With Salesforce’s recent requirement of enabling multi-factor authentication (MFA) to access Salesforce products, we wanted to share how Azure Active Directory can support you on this journey. With organizations supporting hybrid work and employees using a variety of applications to get work done, it’s critical to ensure access to these applications like Salesforce is protected.
Jonathon Lyon, Principal Program Manager, from our Identity Alliances team, will take you through just how you can meet Salesforce’s new requirements and ensure access to Salesforce products are protected.
--------------------
The old security paradigm of firewalls, silos, and passwords has left many organizations vulnerable during the ongoing shift to hybrid work. Threat actors - always quick to spot an opportunity - have noticed that identity is one of the fastest ways to break into a corporate network. Because of the plethora of stolen credentials littering the dark web, identity fraud (i.e., account takeover or business email compromise) has become the most common form of identity attack. As a recent security analysis sees it: “Identity remains the key for access into the network … There is no greater certainty that attacks on and with identities will increase in 2022.”*
Across all sectors, forward-thinking organizations have recognized that Zero Trust security is the best approach for quickly detecting and responding to threats in today’s borderless digital estate. With Zero Trust in mind, Salesforce has announced that beginning February 1, 2022, the company will now require all customers to enable multi-factor authentication (MFA) to access Salesforce products. As part of Microsoft’s mission to enable security for all, we’re happy to help Salesforce customers make MFA and single sign-on (SSO) easy using Microsoft Azure Active Directory (Azure AD).
The problem with passwords
With more than 150,000 customers and a market cap surpassing $200 billion, Salesforce isn’t about to take chances with security. The risks are too great for a major cloud company, or any business, to rely on an employee’s choice of a few digits and letters to protect an entire enterprise. Passwords are easily hacked. The ransomware attack against JBS USA was enabled by just such a breach—a neglected admin account left to linger with a weak password—that ended up costing the company $11 million. These kinds of “brute force” attacks rose 671 percent in June of 2021. In fact, Azure AD detected and blocked more than 25.6 billion attempts to hijack enterprise customer accounts by brute-forcing stolen passwords between January and December 2021.
Microsoft provided a way out of the password trap in 2021 by making passwordless sign-in generally available for commercial users. That means Microsoft customers can now completely remove the password from their account, and instead sign in using:
- Microsoft Authenticator app—turns any iOS or Android phone into a strong passwordless credential. Users can sign into any platform or browser by getting a notification to their phone, matching a number displayed on the screen. They can then use their biometric (finger or face) or PIN to confirm. Recent updates make it easier to add or manage enterprise accounts.
- Windows Hello for Business—uses biometric and PIN credentials directly tied to the user's PC, which prevents access from anyone other than the owner. With public key infrastructure (PKI) integration and built-in support for SSO, Windows Hello for Business provides a convenient method for seamlessly accessing corporate resources both on premises and in the cloud.
- FIDO2 security key—provides SSO for cloud or on-premises resources, as well as supported browsers. FIDO2 security keys are a great option for enterprises who may have employees who aren't willing or able to use their phone as a second factor.
Use Azure AD to implement multi-factor authentication
MFA is proven to prevent 99.9 percent of identity-related attacks. Despite this, only 22 percent of Azure AD customers had already implemented MFA by the end of 2021. As the engine of MFA, Conditional Access is built directly into Azure AD as the heart of our identity-driven control plane, bringing signals together to enable lightning-fast enforcement of your organizational policies.
Microsoft customers can use Azure AD to authenticate into Salesforce or any other application by choosing from a range of flexible authentication methods, such as biometrics, the Authenticator app, texts, calls, or one-time passcodes. (Note: Salesforce does not allow SMS or phone verification because voice and text are the least secure.) When you integrate Azure AD with Salesforce for SSO and MFA, you can:
- Use Azure AD to control who has access to Salesforce.
- Enable users to sign into Salesforce automatically using their Azure AD accounts.
- Manage both accounts in one central location—the Microsoft Azure portal.
- Create a Conditional Access Rule that enforces MFA on the Salesforce application.
To learn more about enabling MFA in Azure AD, see the complete tutorial.
Salesforce multi-factor authentication—the process
After the requirement deadline (dates vary by product), Salesforce will begin enforcement by removing controls for admins to disable MFA according to the company’s Enforcement Roadmap. At present, Salesforce is only enforcing the new requirement contractually. Meaning, customers who don’t enable MFA won’t be able to renew their agreements. Technical enforcement may come later.
To satisfy the new requirement, Salesforce customers must do one of the following:
- Enable MFA through the Salesforce user interface, or…
- Use federated SSO to access Salesforce products. Azure AD can automatically authorize users into Salesforce and many other apps (see quick steps for enabling MFA in Salesforce below).
Customers can also use the Salesforce MFA Requirement Checker to make sure their implementation meets the company’s requirements. Also, learn about authentication and verification methods available in Azure AD.
In the following steps, we’ll walk through creating a Conditional Access Policy that enforces MFA for your Salesforce users.
- Sign in to the Azure portal as an existing Global Administrator.
- Browse to Azure Active Directory and under Manage, select Security.
- Select Conditional Access.
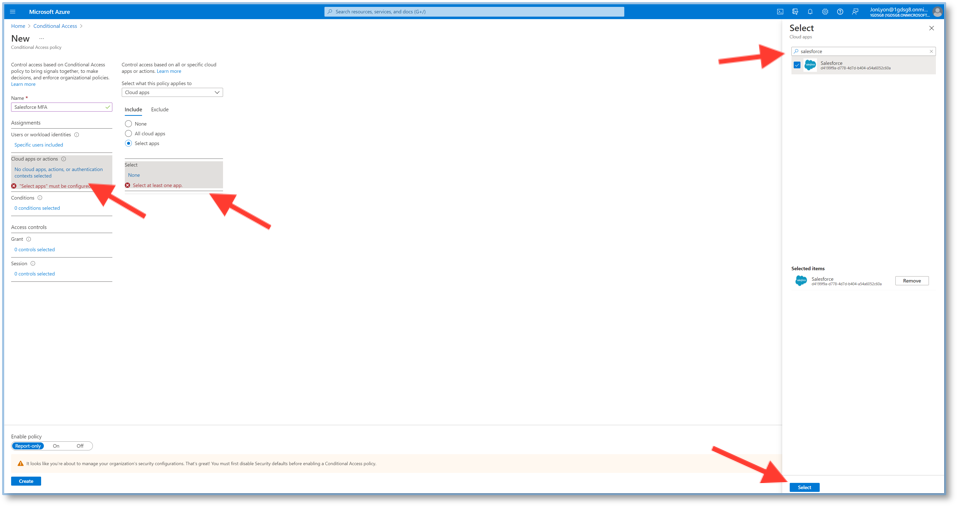
4. Click New Policy, then select Create New Policy.
5. Enter a name for your policy.
7. Under Assignments, select Users or workloads identities.
8. Choose Select users and Groups. Next, select which users, or a group of users, that use Salesforce. Once you’ve selected the users or groups you want, click select.
9. Select Cloud apps or actions.
10. Choose the Select apps option, then search for Salesforce. Click Select. (You could specify some conditions if you wanted, but for this example we will leave the conditions.)
11. Under Access Controls, select Grant.
12. Select Grant Access and tick the Require multi-factor authentication option. Then click Select.
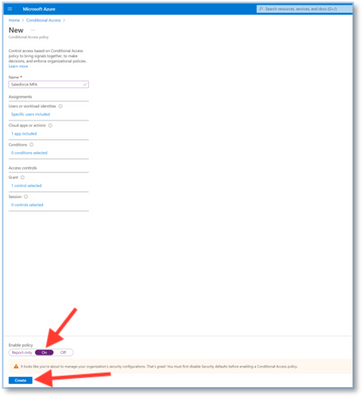
The last step is to enable the policy.
13. Change the option from Report-Only to On. Then click Create.
This rule will now take effect, and all selected users will now use MFA every time they sign into Salesforce.
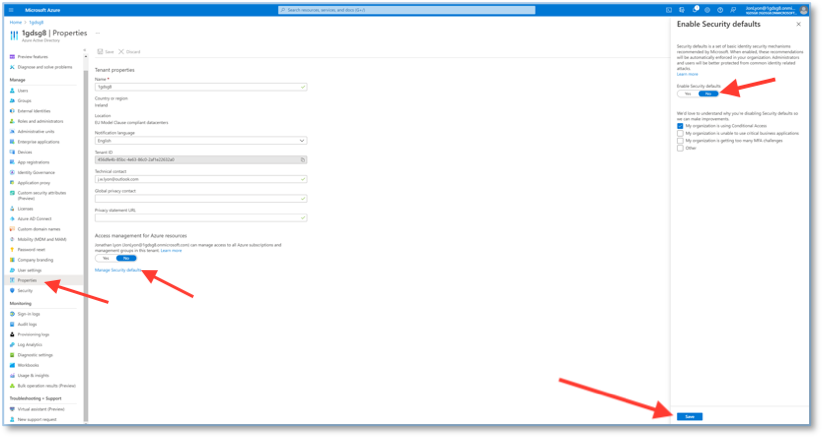
Note: If this is your first Conditional Access Policy, you may get the message shown below.
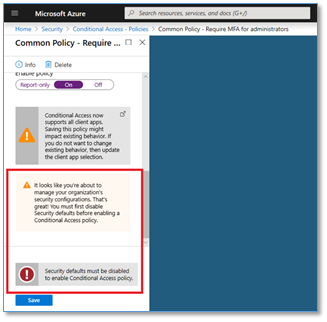
To disable security defaults in your directory:
- Sign in to the Azure portal as a security administrator, Conditional Access administrator, or global administrator.
- Browse to Azure Active Directory > Properties.
- Select Manage security defaults.
- Set Enable Security defaults to No.
- Select Save.
One sign-on for all your apps
Azure AD enables more than frictionless MFA. You’ll benefit from secure, seamless access for all your users from any location or device, including:
- Simplified app deployment with a centralized user portal.
- Strong enforcement of risk-based access policies with identity protection and Conditional Access.
- Automated provisioning workflows and self-service tools to help reduce IT costs.
Azure AD provides easy integration with other widely used apps, including Adobe, AWS, Dropbox, SAP Concur, ServiceNow, and many more. Learn how you can enjoy simple, secure MFA across Salesforce and many more of your enterprise apps—access reliable, scalable identity services with Azure Active Directory single sign-on.
*Security Week, Cyber Insights 2022: Identity
Learn more about Microsoft identity:
- Return to the Azure Active Directory Identity blog home
- Join the conversation on Twitter and LinkedIn
- Share product suggestions on the Azure Feedback Forum