endpoint, Windows Events, and Sysmon.
- Support for your custom sources in built-in analytics
- Ease of use. Writing queries is much simpler after an analyst learns ASIM as the field names are always the same.
What is ASIM?
ASIM is a framework that provides normalization to Microsoft Sentinel. It includes the following parts:
- Normalized schemas cover standard sets of predictable event types that are easy to work with and build unified capabilities. The schema defines which fields should represent an event, a normalized column naming convention, and a standard format for the field values. Query writers and analysts save time by learning only an intuitive standard schema and creating queries that support multiple built-in and custom sources based on this schema.
- Parsers, or views, map existing data to the normalized schemas. Parsers are implemented using KQL functions.
- Normalized content, including analytics rules, workbooks, hunting queries, and additional content. This content works on any normalized data without creating source-specific content.
Posted at https://sl.advdat.com/3veNyTlhttps://sl.advdat.com/3veNyTl