Automation is a key facilitator for a SOC’s ability to save time and let the team focus on what matters most. Over the last year we have introduced a new Automation Rules platform which allows playbooks to run when incidents are created, for fast triage and response. We have also released 200+ playbook templates and exposed them in a new tab so you can start getting your value from automation as quickly as possible. But we know that not all of the automation scenarios can be fully automated and run behind the scenes. So we have added another to help you in these cases. This feature was already available for Logic Apps based on the Microsoft Sentinel Alert trigger, and now it’s being made available for those based on the Microsoft Sentinel Incident trigger as well.


Run playbooks as part of incident investigation and response
Automation rules are the best choice for handling those tasks which should happen when an incident is created, such as: quickly triaging incidents by identifying and closing false positives, reducing the incident queue noise; preparing your incident with enrichment results, to be ready for your analysts to investigate when they get to it; orchestrating the handling of the incident with other teams and systems; and/or immediately mitigating the threat of compromised entities with hard response actions such as resetting a user’s password or isolating an endpoint.
But teams usually prefer some tasks to be governed by human decision-making. For example, while investigating an incident, analysts may work with a list of remediation tasks. They might gather supporting information and correlate between multiple insights, leading them to take various actions at their discretion. Also, some SOCs would prefer their analysts to perform actions when needed, even if they can be fully automated, to keep the team hands-on.
With this feature, playbooks become a tool that can also be used for these manual steps. Every possible step of the investigation or remediation of an incident can be encapsulated each into its own playbook. These playbooks can be stored in a dedicated resource group which your analysts have access to (or you can give them access to individual playbooks independently ). While working on incidents, analysts can choose at any point to open the playbook side panel and launch a playbook from their list.
Microsoft Sentinel remembers the filters each user chooses for the playbooks list, so whenever an analyst comes back to it, they won’t have to filter again. Playbooks which are used most often can be marked as favorites. They will pop to the beginning of your playbooks list.
Test playbooks
Another important use case for this feature is allowing automation engineers to test the incident playbooks they develop for their SOC. For example, while creating a blank playbook, you may want to debug each step until development is completed, so you can sign off on it before attaching it to an automation rule or allowing analysts to run it on demand. When deploying a playbook template from the Templates tab or from the Content Hub, you may want to run the playbook to see how it really works on your incidents and make adjustments. The challenge is that incident playbooks require both the event trigger of a created incident and a real incident as the input, and until today both could be achieved only with the running of an automation rule. With this feature, you can now choose an incident that a playbook will be tested on and quickly pivot to the record of the playbook run to see how it went.
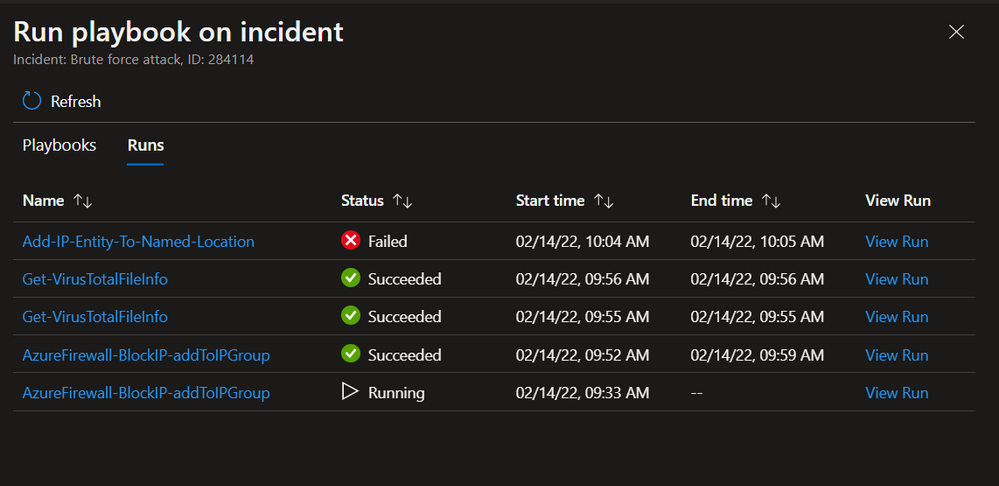
View run history
Whether for incident investigation and response or for testing use cases, after running a playbook you may want to quickly see the results of your on-demand run. When you run a playbook on demand, you will get a notification that the playbook run started successfully. The Runs tab then allows you to track the run status (ended with success or failure, or still running). You can quickly pivot to the full run log in Logic Apps. At the top of the playbooks side panel, the Runs tab shows a list of all the playbook runs on this incident: both from automation rules and on-demand launches.
Some teams configure their playbooks so that their final step makes a change which indicates that it ended successfully, such as writing a comment on the incident. Others will use Azure Monitor to alert when a playbook fails. This feature offers you another option: to quickly pivot to the Runs tab from within the incident context.
New API endpoint
We also introduced a new API endpoint for triggering a playbook. To use it you will need the incident and the playbook ARM ID. You can use it from any HTTP client as part of your scripts, and soon from Microsoft Sentinel PowerShell and CLI. This endpoint is available in our latest API version, with the header “2021-10-01-preview”.
Run playbooks from workbooks
Having an API endpoint for running playbooks also allows running playbooks directly from workbooks.
Permissions
Just as with automation rules, to run playbooks on-demand Microsoft Sentinel must be granted permissions to run playbooks.
The user who triggers the playbook needs to be able to view the Logic Apps workflows and trigger them. Currently the built-in role that grants these permissions is Logic Apps Contributor.
You can also create a custom RBAC role and add the following permissions to it:
- Microsoft.Logic/workflows/read
- Microsoft.Logic/workflows/triggers/listCallbackUrl/action
Learn more
- Run playbooks on demand
- Microsoft Sentinel SOAR (Orchestration, automation, and response)
- Automation rules
- Playbooks
- Customize playbooks from templates
- Authenticate playbooks to Microsoft Sentinel
- Use triggers and actions in playbooks
Posted at https://sl.advdat.com/3I7uzO6https://sl.advdat.com/3I7uzO6