Welcome to part 2 of the 4-part blog series Helping Federal organizations achieve CDM requirements for What is on the Network – software asset management (SWAM).
The previous post Part 1 (HWAM) can be found here Helping Federal organizations achieve CDM requirements Part 1 of 4 – What is on the Network (HWAM) - Microsoft Tech Community
Modern software can be complex consisting of many components that can expose organizations to vulnerabilities and risk. The recent Log4j vulnerability exposed the breath of how software components can be used to exploit applications. This seemingly impossible task of understanding what software is installed on an organization’s network can be challenging.
Like hardware asset management (HWAM)HWAM; SWAM is about the identification of software installed on an organization’s infrastructure. Blog post 3 will cover the vulnerability aspect of CDM.
More information about SWAM can be found here CDM Software Asset Management (SWAM) Capability (cisa.gov)
Software Asset Management (SWAM)
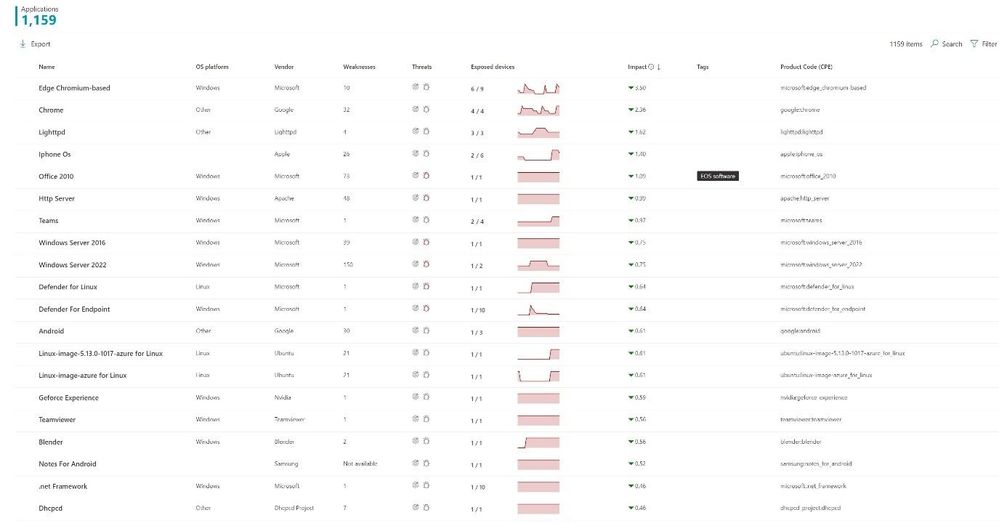
In 2019 Microsoft added Threat and Vulnerability Management (TVM) into Microsoft Defender for Endpoint (MDE) and eventually integrated this into Microsoft Defender for Cloud. TVM can help organizations collect data for two parts of CDM. The first, SWAM is obtained by MDE continuously communicating with endpoints to provide a list of installed software on those devices. In the MDE UI under Threat & Vulnerability Management there is a Software Inventory section. Software inventory produces an enterprise view of software installed on each Windows, Mac, IOS, Android or Linux device.
Figure 8: MDE Software Inventory
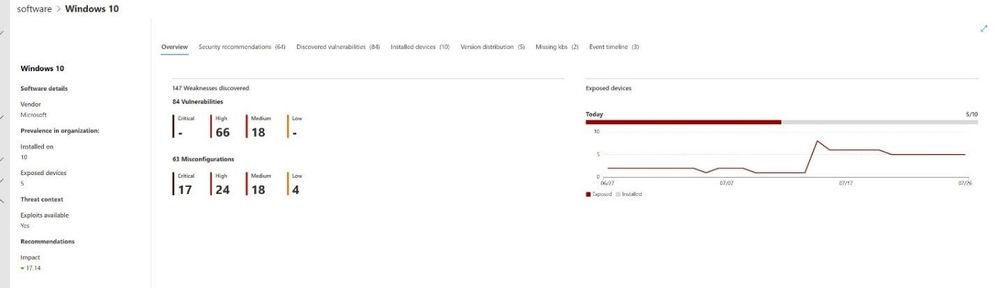
Selecting an item from the software inventory will drill down into several pieces of additional information to include the various versions and any security recommendations. The overview tab provides an “at a glance” look across your organization, the number of devices exposed, number of vulnerabilities, and various other data sets. By moving across each tab, security teams can quickly gain a better understanding of security recommendations, discovered vulnerabilities, and how many devices the software is installed on.
Figure 9: MDE Software Page
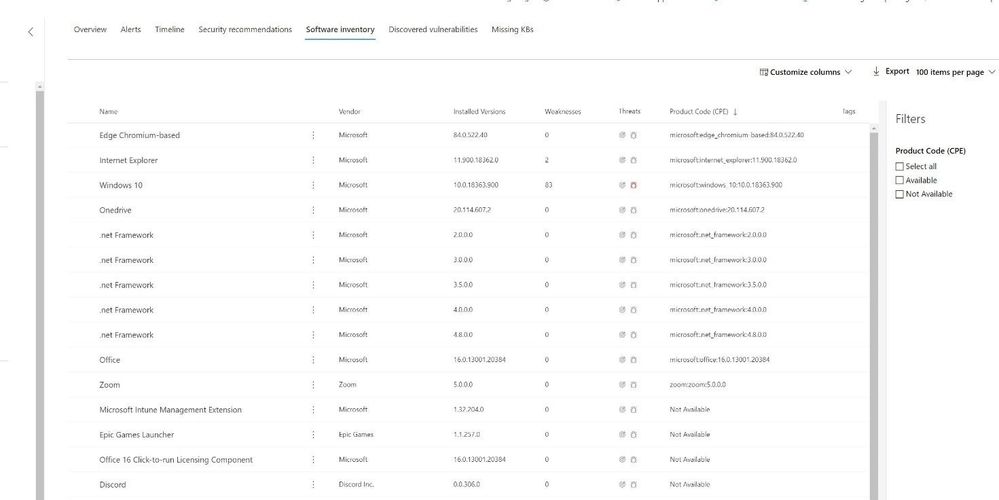
Software inventory is also displayed on each computer object. This provides a list of software installed on a per machine view. The machine view produces several pieces of data helping staff to quickly identify the software installed on a device, the vendor, version information, any known weaknesses, and if any active threats are occurring against the software.
Figure 10: MDE Software Inventory Device view
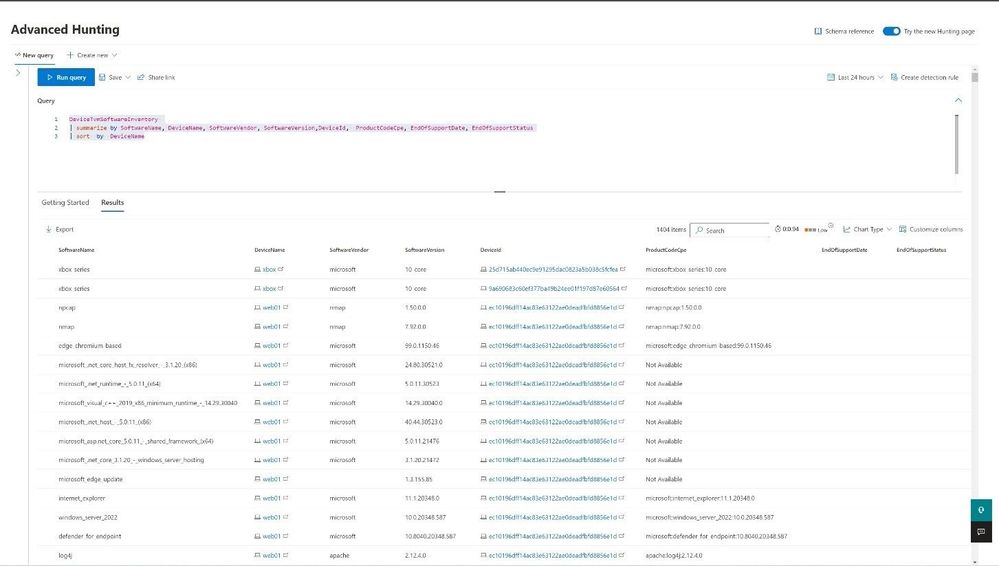
Graphical representation is a nice way for IT staff to get a quick look at information however, for more advanced actions IT teams would use the Advanced hunting capability of MDE. Advanced hunting uses the powerful Kusto Query Language (KQL) to hunt/query data stored in MDE. MDE stores the software inventory data in the DeviceTVMSoftwareInventory table. Advanced hunting help IT teams search for software across their organization and perform advanced analytics by joining various data sets together.
Figure 11: Software Inventory Advance Hunting
Advanced Hunting and API
MDE provides several methods to access data. This can be done graphically in the interface, using the KQL query language, or via an API.
The Defender for Endpoint APIs can be grouped into three:
- Microsoft Defender for Endpoint APIs
- Raw data streaming API
- SIEM integration
Figure 23: MDE APIs
Microsoft Defender for Endpoint API is a multi-layered API that has two subcategories:
- Response API
- Investigation API
To help organizations learn how to use the API’s the built-in API explorer provides an interface to test the syntax. Once the syntax has been validated staff can use the MDE API interface to push and pull data from the platform or integrate with other tools, such as SOAR application(s), to automate tasks or automate incident and response actions.
In some cases, additional data is exposed via the API calls that may not be present in the Advanced hunting tables.
Figure 24: MDE example API call
Advanced Hunting
MDE provides several tables that provide a quick interface for staff to “hunt” across all the data stored within the platform. MDE stores 30 days of data in the hunting tables and 6 months of machine timeline history on each node.
Each table hosts a set of data that can be examined via KQL. KQL is a powerful language that is standardized across several solutions in the Microsoft ecosystem. Since MDE data for each category is stored in these tables, staff can search a single place for software, vulnerabilities, configuration baselines, and many other events captured by MDE. This helps reduce the complexity of bringing data in from multiple sources.
Figure 25: MDE Advanced Hunting Tables
Additional Training
Become a Microsoft Defender for Endpoint Ninja - Microsoft Tech Community
Posted at https://sl.advdat.com/3MkDcqshttps://sl.advdat.com/3MkDcqs