Disclaimer
This document is not meant to replace any official documentation, including those found at docs.microsoft.com. Those documents are continually updated and maintained by Microsoft Corporation. If there is a discrepancy between this document and what you find in the Compliance User Interface (UI) or inside of a reference in docs.microsoft.com, you should always defer to that official documentation and contact your Microsoft Account team as needed. Links to the docs.microsoft.com data will be referenced both in the document steps as well as in the appendix.
All of the following steps should be done with test data, and where possible, testing should be performed in a test environment. Testing should never be performed against production data.
Target Audience
The Information Protection section of this blog series is aimed at Security and Compliance officers who need to properly label data, encrypt it where needed.
Document Scope
This document is meant to guide an administrator who is “net new” to Microsoft E5 Compliance through the following:
- Created a label that is required
- Publish a label that is required
It is presumed that you already have a Sensitive Information Type that you want to use in your Information Protection policy. For the purposes of this document, I will use a copy of the U.S. Social Security Number (SSN) called “U.S. SSN – Numbers Only” that I created in Part 1 of this blog series.
Out-of-Scope
This document does not cover any other aspect of Microsoft E5 Compliance, including:
- Sensitive Information Types
- Exact Data Matching
- Information Protection (creating a basic label)
- Data Protection Loss (DLP) for Exchange, OneDrive, Devices
- Microsoft Cloud App Security (MCAS)
- Records Management (retention and disposal)
- Overview of Advanced eDiscovery (AeD)
- Reports and Analytics available in of Advanced eDiscovery (AeD)
- Insider Risk Management
- Privacy Management
It is presumed that you have a pre-existing of understanding of what Microsoft E5 Compliance does and how to navigate the User Interface (UI).
It is also presumed you are using an existing Information Types (SIT) or a Exact Data Match (EDM) you have created for your testing.
Overview of Document
- Created a label that is required
- Publish a label that is required
Use Case
- You wish to require users to apply a Sensitivity label to a file/email. This could apply to any label, but we will do this for only one label in this blog. This is a manual process for the user
Definitions
- Sensitivity Label – a metadata tag
- Publish Label – making the metadata tag available to your tenant
- Required Label Policy – A policy that requires end users to apply a label to a new file/email before they can save or send it
Notes
- Required label policies are used when you want to do manual labeling of files/emails.
- Required labels are not the same things as Default labels. Required labels “force” users to apply a label to any a file/email before it can be saved or sent. On the other hand, Default labels, simply put, place a baseline Sensitivity label on all new files/emails. Default labels take the initial labeling if files/emails out of the hands of the end user and automate them.
- After a Sensitivity label is created and published, it should be visible within a few minutes, but can take up to 24 hours depending on what else is going on inside your test tenant.
Pre-requisites
- You have created a Sensitive Information Type (SIT) in Part 1 OR an Exact Data Match (EDM) in Part 1a of this blog series.
Create Required Label
We will now create our Required Label.
- Go to your Compliance console
- Navigate to your Information Protection -> Labels and click Create a Label.
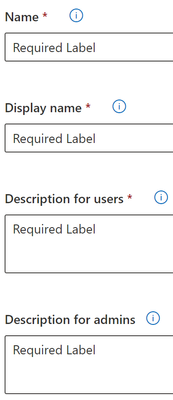
- Name & Description - Give the Label a name (ex. “Default Label”) and click Next.
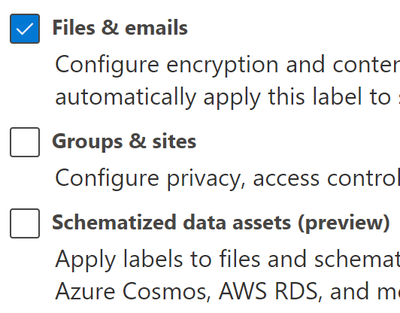
- Scope - Select only Files & emails and click Next.
- Files & Emails - File related settings will be disabled. Click Next.
- Under Choose Protection for settings for Files and Emails, check the box to Mark the content of files. Click Next.
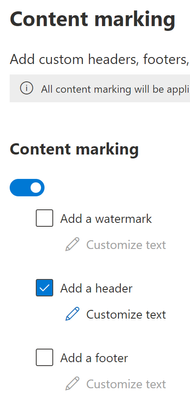
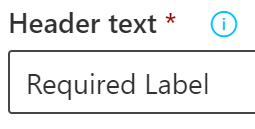
- On the next Content Marking, turn on Content marking and under a Watermark, select Add a header.
- For the custom text, enter the name “Required Label”.
- Click Save and then Next.
- You will now come to the section labeled Auto-labeling for files and emails. Accept the default of disabled and click Next.
- The next step in the wizard is Define protection settings for groups and sites. Since we are not working with groups of sites, this page will be disabled. Click Next.
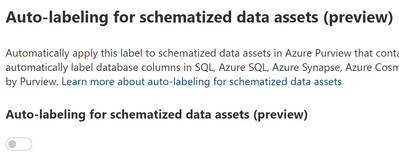
- Azure Purview (preview). This feature is not in General Availability yet. Lleave this disabled. Click Next.
- Now you will review your label settings.
- When you are satisfied, click Create Label.
Publish Required Label
Now we will publish our Required label.
- Click Publish Labels
- Select Choose Sensitive labels to publish and select your labels from above.
- Select your Required label and click Add. Then click Next.
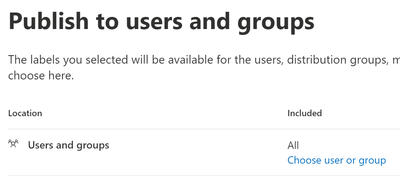
- Select which users and groups this will apply to. We will accept the default of All for this test. Click Next.
- For Policy Settings,
- First, select User must provide a justification to remove a label or lower its classification. As this option says, this will force the user to justify any future changes they might make to a label (required label or otherwise). This will also be logged as part of the activity.
- Second, select Require Uses to apply a label to their emails and documents. This will meet the goal of this blog to force users to add a Sensitivity label before they are able to save the file (whether this be a new file or an existing file that does not have a Sensitivity label.
- Click Next.
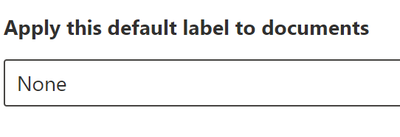
- Now you will arrive at Apply default label to documents. From the drop down, select the default of None and click Next.
- Now you will arrive at Apply default label to emails. From the drop down, select the None or same as Document. We will select None as we are not testing that at this time.
- Note – We will not be requiring users to apply a label to their emails at this time.
- Click Next.
- Now you will arrive at Apply default label to Power BI Content. Accept the default of None and click Next.
- Name and describe your policy.
- Now review the settings and when you are ready, click Submit.
- You have now published your Required label of use.
- Before proceeding to Testing this Required label, please wait up to 24 hours for the Label to be published into your test tenant. Note however, this could be as quick as an hour.
Testing
After waiting for the Default Label to be published, we can now test that it is applied to a new file. For our test here, we will use Microsoft Word.
- Open a Word document on your Windows test Tenant
- Create a new Blank Document
- Enter some data into the file and click Save (ex. (This is a Test File”)
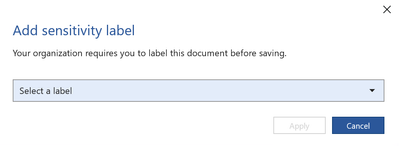
- You will see that you cannot save the file until a Sensitivity label is assigned. You will see a note similar to the one below before it allows you to finish saving the file.
- Note – This also stands true if you remove a label from a file and attempt to save it. You will see a note similar to this one.
- Note – if you have previously configured a default label policy (as in Part 2c of this Blog series), then this file will save because of that policy. If that is the case, for this test, remove that default label. You will then see a message similar to the one above.
- Select the Required Label from the dropdown and click Apply.
- You should see a Header in the file similar to the one below.
- You can now close the file
- You are now done with testing your Required Label.
Appendix and Links
- Learn about sensitivity labels - Microsoft 365 Compliance | Microsoft Docs
- Get started with sensitivity labels - Microsoft 365 Compliance | Microsoft Docs
- Automatically apply a sensitivity label to content in Microsoft 365 - Microsoft 365 Compliance | Microsoft Docs
- Manage sensitivity labels in Office apps - Microsoft 365 Compliance | Microsoft Docs
Posted at https://sl.advdat.com/3618BhMhttps://sl.advdat.com/3618BhM