This article contributed by Linda Murray and Amy McAuley, Assc Consultants in Azure Cloud and AI at Microsoft.
You can now connect AWS accounts to Microsoft Defender for Cloud, to get a unified multi-cloud view of your organization's security posture. Specifically, AWS Security Hub detected misconfigurations and findings are now included in our Secure Score Model and Regulatory Compliance Experience.
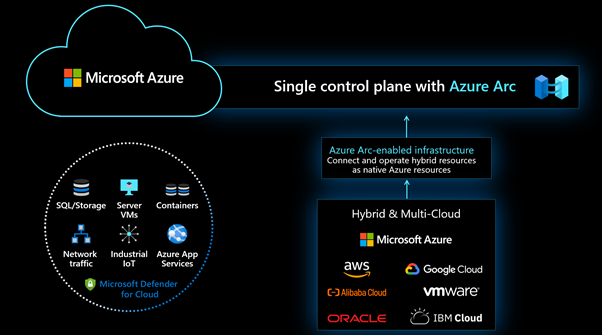
Defender for Cloud leverages Azure Arc to simplify the on-boarding and security of virtual machines running in AWS and other clouds. This includes automatic agent provisioning, policy management, vulnerability management, embedded EDR, and much more. The below image shows the different hybrid and multi-cloud options and the capabilities they have when they are connected as Azure Arc enabled infrastructure:
Required roles and permissions for the AWS connector
Azure - The Owner role of the relevant Azure subscription is required. The Contributor role can also connect an AWS account if an owner provides the service principal details (required for the Defender for Servers plan).
AWS - To create the stack in AWS you need the appropriate permissions to create IAM roles.
AWS connector pre-requisites
Before enabling the AWS connector in Azure, check that you have the following pre-requisites in place:
1. AWS account
To connect an AWS account to your Azure subscription, you'll need access to an AWS account.
2. Microsoft Defender for Servers enabled
Visit Quickstart: Enable enhanced security features for details.
3. EC2 Instances require management by AWS Systems Manager
An active AWS account with EC2 instances managed by AWS Systems Manager (SSM) and using SSM agent. Some Amazon Machine Images (AMIs) have the SSM agent pre-installed, their AMIs are listed in AMIs with SSM Agent preinstalled.
If your EC2 instances don't have the SSM Agent, follow the relevant instructions from Amazon:
Install SSM Agent for a hybrid environment (Windows)
Install SSM Agent for a hybrid environment (Linux)
4. Setting up AWS Systems Manager
- Stop (shut down) your AWS machine.
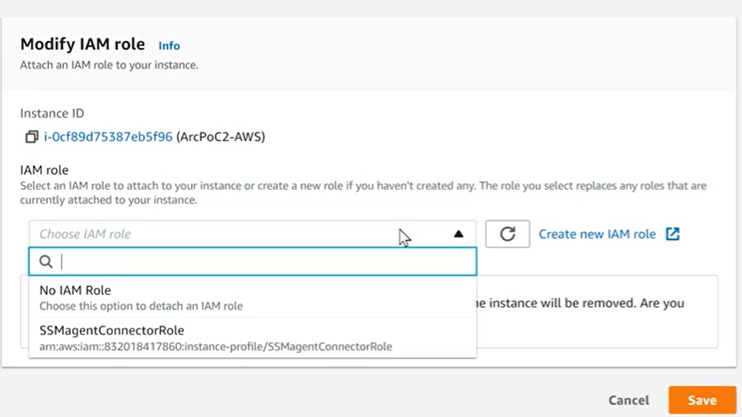
- Look in Security tab to see If there is an IAM role. If it's empty, then you need to create one. Go to actions > security > modify IAM role.
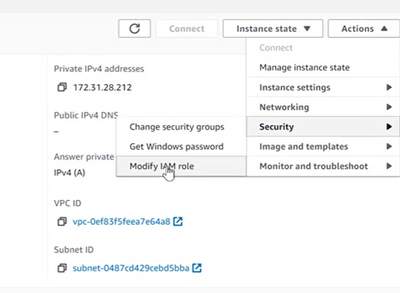
- Choose an IAM role. If you do not have one then create one by selecting the box on the blue text on the right, Create new IAM role.
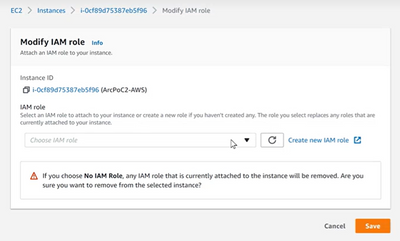
- This will bring you to a new page. Select Create role. Choose a use case, choose EC2.
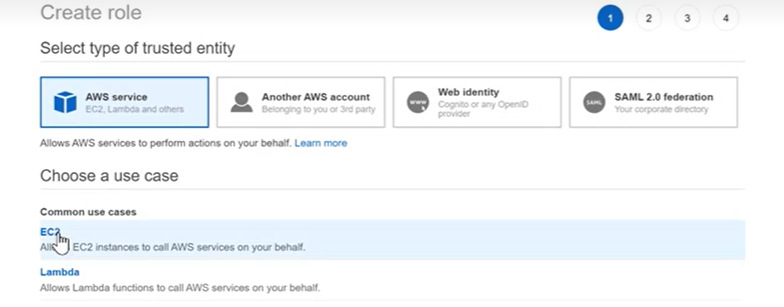
- In the Filter policies box, enter the search word core.
- Choose AmazonSSMManagedInstanceCore, select Next: tags and Next: Review. Create this role by giving it a name and when finished select create role.
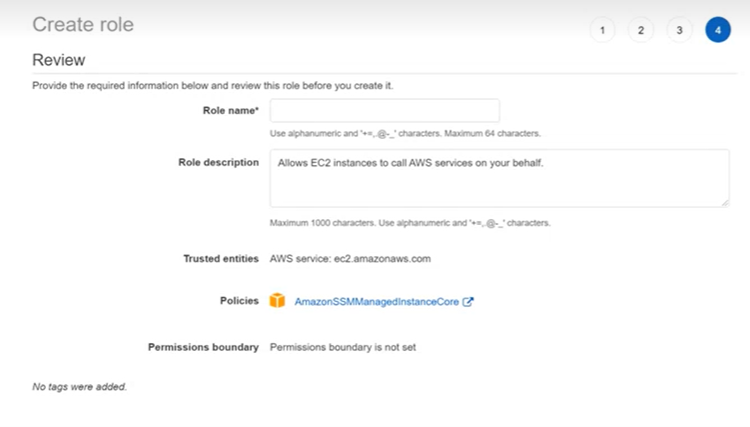
- Go back to Modify IAM role under the machine instance and select your newly created IAM role and select save to assign it to the machine.
- Now you need to click on instance state and start the machine.
In the security tab under the machine instance information on AWS, the IAM role should now be listed. This allows it to connect to the SSM agent, which allows the deployment of the auto provisioning piece from Azure.
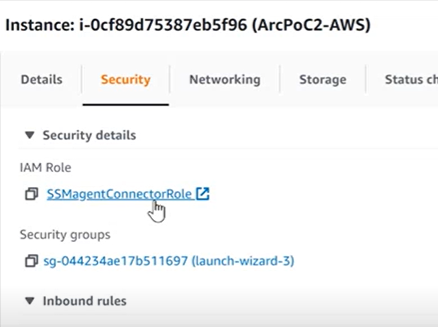
- This should then appear in Fleet Manager in AWS. The machine can take up to 3 hours to onboard to Azure Arc.
Note: The Azure Arc Product Group are working on automation for Microsoft Defender for Cloud to attach the required IAM role for SSM to work. We can also use AWS Quick setup wizard under System Manager console.
Enable the AWS cloud connector
1. Ensure you already have a Log Analytics workspace enabled (Default or Custom) and Auto-provisioning enabled at the subscription level.
2. From Defender for Cloud's menu, open Environment settings.
3. Select Add environment > Amazon Web Services.
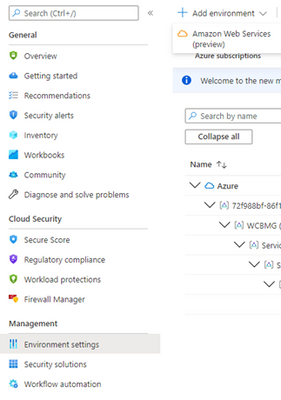
4. Enter the details of the AWS account:
- Connector name: give the connector a name
- Onboard: choose a ‘Single account’ or ‘Management account’
- Subscription: choose an Azure subscription
- Resource Group: choose a resource group
- Location: choose where you'll store the connector resource, same as AWS account.
- AWS Account ID: enter AWS account ID (You will need to retrieve this from your AWS account)

5. Select Next: Select plans.
6. The select plans tab is where you choose which Defender for Cloud capabilities to enable for this AWS account.
7. To extend Defender for Servers coverage to your AWS EC2, set the Servers plan to On.
8. Choose configure under the configurations tab and turn on:
- Azure Arc agent
- Log Analytics agent
- Microsoft Defender for Endpoint agent
9. Select Save.

10. Optional: You can also select the Standards (Preview) tab to apply AWS standards as well as apply custom standards. This option can also be configured later.
11. Select Next: Configure access.
12. Download the CloudFormation template.
13. Copy the service principal secret and keep in a safe place.
14. Choose Go to AWS to log into your AWS account.
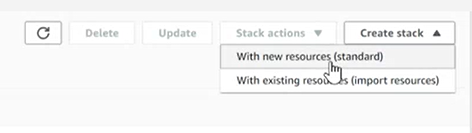
15. Select Create stack> with new resources (standard).
16. Under Prerequisite- Prepare template ensure that the Template is ready option is selected.
17. Under Specify template, choose Upload a template file.
18. Select choose file and upload the downloaded CloudFormation template.
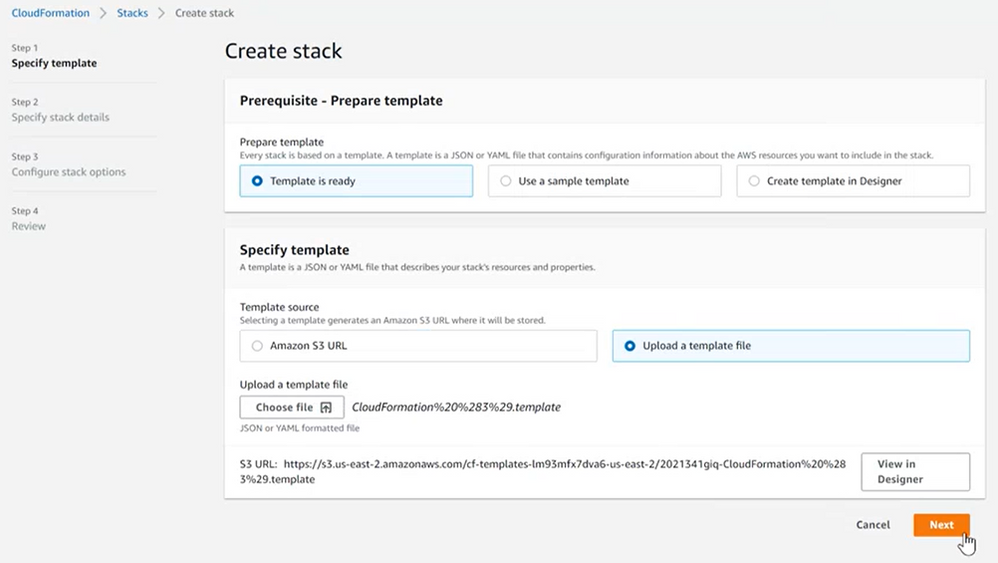
19. Choose Next.
20. Enter the Stack name.
21. Under the ArcAutoProvisioningServicePrincipalSecret parameter enter the service principal that you copied from the Azure portal earlier.
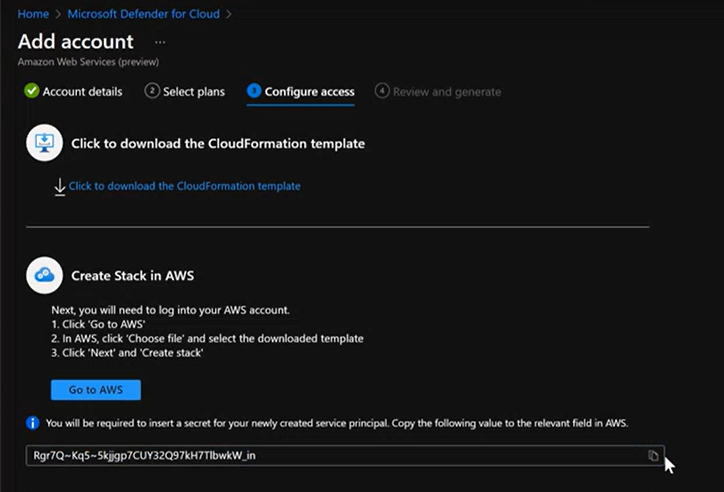

Note: Make sure to enter the Service Principal secret. Not to be confused with the Secret Name. The auto provisioning secret name is not what is needed here.
22. Choose Next.
23. Configure stack options if needed, or leave as default.
24. Choose Next.
25. Ensure you tick The Template has changed acknowledgement.
26. Select Create stack.
Defender for Cloud will immediately start scanning your AWS resources and you'll see security recommendations within a few hours.
Assign AWS standards
You can apply new standards by selecting a matrix of pre-existing AWS assessments by:
1. From Defender for Cloud's menu, open Environment settings.
2. Select the newly created connector.
3. Select the Standards (preview) tab.
4. Here you can see the built in and custom standards which are applied to your AWS account.

6. To assign a new standard, click Assign standard > Enter Name & Description > Choose Assessments from the list > click Create.
Note: These are pre-existing CSPM AWS assessments that you define against the standard.
Create custom AWS assessments
When the pre-existing AWS assessments do not meet your requirements, you can create your own custom assessments by:
1. From Defender for Cloud's menu, open Environment settings.
2. Choose the newly created connector.
3. Select the Standards (preview) tab.
4. Click Create assessment.
5. Enter a Name.
6. Choose the severity > low, medium or high.
7. Enter a Description.
8. Enter a Remediation description.
9. Choose the Standard you want to apply this assessment to.
10. Then in the query section, create a new query or customise an existing query with Azure Data Explorer. You can select Launch Data Explorer link to navigate to Azure Data explorer.
Note: Here you are applying a Kusto query onto data gathered from the Arc agent and the log analytics agent to query in the context of the resources in AWS. You can define a query and it's going to find resources that are conforming or not to that query. This enables you to make your CSPM definitions whatever you want them to be.
Required roles and permissions: View and apply Microsoft Defender alerts and recommendations to AWS resources.
Security Reader, Security Admin, Reader, Contributor, or Owner role at the Resource Group level is required to View Microsoft Defender alerts and recommendations.
To apply recommendations from Microsoft Defender for Cloud, the Contributor or Owner role is required at the Resource Group level.
Next steps
Connecting your AWS account is part of the multi-cloud experience available in Microsoft Defender for Cloud. To learn more, visit:
Security recommendations for AWS resources - a reference guide
Connect your GCP accounts to Microsoft Defender for Cloud
Posted at https://sl.advdat.com/3IZzEbzhttps://sl.advdat.com/3IZzEbz
